Netinfo Security ›› 2020, Vol. 20 ›› Issue (9): 107-111.doi: 10.3969/j.issn.1671-1122.2020.09.022
Previous Articles Next Articles
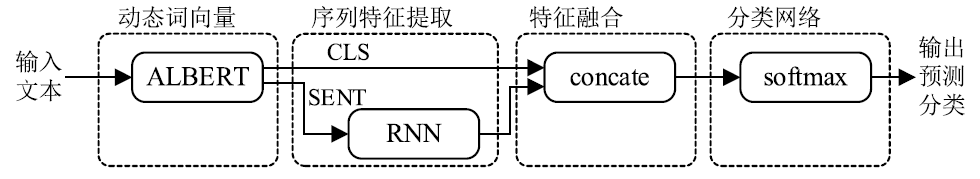
Spam Filtering Model Based on ALBERT Dynamic Word Vector
ZHOU Zhining, WANG Binjun( ), ZHAI Yiming, TONG Xin
), ZHAI Yiming, TONG Xin
- College of Information and Cyber Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2020-07-16Online:2020-09-10Published:2020-10-15 -
Contact:WANG Binjun E-mail:wangbinjun@ppsuc.edu.cn
CLC Number:
Cite this article
ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector[J]. Netinfo Security, 2020, 20(9): 107-111.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.09.022
| [1] | LIN Yanzhong, PEI Zhiyong, LIU Chuanqi, et al. Research Report on the Security of Chinese Enterprise Email in 2019[EB/OL]. https://shs3.b.qianxin.com/qax/345df09630c9033c11e8ad173c743fe4.pdf, 2020-1-13. |
| 林延忠, 裴志勇, 刘川琦, 等. 2019年中国企业邮箱安全性研究报告[EB/OL]. https://shs3.b.qianxin.com/qax/345df09630c9033c11e8ad173c743fe4.pdf, 2020-1-13. | |
| [2] | GAO Feng. Will Spam Disappear in 2020[J]. Computer and Network, 2020,4:53. |
| 高枫. 垃圾邮件会在2020年消失吗[J]. 计算机与网络, 2020,4:53. | |
| [3] | E Security. Ten Threats of Dark Network[J]. Information Security in China, 2018,9:110-111. |
| E安全. 暗网的十大威胁[J]. 中国信息安全, 2018,9:110-111. | |
| [4] | MOHAMED Bennasar, HICKS Yulia, SETCHI Rossitza. Feature Selection Using Joint Mutual Information Maximisation[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=c804e73158237c088c06a43ffb61aa54&site=xueshu_se, 2020-6-30. |
| [5] |
LIU Li, CHEN Jie, FIEGUTH Paul, et al. From BoW to CNN: Two Decades of Texture Representation for Texture Classification[J]. International Journal of Computer Vision, 2019,127(1):74-109.
doi: 10.1007/s11263-018-1125-z URL |
| [6] | MIKOLOV Tomas, CHEN Kai, CORRADO Greg S, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL]. https://arxiv.org/abs/1301.3781, 2013-9-7. |
| [7] | PENNINGTON Jeffrey, SOCHER Richard, MANNING Christopher D. Glove: Global Vectors for Word Representation[C]// ACL. the 2014 Conference on Empirical Methods in Natural Language Processing, October 25-29, 2014, Doha, Qatar. Stroudsburg, PA: ACL, 2014: 1532-1543. |
| [8] | PETERS Matthew E, AMMAR Waleed, BHAGAVATULA Chandra, et al. Semi-supervised Sequence Tagging with Bidirectional Language Models[C]// ACL. the 55st Annual Meeting of the Association for Computational Linguistics, July 30-August 4, 2017, Vancouver, Canada. Stroudsburg, PA: ACL, 2017: 1756-1765. |
| [9] | PETERS Matthew E, NEUMANN Mark, IYYER Mohit, et al. Deep Contextualized Word Representations[EB/OL]. https://arxiv.org/abs/1802.05365, 2018-5-22. |
| [10] | DEVLIN Jacob, CHANG Mingwei, LEE Kenton, et al. BERT: Pre-training of Deep Bidirectional Transformers for Language Understanding[EB/OL]. https://arxiv.org/abs/1810.04805, 2019-5-24. |
| [11] | LAN Zhenzhong, CHEN Mingda, GOODMAN Sebastian, et al. ALBERT: A Lite BERT for Self-supervised Learning of Language Representations[EB/OL]. https://arxiv.org/abs/1909.11942, 2020-2-9. |
| [12] | VASWANI Ashish, SHAZEER Noam, PARMAR Niki, et al. Attention is All You Need[EB/OL]. https://arxiv.org/abs/1706.03762, 2017-12-6. |
| [13] |
ELMAN Jeffrey L. Finding Structure in Time[J]. Cognitive Science, 1990,14(2):179-211.
doi: 10.1207/s15516709cog1402_1 URL |
| [14] | WANG Xin, LIU Yuanchao, SUN Chengjie, et al. Predicting Polarities of Tweets by Composing Word Embeddings with Long Short-Term Memory[C]// ACL. the 53rd Annual Meeting of the Association for Computational Linguistics and the 7th International Joint Conference on Natural Language Processing,July 26-31, 2015, Beijing, China. Stroudsburg, PA: ACL, 2015: 1343-1353. |
| [15] | CHO Kyunghyun, MERRIENBOER Bart Van, GULCEHRE Caglar, et al. Learning Phrase Representations using RNN Encoder-Decoder for Statistical Machine Translation[EB/OL]. https://arxiv.org/abs/1406.1078, 2014-9-3. |
| [16] | SRIVASTAVA Nitish, HINTON Geoffrey E, KRIZHEVSKY Alex, et al. Dropout: a Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014,15(1):1929-1958. |
| [17] | LIN Tsungyi, GOYAL Priya, GIRSHICK Ross, et al. Focal Loss for Dense Object Detection[EB/OL]. https://arxiv.org/abs/1708.02002, 2018-2-7. |
| [1] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [4] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [5] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [6] | HUANG Na, HE Jingsha, WU Yabiao, LI Jianguo. Method of Insider Threat Detection Based on LSTM Regression Model [J]. Netinfo Security, 2020, 20(9): 17-21. |
| [7] | ZHANG Runzi, LIU Wenmao, YOU Yang, XIE Feng. Research on AISecOps Automation Levels and Technology Trends [J]. Netinfo Security, 2020, 20(9): 22-26. |
| [8] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [9] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [10] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [11] | LIU Daheng, LI Hongling. Research on QR Code Phishing Detection [J]. Netinfo Security, 2020, 20(9): 42-46. |
| [12] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [13] | ZENG Yingming, WANG Bin, GUO Min. Research on Collaborative Defense Technology of Network Security Based on Swarm Intelligence [J]. Netinfo Security, 2020, 20(9): 52-56. |
| [14] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [15] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||