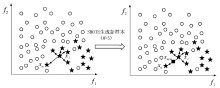
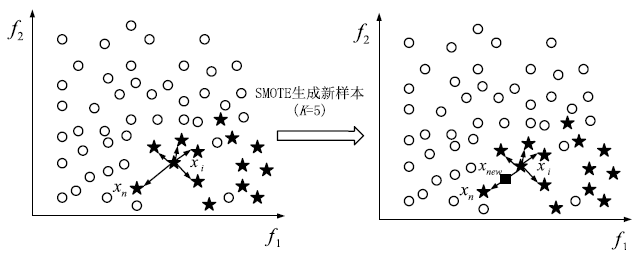
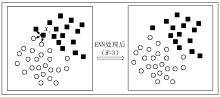
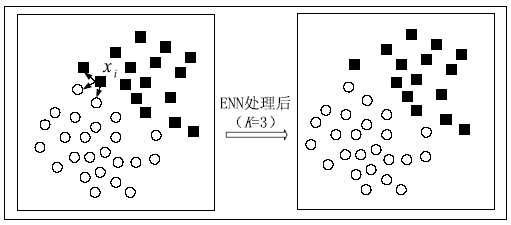
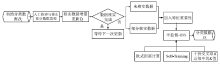
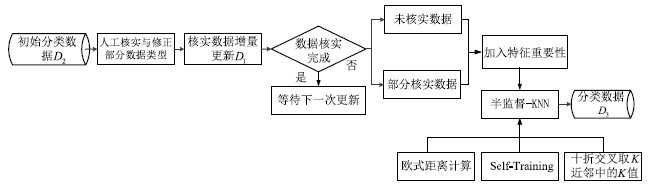
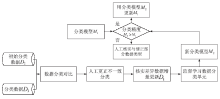
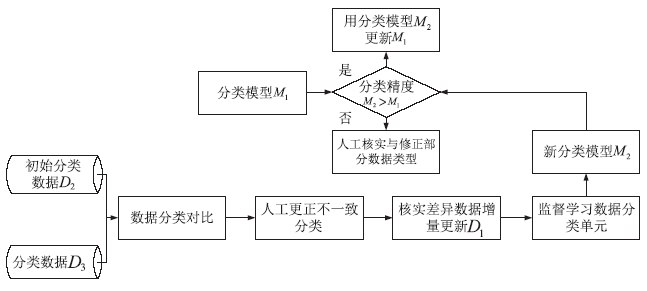
Netinfo Security ›› 2020, Vol. 20 ›› Issue (2): 66-74.doi: 10.3969/j.issn.1671-1122.2020.02.009
• 技术研究 • Previous Articles Next Articles
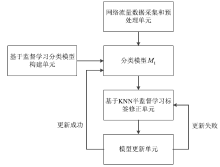
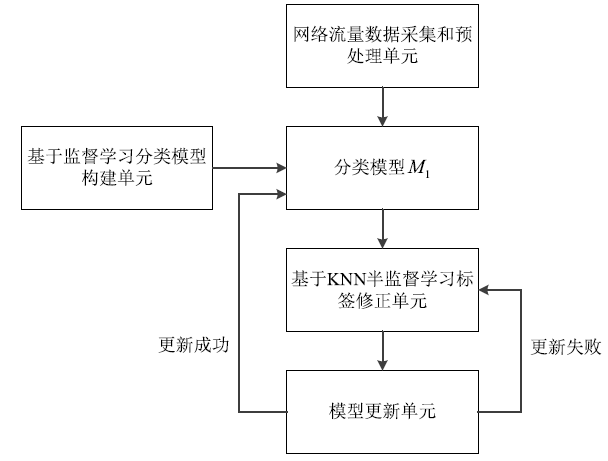
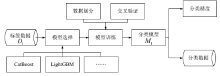
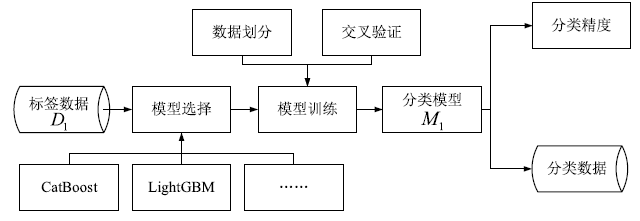
Abnormal Traffic Detection Technology Based on Data Augmentation and Model Update
ZHANG Hao1,2( ), CHEN Long1,2, WEI Zhiqiang1,2
), CHEN Long1,2, WEI Zhiqiang1,2
- 1. College of Mathematics and Computer Science, Fuzhou University, Fuzhou 350116, China
2. Fujian Provincial Key Laboratory of Network Computing and Intelligent Information Processing, Fuzhou 350116, China
-
Received:2019-10-10Online:2020-02-10Published:2020-05-11
CLC Number:
Cite this article
ZHANG Hao, CHEN Long, WEI Zhiqiang. Abnormal Traffic Detection Technology Based on Data Augmentation and Model Update[J]. Netinfo Security, 2020, 20(2): 66-74.
share this article
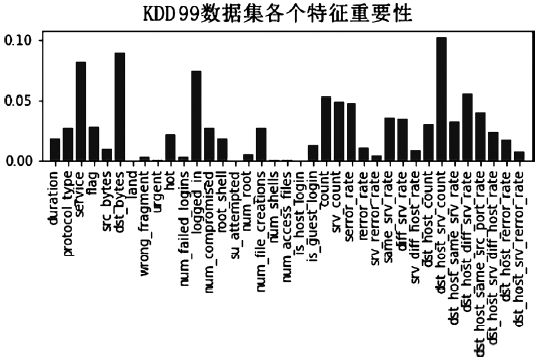
| 特征 | 重要性 | 特征 | 重要性 |
|---|---|---|---|
| dst_host_srv_count | 0.1026 | diff_srv_rate | 0.0349 |
| dst_bytes | 0.0905 | dst_host_same_srv_rate | 0.0321 |
| service | 0.0828 | dst_host_count | 0.0303 |
| logged_in | 0.0750 | flag | 0.0284 |
| dst_host_diff_srv_rate | 0.0555 | protocol_type | 0.0271 |
| count | 0.0526 | num_compromised | 0.0269 |
| srv_count | 0.0483 | num_file_creations | 0.0265 |
| serror_rate | 0.0475 | dst_host_srv_diff_host_rate | 0.0238 |
| dst_host_same_src_port_rate | 0.0399 | hot | 0.0220 |
| same_srv_rate | 0.0361 | duration | 0.0181 |
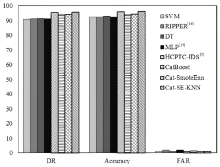
| 模型 | TNR_Normal | DR_DoS | DR_Probe | DR_R2L | DR_U2R |
|---|---|---|---|---|---|
| SVM | 98.95 | 97.10 | 74.84 | 9.69 | 8.77 |
| RIPPER[ | 98.13 | 97.42 | 80.17 | 7.00 | 10.53 |
| DT | 99.10 | 97.42 | 85.50 | 10.77 | 4.82 |
| MLP[ | 98.13 | 97.42 | 80.17 | 7.00 | 10.53 |
| HCPTC-IDS[ | 98.87 | 99.83 | 95.27 | 36.50 | 81.14 |
| CatBoost | 99.26 | 95.27 | 66.90 | 27.60 | 14.42 |
| Cat-SmoteEnn | 99.46 | 95.73 | 79.65 | 34.52 | 14.86 |
| Cat-SE-KNN | 99.62 | 98.87 | 95.42 | 55.76 | 78.93 |
| [1] | Network Security Law of the People’s Republic of China[EB/OL]. , 2016-11-7. |
| 中华人民共和国网络安全法[EB/OL]. , 2016- 11-7. | |
| [2] | BELOUCH M, EL S, IDHAMMAD M.A Two-Stage Classifier Approach Using RepTree Algorithm for Network Intrusion Detection[J]. International Journal of Advanced Computer Science and Applications, 2017, 8(6): 137-142. |
| [3] | JIA Fan, YAN Yan, ZHANG Jiaqi.k-means Based Feature Reduction for Network Anomaly Detection[J]. Journal of Tsinghua University(Science and Technology), 2018, 58(2): 137-142. |
| 贾凡,严妍,张家琪.基于k-means聚类特征消减的网络异常检测[J]. 清华大学学报(自然科学版),2018,58(2):137-142. | |
| [4] | ASHFAQ R A R, WANG Xizhao, HUANG Zhexue, et al. Fuzziness Based Semi-Supervised Learning Approach for Intrusion Detection System[J]. Information Sciences, 2016, 378(C): 484-497. |
| [5] | AHMIM A, DERDOUR M, FERRAG M A.An Intrusion Detection System Based on Combining Probability Predictions of a Tree of Classifiers[J]. International Journal of Communication Systems, 2018, 31(9): e3547. |
| [6] | YANG Xudong, GAO Ling, WANG Hai, et al.A Cooperative Deep Belief Network for Intrusion Detection[C]//IEEE. 2018 Sixth International Conference on Advanced Cloud and Big Data, August 12-15, Lanzhou, China. New York: IEEE, 2018: 230-236. |
| [7] | GREGGIO N.Anomaly Detection in IDSs by Means of Unsupervised Greedy Learning of Finite Mixture Models[J]. Soft Computing, 2018, 22(10): 3357-3372. |
| [8] | CHAWLA N V, BOWYER K W, HALL L O, et al.SMOTE: Synthetic Minority Over-Sampling Technique[J]. Journal of Artificial Intelligence Research, 2002, 16(1): 321-357. |
| [9] | WILSON D L. Asymptotic Properties of Nearest Neighbor Rules Using Edited Data[J]. IEEE Transactions on Systems, Man and Cybernetics, 1972, SMC-2(3): 408-421. |
| [10] | BREIMAN L.Random Forests[J]. Machine Learning, 2001, 45(1): 5-32. |
| [11] | SYLVESTER E V A, BENTZEN P, BRADBURY I R, et al. Applications of Random Forest Feature Selection for Fine-Scale Genetic Population Assignment[J]. Evolutionary Applications, 2018, 11(2): 153-165. |
| [12] | PROKHORENKOVA L, GUSEV G, VOROBEV A, et al.CatBoost: Unbiased Boosting with Categorical Features[J]. Advances in Neural Information Processing Systems, 2018, 31(3): 6638-6648. |
| [13] | HART P E.The Condensed Nearest Neighbor Rule[J]. IEEE Transactions on Information Theory, 1968, 14(3): 515-516. |
| [14] | COHEN W W.Fast Effective Rule Induction[C]//ACM. Proceedings of the Twelfth International Conference on Machine Learning Machine Learning, July 9-12, 1995, Tahoe City, California. New York: ELSEVISER, 1995: 115-123. |
| [15] | JORDAN M I, BISHOP C.Neural Networks[J]. ACM Computing Surveys, 1996, 28(1): 73-75. |
| [1] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | XIA Tianyu, GU Yijun. A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model [J]. Netinfo Security, 2020, 20(9): 97-101. |
| [4] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [5] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [6] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [7] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [8] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [9] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| [10] | YU Xiaojun, WU Yabiao, ZHANG Yuqing. Research on the Design of Cloud Security Architecture [J]. Netinfo Security, 2020, 20(9): 62-66. |
| [11] | LIU Wenmao, YOU Yang. Shifting Security Protection Mindset and Mechanisms for Novel 5G Infrastructures [J]. Netinfo Security, 2020, 20(9): 67-71. |
| [12] | BI Qinbo, ZHAO Chengdong. Research and Application of 5G Cybersecurity Threat Modeling Based on STRIDE-LM [J]. Netinfo Security, 2020, 20(9): 72-76. |
| [13] | YU Guo, WANG Chonghua, CHEN Xuehong, LI Jun. Industrial Internet Identifier Resolution Security from the Perspective of Authentication [J]. Netinfo Security, 2020, 20(9): 77-81. |
| [14] | LIU Hong, XIE Yongheng, WANG Guowei, JIANG Shuai. Ontology-based Cross-domain Security Analysis [J]. Netinfo Security, 2020, 20(9): 82-86. |
| [15] | WANG Wenhua, HAO Xin, LIU Yan, WANG Yang. The Safety Evaluation and Defense Reinforcement of the AI System [J]. Netinfo Security, 2020, 20(9): 87-91. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||