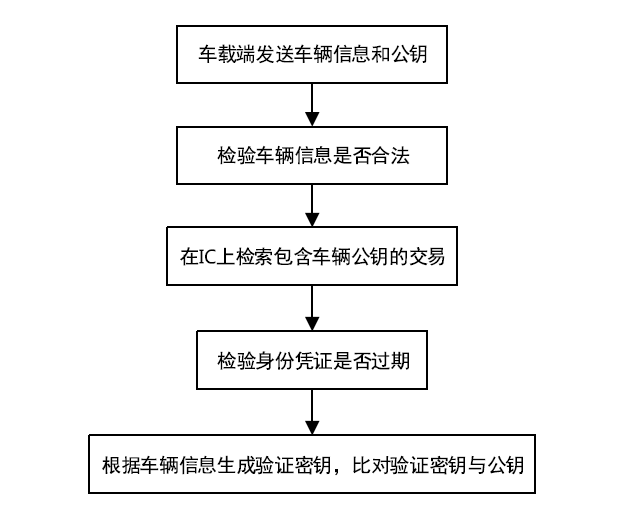
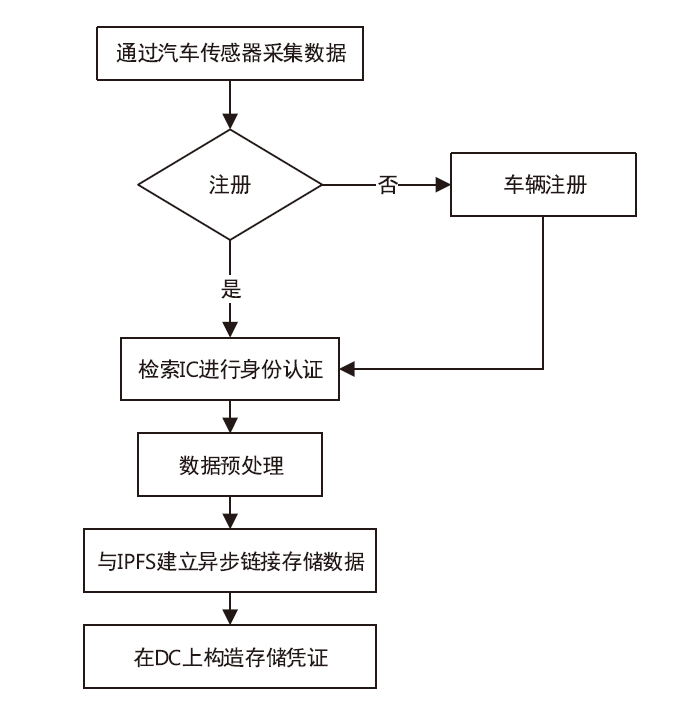
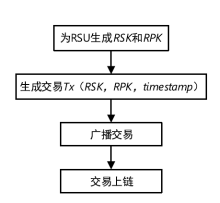
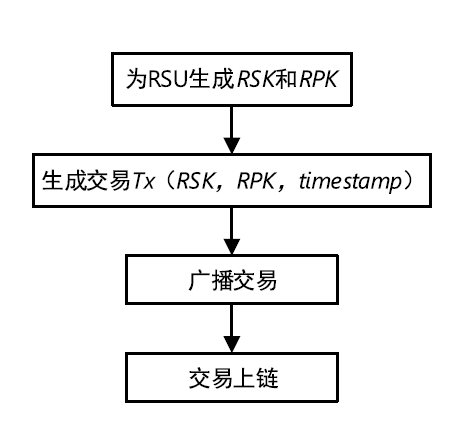
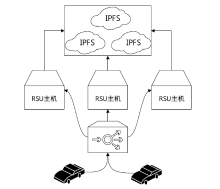
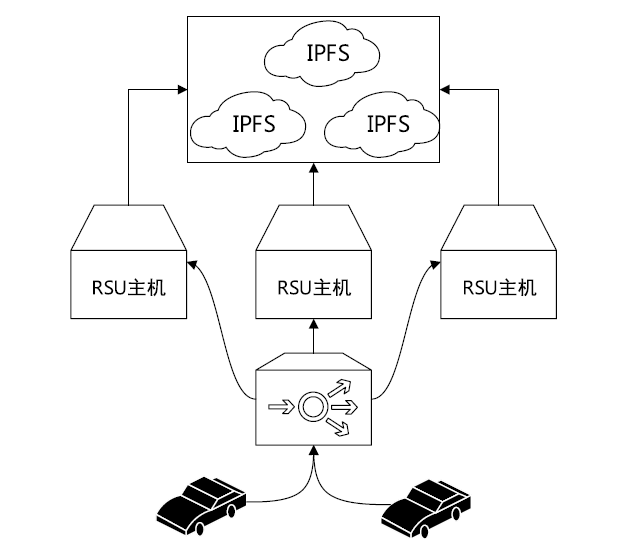
Netinfo Security ›› 2022, Vol. 22 ›› Issue (8): 26-35.doi: 10.3969/j.issn.1671-1122.2022.08.004
Previous Articles Next Articles
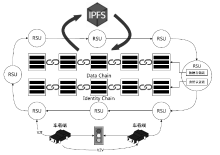
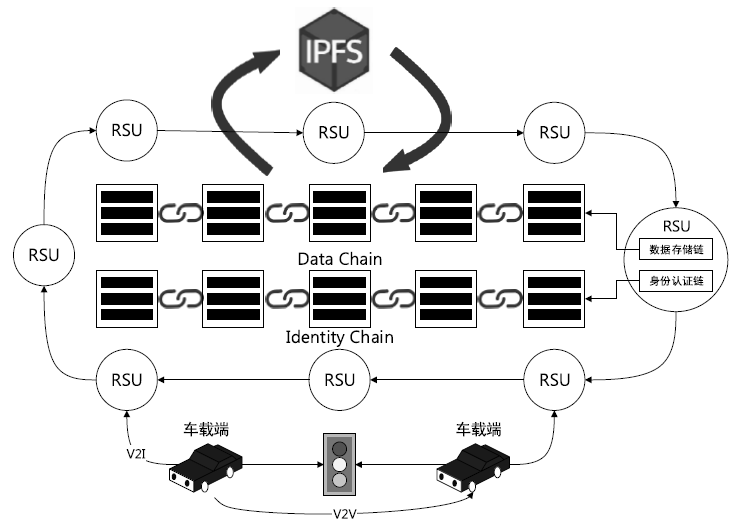
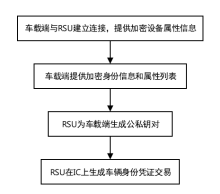
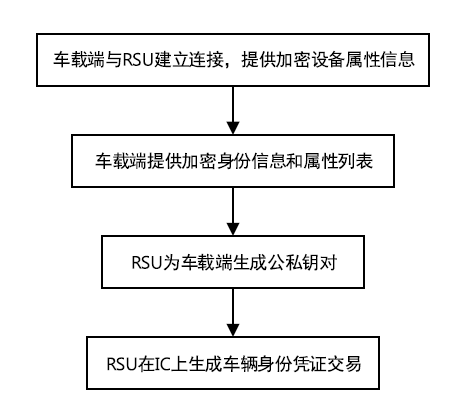
Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System
- School of Information and Software Engineering, University of Electronic Science and Technology of China, Chengdu 610054, China
-
Received:2022-03-23Online:2022-08-10Published:2022-09-15 -
Contact:SHE Kun E-mail:kunshe@126.com
CLC Number:
Cite this article
HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System[J]. Netinfo Security, 2022, 22(8): 26-35.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.08.004
| [1] | LIU Yang, WANG Shuo, GAO Hongwei. Overview of Global V2X Technology Progress-A review of the 5th SIP-Adus Conference(SIP-adus Workshop 2018) on Telematics[J]. Automotive Digest, 2019(3): 20-23. |
| 刘阳, 王硕, 高洪伟. 全球V2X技术进展概述—第5届SIP-Adus大会 (SIP-Adus Workshop 2018)车联网综述[J]. 汽车文摘, 2019(3): 20-23. | |
| [2] | WANG Xuejin, LIU Jing, AN Xiaojiang. A Review of Information Security Research in Vehicle Networking[J]. Transportation Technology and Management, 2021(2): 123-126. |
| 王学进, 柳晶, 安晓江. 车联网信息安全研究综述[J]. 交通科技与管理, 2021(2): 123-126. | |
| [3] | ZHANG Haibo, CHENG Yan, LIU Kaijian, et al. Mobility Management Strategies for Integrating Mobile Edge Computing and Content Delivery Networks in Vehicular Networking[J]. Journal of Electronics and Information, 2020, 42(6): 1444-1451. |
| 张海波, 程妍, 刘开健, 等. 车联网中整合移动边缘计算与内容分发网络的移动性管理策略[J]. 电子与信息学报, 2020, 42(6): 1444-1451. | |
| [4] |
FEANC O, CICIRELL I, ANTONI O, et al. Edge Computing and Social Internet of Things for Large-Scale Smart Environments Development[J]. IEEE Internet of Things Journal, 2017, 5(4): 2557-2571.
doi: 10.1109/JIOT.2017.2775739 URL |
| [5] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-11-1)[2022-02-17]. https://bitcoin.org/bitcoin.pdf. |
| [6] |
KANO Y, NAKAJIMA T. A Novel Approach to Solve a Mining Work Centralization Problem in Blockchain Technologies[J]. International Journal of Pervasive Computing and Communications, 2018, 14(1): 15-32.
doi: 10.1108/IJPCC-D-18-00005 URL |
| [7] |
TUSHAR W, SAHA T K, YUEN C, et al. Peer-to-Peer Trading in Electricity Networks: An Overview[J]. IEEE Transactions on Smart Grid, 2020, 11(4): 3185-3200.
doi: 10.1109/TSG.2020.2969657 URL |
| [8] | CHRISTIDIS K, DEVETSIKIOTIS M. Blockchains and Smart Contracts for the Internet of Things[J]. IEEE Access, 2016(4): 2292-2303. |
| [9] | ALI O, JARADAT A, KULAKLI A, et al. A Comparative Study: Blockchain Technology Utilization Benefits, Challenges and Functionalities[J]. IEEE, 2021(9): 12730-12749. |
| [10] | YANG Qing, WANG Hao. Privacy-Preserving Transactive Energy Management for IoT-Aided Smart Homes via Blockchain[J]. IEEE Internet of Things Journal, 2021, 8(14): 1-13. |
| [11] | ZHANG Xiaohong, CHEN Xiaofeng. Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad-Hoc Network[J]. IEEE, 2019, 7: 58241-58254. |
| [12] | KOUICEM D E, BOUABDALLAH A, LAKHLEF H. An Efficient and Anonymous Blockchain-Based Data Sharing Scheme for Vehicular Networks[C]// IEEE. 2020 IEEE Symposium on Computers and Communications(ISCC). New York: IEEE, 2020: 1-6. |
| [13] | STD I. IEEE Trial-Use Standard for Wireless Access in Vehicular Environments(WAVE)- Multi-Channel Operation[J]. IEEE, 2006(1): 71-82. |
| [14] | SALEM A H, ABDEL H A, ELNASR M A. The Case for Dynamic Key Distribution for PKI-Based VANETs[J]. International Journal of Communication Networks and Distributed Systems, 2014, 6(1): 61-78. |
| [15] |
HENG C, TAN N, MAOD E, et al. A Secure and Authenticated Key Management Protocol(SA-KMP) for Vehicular Networks[J]. IEEE Transactions on Vehicular Technology, 2016, 65(12): 9570-9584.
doi: 10.1109/TVT.2016.2621354 URL |
| [1] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [2] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [3] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [4] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [5] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [6] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [7] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [8] | LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit [J]. Netinfo Security, 2022, 23(3): 53-61. |
| [9] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [10] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [11] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [12] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [13] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| [14] | FENG Jingyu, WANG Tao, YU Tingting, ZHANG Wenbo. A Secure Medical Data Sharing Scheme Based on Multi-clouds and Multi-chains Collaboration [J]. Netinfo Security, 2022, 22(1): 9-18. |
| [15] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||