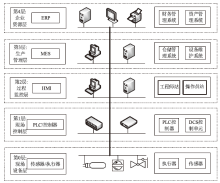
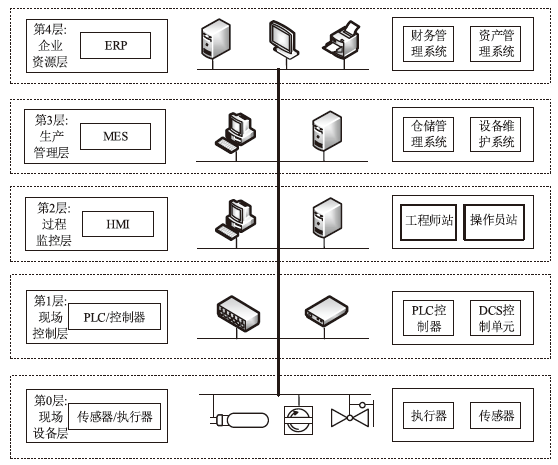
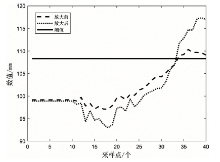
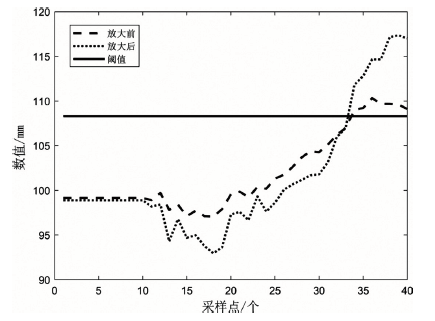
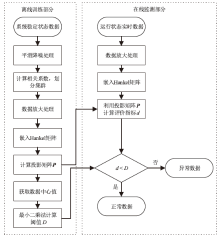
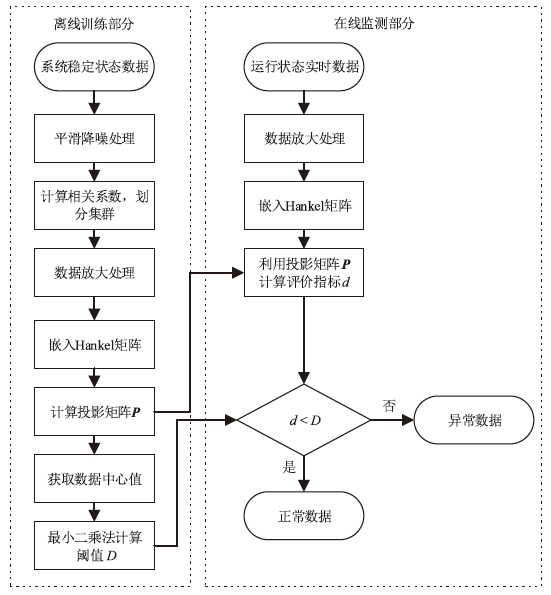
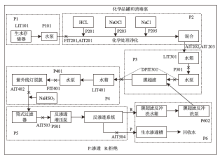
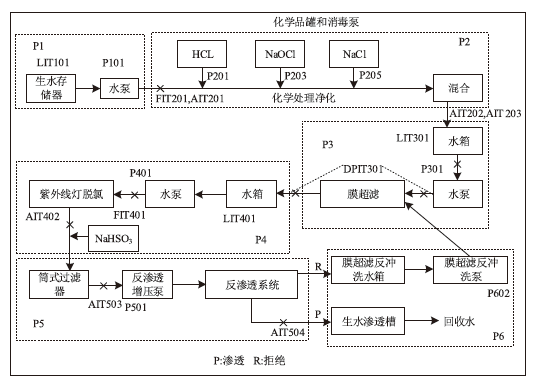
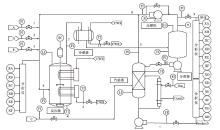
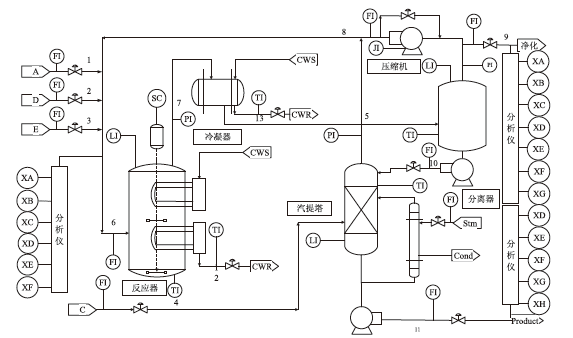
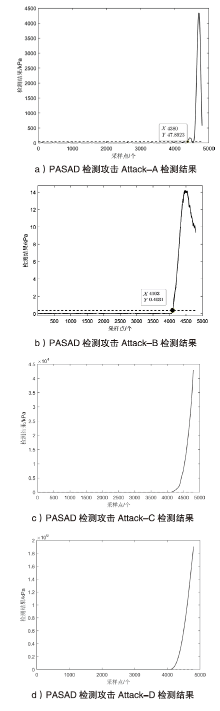
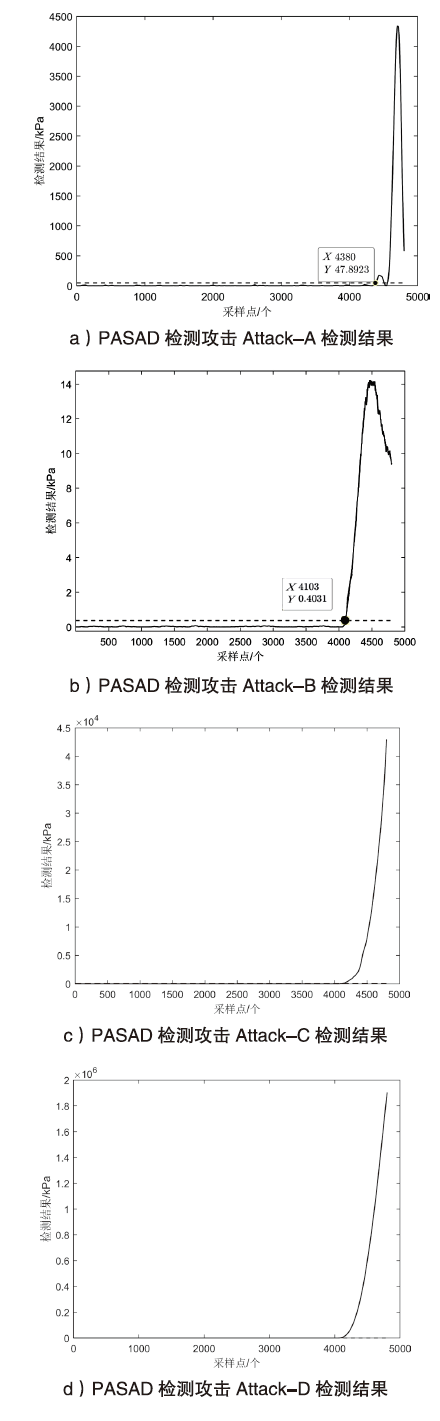
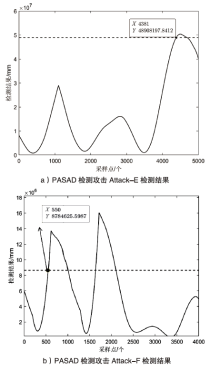
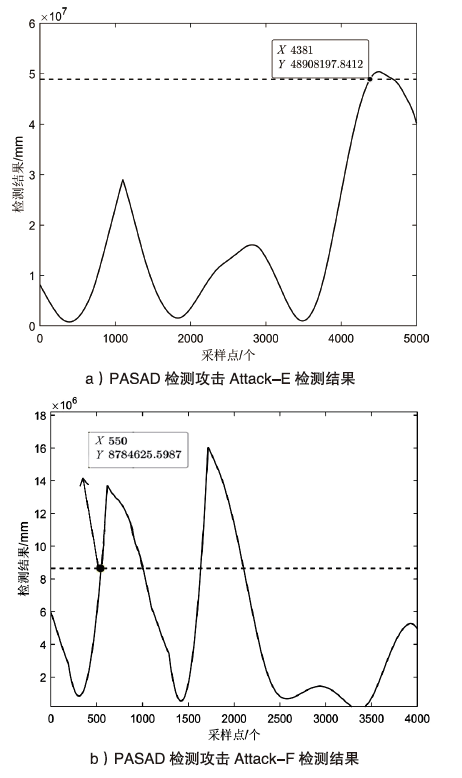
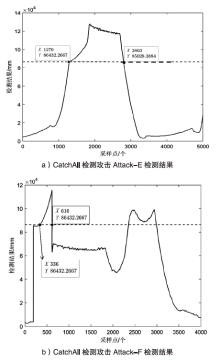
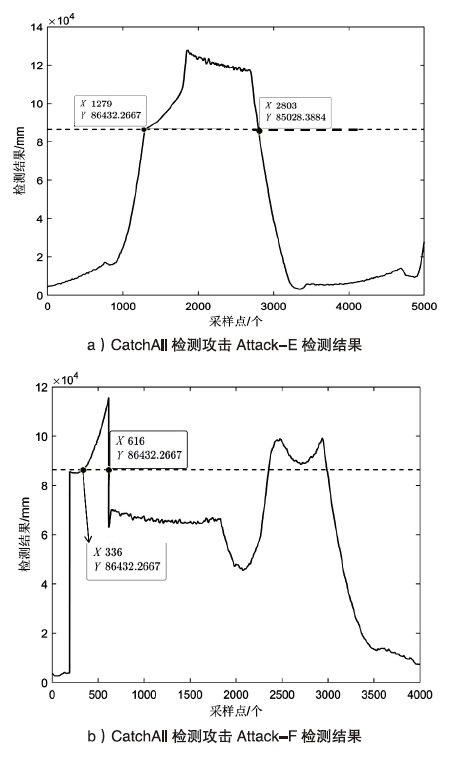
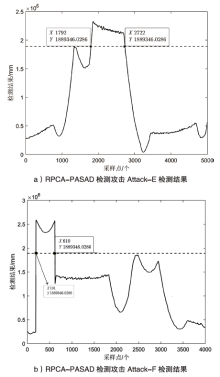
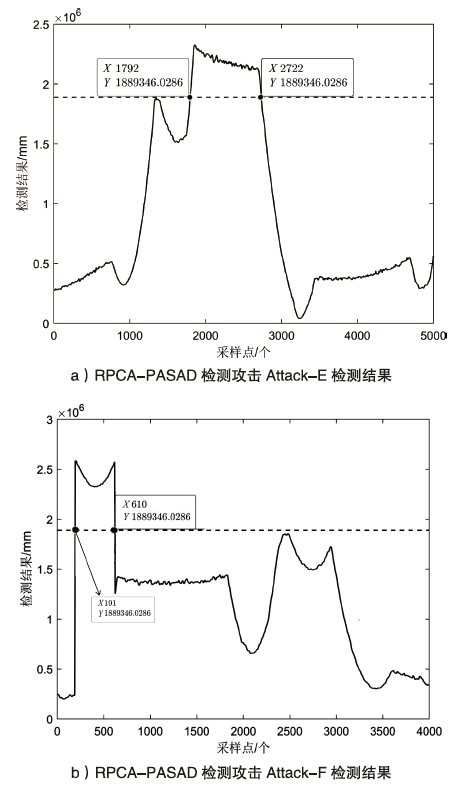
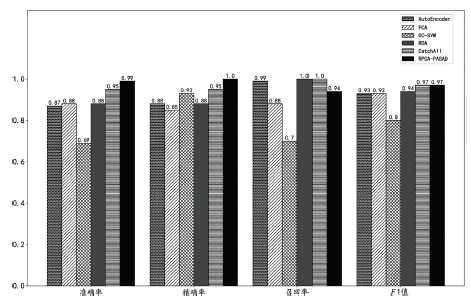
Netinfo Security ›› 2022, Vol. 22 ›› Issue (12): 34-46.doi: 10.3969/j.issn.1671-1122.2022.12.005
Previous Articles Next Articles
Defense Research of High-Hidden Data Attack in Industry Control System
XU Ruzhi1, LYU Changran1( ), LONG Yan2, LIU Yuanbin1
), LONG Yan2, LIU Yuanbin1
- 1. School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
2. State Power Investment Group Digital Technology Co., Ltd., Beijing 100080, China
-
Received:2022-07-01Online:2022-12-10Published:2022-12-30 -
Contact:LYU Changran E-mail:120212227100@ncepu.edu.cn
CLC Number:
Cite this article
XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System[J]. Netinfo Security, 2022, 22(12): 34-46.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.12.005
| [1] | LIU Weidi, GUO Qiaojin, CHAN Yuandong, et al. Review of Industrial Control System Security Development[J]. Information Research, 2021, 47(1): 1-9. |
| 刘蔚棣, 郭乔进, 产院东, 等. 工业控制系统安全发展综述[J]. 信息化研究, 2021, 47(1):1-9. | |
| [2] | FAN Kefeng, ZHOU Ruikang, LI Lin. Research on Information Security Standard System of Industrial Control System[J]. Information Technology & Standardization, 2016(6): 17-21. |
| 范科峰, 周睿康, 李琳. 工业控制系统信息安全标准体系研究[J]. 信息技术与标准化, 2016(6): 17-21. | |
| [3] |
MASOOD Z, RAJA M A Z, CHAUDHARY N I, et al. Fractional Dynamics of Stuxnet Virus Propagation in Industrial Control Systems[J]. Mathematics, 2021, 9(17): 1-27.
doi: 10.3390/math9010001 URL |
| [4] | AOUDI W, ITURBE M, ALMGREN M. Truth will Out: Departure-Based Process-Level Detection of Stealthy Attacks on Control Systems[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 817-831. |
| [5] | AOUDI W, ALMGREN M. A Framework for Determining Robust Context-Aware Attack-Detection Thresholds for Cyber-Physical Systems[C]// ACM. 2021 Australasian Computer Science Week Multiconference. New York: ACM, 2021: 1-6. |
| [6] | WAGHMARE S, KAZI F, SINGH N. Data Driven Approach to Attack Detection in a Cyber-Physical Smart Grid System[C]// IEEE. 2017 Indian Control Conference (ICC). New York: IEEE, 2017: 271-276. |
| [7] | LIU Dalong. Modeling and Detection of Sinusoidal Attack in Industrial Control System Based on MSPCA and its Improved Algorithm[D]. Hangzhou: Zhejiang University, 2018. |
| 刘大龙. 基于MSPCA及其改进算法的工控系统正弦攻击建模与检测研究[D]. 杭州: 浙江大学, 2018. | |
| [8] |
KAVOUSI-FARD A, SU W, JIN T. A Machine-Learning-Based Cyber Attack Detection Model for Wireless Sensor Networks in Microgrids[J]. IEEE Transactions on Industrial Informatics, 2020, 17(1): 650-658.
doi: 10.1109/TII.2020.2964704 URL |
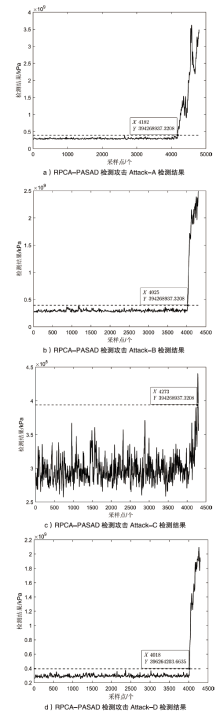
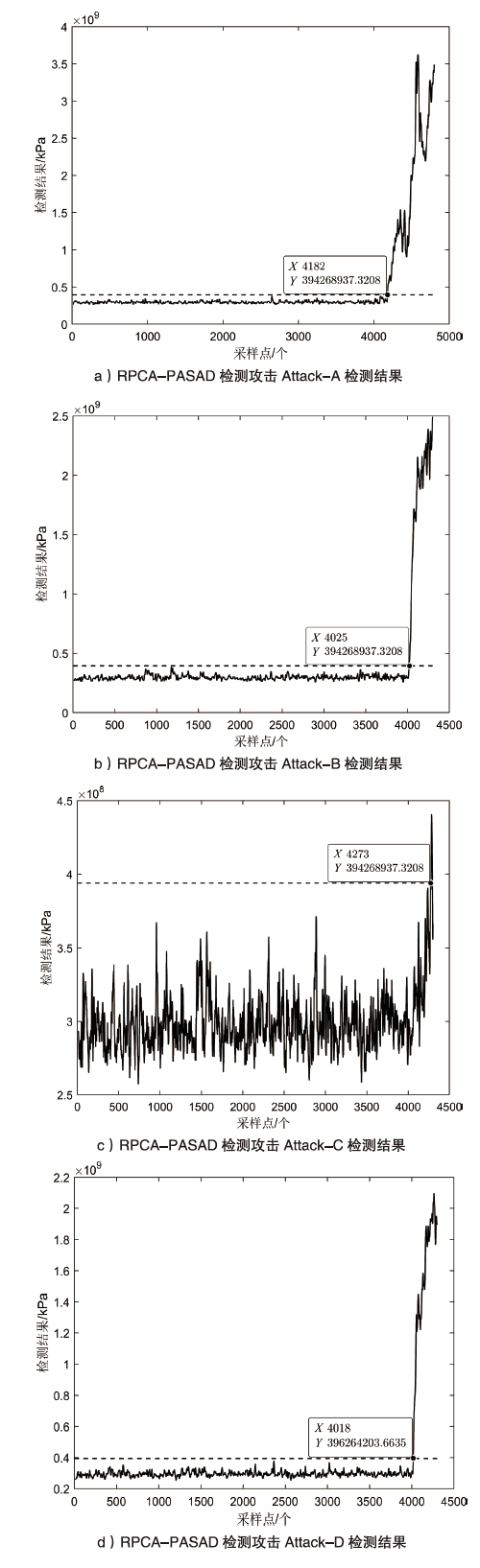
| [9] | CANDES E J, LI Xiaodong, MA Yi, et al. Robust Principal Component Analysis?[J]. Journal of the ACM (JACM), 2011, 58(3): 1-37. |
| [10] | JIN Lin, LI Yan. Analysis of Several Correlation Coefficients and Their Implementation in R language[J]. Statistics & Information Forum, 2019, 34(4): 3-11. |
| 金林, 李研. 几种相关系数辨析及其在R语言中的实现[J]. 统计与信息论坛, 2019, 34(4):3-11. | |
| [11] |
DOWNS J J, VOGEL E F. A Plant-Wide Industrial Process Control Problem[J]. Computers & Chemical Engineering, 1993, 17(3): 245-255.
doi: 10.1016/0098-1354(93)80018-I URL |
| [12] | LIU De, WANG Xianshang. On-Line Identification State-Space Method of Multivariable System[J]. Systems Engineering, 1989(6): 59-63. |
| 刘德, 王先上. 多变量线性系统的在线辨识[J]. 系统工程, 1989(6):59-63. | |
| [13] |
YANG Yimin. The Modified Form of Weiszfeld’s Algorithm[J]. Journal on Numerical Methods and Computer Applications, 1993(4): 287-294.
doi: 10.12288/szjs.1993.4.287 |
|
杨益民. 修正的Weiszfeld算法[J]. 数值计算与计算机应用, 1993(4):287-294.
doi: 10.12288/szjs.1993.4.287 |
|
| [14] | GOH J, ADEPU S, JUNEJO K N, et al. A Dataset to Support Research in the Design of Secure Water Treatment Systems[C]// Springer. International Conference on Critical Information Infrastructures Security. Heidelberg: Springer, 2016: 88-99. |
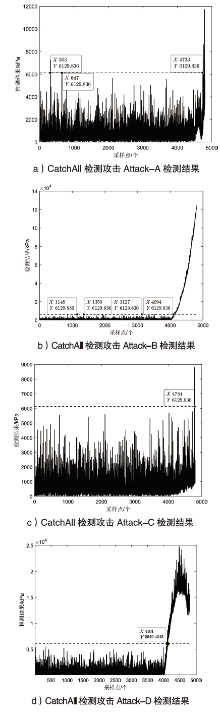
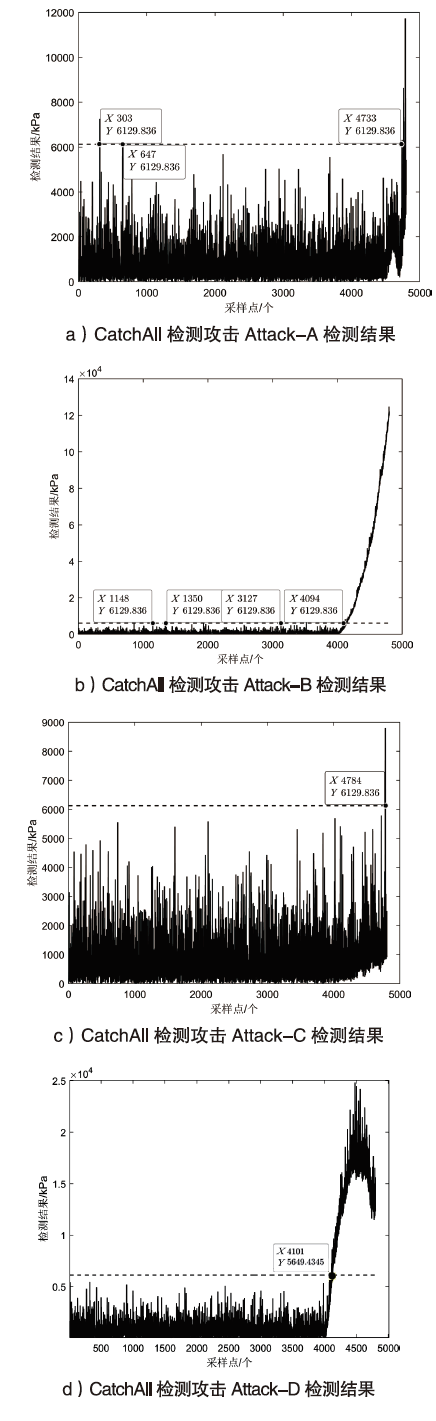
| [15] | DUTTA A K, MUKHOTY B, SHUKLA S K. CatchAll: A Robust Multivariate Intrusion Detection System for Cyber-Physical Systems Using Low Rank Matrix[C]// ACM.Proceedings of the 2th Workshop on CPS&IoT Security and Privacy. New York: ACM, 2021: 47-56. |
| [16] |
KU Wenfu, STORER R H, GEORGAKIS C. Disturbance Detection and Isolation by Dynamic Principal Component Analysis[J]. Chemometrics and Intelligent Laboratory Systems, 1995, 30(1): 179-196.
doi: 10.1016/0169-7439(95)00076-3 URL |
| [17] | MALHOTRA P, RAMAKRISHNAN A, ANAND G, et al. LSTM-Based Encoder-Decoder for Multi-Sensor Anomaly Detection[EB/OL]. [2022-06-03]. https://arxiv.org/pdf/1607.00148.pdf. |
| [18] | INOUE J, YAMAGATA Y, CHEN Yuqi, et al. Anomaly Detection for a Water Treatment System Using Unsupervised Machine Learning[C]// IEEE. 2017 IEEE International Conference on Data Mining Workshops (ICDMW). New York: IEEE, 2017: 1058-1065. |
| [19] | ZHOU Chong, PAFFENROTH R C. Anomaly Detection with Robust Deep Autoencoders[C]// ACM. Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2017: 665-674. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||