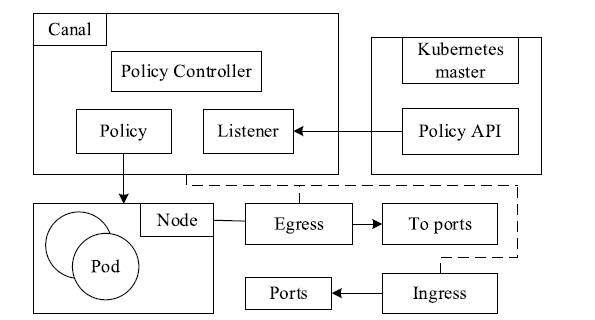
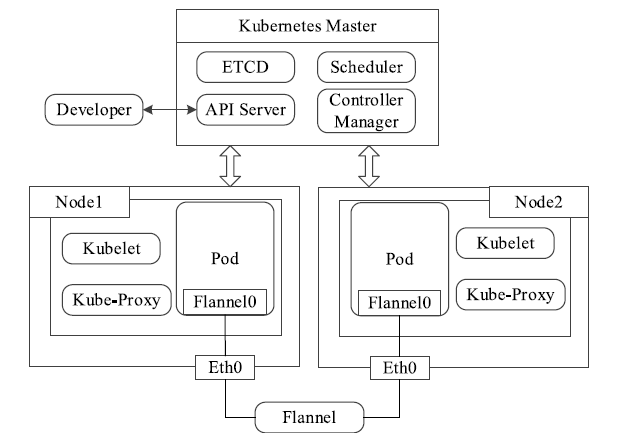
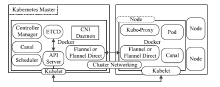
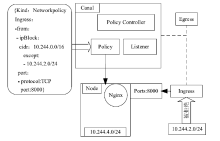
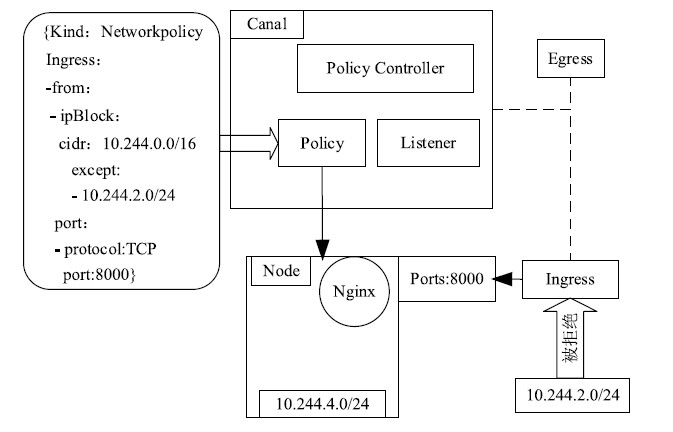
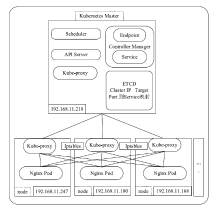
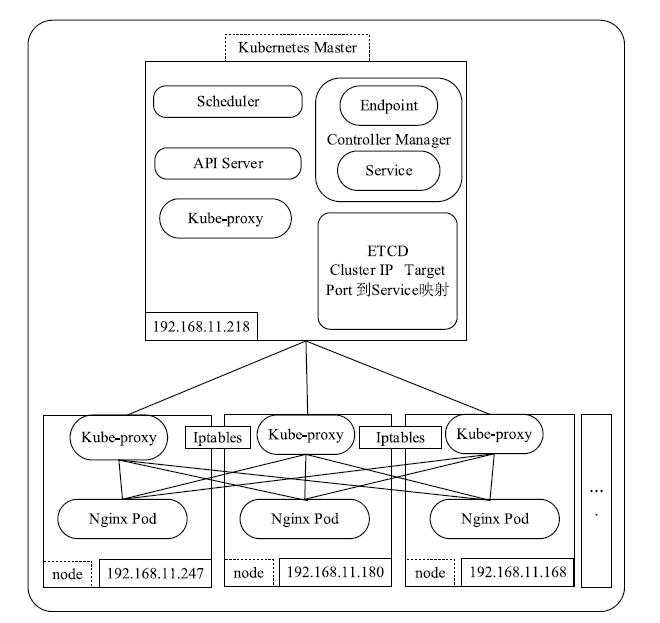
Netinfo Security ›› 2020, Vol. 20 ›› Issue (3): 36-44.doi: 10.3969/j.issn.1671-1122.2020.03.005
Previous Articles Next Articles
Research and Optimization of Container Network Based on Kubernetes Cluster System in Cloud Environment
- School of Digital Media, Jiangnan University, Wuxi 214122, China
-
Received:2019-12-28Online:2020-03-10Published:2020-05-11
CLC Number:
Cite this article
LIU Yuan, QIAO Wei. Research and Optimization of Container Network Based on Kubernetes Cluster System in Cloud Environment[J]. Netinfo Security, 2020, 20(3): 36-44.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.03.005
| [1] | RAKESH K, NEHA G, SHILPI C, et al.Open Source Solution for Cloud Computing Platform Using OpenStack[J]. International Journal of Computer Science and Mobile Computing, 2014, 3(5): 89-98. |
| [2] | YOUNGKI P, HYUNSIK Y, YOUNGHAN K.Performance Analysis of CNI(Container Networking Interface) based Container Network[C]//IEEE. 2018 International Conference on Information and Communication Technology Convergence(ICTC), October 17-19, 2018, Jeju, South Korea. New Jersey: IEEE, 2018: 248-250. |
| [3] | LI Zheng, KIHL Ma, LU Qinghua, et al.Performance Overhead Comparison between Hypervisor and Container based Virtualization[C]//IEEE. 2017 IEEE 31st International Conference on Advanced Information Networking and Applications(AINA), March 27-29, 2017, Taipei, Taiwan, China. New Jersey: IEEE, 2017: 955-962. |
| [4] | Kubernetnes. Kubernetes Documentation[EB/OL]. , 2019-12-9. |
| [5] | FLÁVIO R, AUGUSTO N. Virtualization at the Network Edge: A Performance Comparison[C]//IEEE. 17th International Symposium on a World of Wireless, Mobile and Multimedia Networks(WoWMoM), June21-24, 2016, Coimbra, Portugal. New Jersey: IEEE, 2016: 1-6. |
| [6] | DAVID B.Containers and Cloud: From LXC to Docker to Kubernetes[J]. IEEE Cloud Computing, 2014, 1(3): 81-84. |
| [7] | GONG Zheng, WU Zhihui, WANG Wei, et al.Kubernentes: Definitive Guide[M]. 4th Edition. Beijing: Publishing House of Electronics Industry, 2019. |
| 龚正,吴治辉,王伟,等. Kubernetes权威指南[M]. 4版.北京:电子工业出版社,2019. | |
| [8] | Docker Docs. Docker Container Networking[EB/OL]. , 2019-12-10. |
| [9] | Caolio. Calico Documentation[EB/OL].. |
| [10] | BI Xiaohong, LIU Yuan, CHEN Fei, Research and Optimization of Network Performance for Micro-service Application Platform[J]. Computer Engineering, 2018, 44(5): 53-59. |
| 毕小红,刘渊等.微服务应用平台的网络性能研究与优化[J].计算机工程,2018,44(5):53-59. | |
| [11] | LI Wei, ZHAO Yongbin, WANG Ou, et al.Dockers Container Network Architecture Research Based on Macvlan[J]. Machinery Design & Manufacture, 2017(5): 270-272. |
| 李巍,赵永彬,王鸥,等.基于Macvlan的Docker容器网络构架研究[J].机械设计与制造,2017(5):270-272. | |
| [12] | FENG Mingzhen.Design and Implementation of Docker Network System Based on Macvlan[D]. Hangzhou: Zhejiang University, 2016. |
| 冯明振. 基于Macvlan的Docker容器网络模型的设计与实现[D].杭州:浙江大学,2016. | |
| [13] | MARKO L.Kubernetes in Action[M]. Beijing: Publishing House of Electronics Industry, 2018. |
| [14] | ALIN C, CRISTIAN C SPOIALA, CORNELIU O T, et al.OpenStack and Docker: Building a High-performance IaaS Platform for Interactive Social Media Applications[C]//IEEE. 2016 International Conference on Development and Application Systems(DAS), May 19-21, 2016, Suceava, Romania. New Jersey: IEEE, 2016: 287-290. |
| [15] | BOETTIGER C.An Introduction to Docker for Reproducible Research[J]. ACM SIGOPS Operating Systems Review, 2015, 49(1): 71-79. |
| [16] | GUO Yanghui.Research and Implementation of Docker Container Scheduling Strategy in Micro Service[D]. Beijing: Beijing University of Posts and Telecommunications, 2018. |
| 郭杨虎. 微服务环境下Docker容器调度策略的研究与实现[D].北京:北京邮电大学,2018. | |
| [17] | XIE Bin, SUN Guanyi, GUO Ma.Docker Based Overlay Network Performance Evaluation in Large Scale Streaming System[C]//IEEE. 2016 IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference(IMCEC), October 3-5, 2016. Xi’an, China. New Jersey: IEEE, 2016: 366-369. |
| [18] | ZENG Hao, WANG Baosheng, DENG Wenping, et al.Measurement and Evaluation for Docker Container Networking[C]//IEEE. 2017 International Conference on Cyber-enabled Distributed Computing and Knowledge Discovery(CyberC), October 12-14, 2017, Nanjing, China. New Jersey: IEEE, 2017: 105-108. |
| [1] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [2] | XU Yuwei, ZHAO Baokang, SHI Xiangquan, SU Jinshu. Low-latency Optimal Orchestration of Containerized Security Service Function Chain [J]. Netinfo Security, 2020, 20(7): 11-18. |
| [3] | BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment [J]. Netinfo Security, 2020, 20(7): 85-95. |
| [4] | BAI Jiameng, KOU Yingshuai, LIU Zeyi, ZHA Daren. Docker-based RBAC Task Management System [J]. Netinfo Security, 2020, 20(1): 75-82. |
| [5] | Liangqin REN, Wei WANG, Qiongxiao WANG, Linli LU. A New Cloud Cryptographic Computing Platform Architecture and Implementation [J]. Netinfo Security, 2019, 19(9): 91-95. |
| [6] | Yi YU, Liangshuang LV, Xiaojian LI, Tianbo WANG. Dynamic Network Topology Description Language for Mobile Cloud Computing Scenario [J]. Netinfo Security, 2019, 19(9): 120-124. |
| [7] | Zixuan WANG, Liangshuang LV, Xiaojian LI, Tianbo WANG. A Shared Storage-based Virtual Machine Application Distribution Strategy for OpenStack [J]. Netinfo Security, 2019, 19(9): 125-129. |
| [8] | Yanpeng CUI, Luming FENG, Zheng YAN, Huaqing LIN. Research on Software Security Model of Cloud Computing Based on Program Slicing Technology [J]. Netinfo Security, 2019, 19(7): 31-41. |
| [9] | Xinrui GE, Wei CUI, Rong HAO, Jia YU. Verifiable Keywords Ranked Search Scheme over Encrypted Cloud Data [J]. Netinfo Security, 2019, 19(7): 82-89. |
| [10] | Chunqi TIAN, Jing LI, Wei WANG, Liqing ZHANG. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. Netinfo Security, 2019, 19(4): 11-19. |
| [11] | Pu ZHAO, Wei CUI, Rong HAO, Jia YU. A Secure Outsourcing Computation Scheme for El-Gamal Signature Generation [J]. Netinfo Security, 2019, 19(3): 81-86. |
| [12] | Zhenfeng ZHANG, Zhiwen ZHANG, Ruichao WANG. Model of Cloud Computing Security and Compliance Capability for Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2019, 19(11): 1-7. |
| [13] | Xinyang FENG, Jianjing SHEN. A Yarn and NMF Based Big Data Clustering Algorithm [J]. Netinfo Security, 2018, 18(8): 43-49. |
| [14] | Yuan TAO, Tao HUANG, Mohan ZHANG, Shuilin LI. Research and Development Trend Analysis of Key Technologies for Cyberspace Security Situation Awareness [J]. Netinfo Security, 2018, 18(8): 79-85. |
| [15] | Qi ZHANG, Xijun LIN, Haipeng QU. Identity-based Encryption Scheme Support Authorization Equality Test in Cloud Environment [J]. Netinfo Security, 2018, 18(6): 52-60. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||