Netinfo Security ›› 2020, Vol. 20 ›› Issue (1): 67-74.doi: 10.3969/j.issn.1671-1122.2020.01.010
Previous Articles Next Articles
Multi-feature Android Malware Detection Method
HOU Liuyang, LUO Senlin( ), PAN Limin, ZHANG Ji
), PAN Limin, ZHANG Ji
- School of Information and Electronics, Beijing Institute of Technology, Beijing 100081, China
-
Received:2019-09-10Online:2020-01-10Published:2020-05-11
CLC Number:
Cite this article
HOU Liuyang, LUO Senlin, PAN Limin, ZHANG Ji. Multi-feature Android Malware Detection Method[J]. Netinfo Security, 2020, 20(1): 67-74.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.01.010
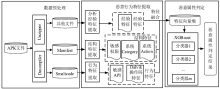
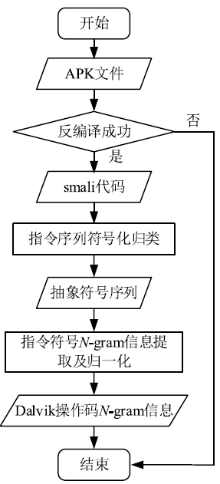
| 符号 | 语义 | 数量 | 代表的Dalvik指令 |
|---|---|---|---|
| C | Compare | 5 | Cmp-float|cmpg-float|cmpl_double|cmpg-double |cmp-long |
| D | Definition | 11 | Const|const/4|const/16|const-wide|const/high|const-string |
| M | manipulation | 13 | Move|move-wide|move-object|move-result|move-exception |
| R | Reture | 4 | Reture|return-void|return-wide|return-object |
| L | Monitor | 2 | Monitor-enter|monitor-exit |
| G | Jump | 3 | Goto|goto/16|goto/32 |
| I | Judgemnet | 12 | If-eq|if-ne|if-lt|if-ge|if-gt|if-le|if-eqz|if-nez|if-gez|if-gtz|if-lez |
| T | Reading | 21 | Aget|iget|sget|aget-wide|aget-object|aget-boolea|aget-byte|aget-char |
| P | Writing | 21 | Ainput|iput|sput|aput-wide|aput-object|aput-boolea| aput-byte|aput-char |
| V | Method call | 15 | Invoke-virtual|invoke-super|invike-direct|invoke-static |
| 特征类别 | 数量 | 特征部分实例 |
|---|---|---|
| 敏感API特征 | 629 | Android/net/ConnectivityManager;startUsingNetworkFeature Android/net/wifi/p2p/WifiP2pManager;initialize Android/net/ConnectivityManager;stopUsingNetworkFeature Android/provider/Browser;getVisitedHistory Android/location/LocationManager;getProvider |
| 敏感权限特征 | 21 | Android.permission.CAMERA Android.permission.READ_CONTACTS Android.permission.WRITE_CONTACTS Android.permission.READ_PHONE_STATE Android.permission.READ_CALL_LOG |
| 系统Action特征 | 41 | Android.intent.action.MAIN Android.intent.action.VIEW Android.intent.action.PICK_ACTIVITY Android.intent.action.MEDIA_MOUNTED Android.intent.action.MEDIA_UNMOUNTED |
| 系统Category | 11 | Android.intent.category.DEFAULT Android.intent.category.BROWSABLE Android.intent.category.TAB Android.intent.category.CAR_DOCK Android.intent.category.DESK_DOCK |
| 经验特征 | 17 | 权限数量 资源文件中包含图像的文件个数 资源文件中包含可执行文件个数 DEX文件中所有类的个数超过10个 DEX文件中所有方法的个数超过1000个 |
| [1] | FORNI A A. Gartner Says Worldwide Sales of Smartphones Grew 9 Percent in First Quarter of 2017[EB/OL]. , 2019-6-5. |
| [2] | NICOLAS L. Number of Available Applications in the Google Play Store from December 2009 to December 2017[EB/OL]. , 2019-6-5. |
| [3] | RALF B. Malware Trends 2017[EB/OL]. , 2019-6-5. |
| [4] | WU Dongjie, MAO C H, WEI T E, et al.DroidMat: Android Malware Detection through Manifest and API Calls Tracing[C]//IEEE. 2012 Seventh Asia Joint Conference on IEEE, August 9-10, 2012, Tokyo Japan. New Jersey: IEEE, 2012: 62-70. |
| [5] | AU K W Y, ZHOU Yifan, ZHANG Huang, et al. PScout: Analyzing the Android Permission Specification[C]//ACM. ACM Conference on Computer & Communications Security ACM, October 16-18, 2012, Raleigh, NC, USA. New York: ACM, 2012: 217-228. |
| [6] | PANDITA R, XIAO Xusheng, YANG Wei, et al.WHYPER: Towards Automating Risk Assessment of Mobile Applications[C]//ACM. 22nd USENIX Conference on Security, August 14-16, 2013, Berkeley, CA, USA. New York: ACM, 2013: 571-584. |
| [7] | IDRESS F, RAJARAJAN M.Investigating the Android Intents and Permissions for Malware Detection[C]//IEEE. 10th International Conference on Wireless and Mobile Computing, Networking and Communications(WiMob), October 8-10, 2014, Larnaca, Cyprus. New Jersey: IEEE, 2014: 354-358. |
| [8] | LI Li, BARTEL A, BISSYANDE T F, et al.IccTA: Detecting Inter-Component Privacy Leaks in Android Apps[C]//IEEE. 37th International Conference on Software Engineering(ICSE 2015), May 16-24, 2015, Florence/Firenze, Italy. New Jersey: IEEE, 2015: 280-291. |
| [9] | ARP D, SPREITZENBARTH M, HUBNER M, et al.Drebin: Effective and Explainable Detection of Android Malware in Your Pocket[C]//IEEE. 2014 Network and Distributed System Security Symposium, February 23-26, 2014, San Diego, California, USA. New Jersey: IEEE, 2014: 23-38. |
| [10] | CHIN E, FELT A P, GREENWOOD K, et al.Analyzing Interapplication Communication in Android[J]. Signo Pensam, 2006, 27(49): 36-45. |
| [11] | ZHOU Wu, ZHOU Yajin, GRACE M, et al.Fast, Scalable Detection of Piggybacked Mobile Applications[C]//ACM.3rd ACM Conference on Data and Application Security and Privacy, February 18-20, 2013, San Antonio, TX, USA. New York: ACM, 2013: 185-196. |
| [12] | HOFFMANN J, USSATH M, HOLZ T, et al.Slicing Droids: Program Slicing for Smali Code[C]//ACM. 28th Annual ACM Symposium on Applied Computing, March 18-22, 2013, Coimbra, Portugal. New York: ACM, 2013: 1844-1851. |
| [13] | YU Wei, GE Linqiang, XU Guobin, et al. Towards Neural Network Based Malware Detection on Android Mobile Devices[EB/OL]. , 2019-6-5. |
| [14] | ZHOU Wu, ZHOU Yajin, JIANG Xuxian, et al.Detecting Repackaged Smartphone Applications in Third-party Android Marketplaces[C]//ACM. 2nd ACM Conference on Data and Application Security and Privacy, February 7-9, 2012, San Antonio, Texas, USA. New York: ACM, 2012: 317-326. |
| [15] | WOGNSEN E R, KARLSEN H S, OLESEN M C, et al. Formalisation and Analysis of Dalvik Bytecode[EB/OL]. , 2019-7-10. |
| [16] | AAFER Y, DU Wenliang, YIN Heng.DroidAPIMiner: Mining API-level Features for Robust Malware Detection in ANDROID[C]//Springer. International Conference on Security and Privacy in Communication Systems, September 25-28, Sydney, NSW, Australia. Heidelberg: Springer, 2013: 86-103. |
| [17] | WEI Fengguo, LI Yuping, ROY S, et al.Deep Ground Truth Analysis of Current Android Malware[C]//Springger. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, July 6-7, 2017, Bonn, Germany. Heidelberg: Springer, 2017: 252-276. |
| [18] | LI Jin, SUN Lichao, YAN Qiben, et al.Significant Permission Identification for Machine-learning-based Android Malware Detection[J]. IEEE Transactions on Industrial Informatics, 2018, 14(7): 3216-3225. |
| [19] | XIE Niannian, ZENG Fanping, QIN Xiaoxia, et al.RepassDroid: Automatic Detection of Android Malware Based on Essential Permissions and Semantic Features of Sensitive APIs[C]//IEEE. 2018 International Symposium on Theoretical Aspects of Software Engineering(TASE), August 14-16, 2018, Guangzhou, China. New Jersey: IEEE, 2018: 52-59. |
| [20] | ZHANG Hanqing, LUO Senlin, ZHANG Yifei, et al. An Efficient Android Malware Detection System Based on Method-level Behavioral Semantic Analysis[EB/OL]. , 2019-8-12. |
| [1] | YUAN Xiaoxiao, LUO Senlin, YANG Peng. Research on Android Application DEX File Protection Method [J]. Netinfo Security, 2020, 20(7): 60-69. |
| [2] | Xin SONG, Kai ZHAO, Linlin ZHANG, Wenbo FANG. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [3] | Yanchen QIAO, Qingshan JIANG, Liang GU, Xiaoming WU. Malware Classification Method Based on Word Vector of Assembly Instruction and CNN [J]. Netinfo Security, 2019, 19(4): 20-28. |
| [4] | Liping DING, Xuehua LIU, Guangxuan CHEN, Yin LI. Overview of Digital Forensics Technologies of RAM in Android Devices [J]. Netinfo Security, 2019, 19(2): 10-17. |
| [5] | Xuruirui FENG, Jiayong LIU, Pengsen CHENG. Analyzing Malware Behavior and Capability Related Text Based on Feature Extraction [J]. Netinfo Security, 2019, 19(12): 72-78. |
| [6] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [7] | Yanhua LIU, Xiaoling GAO, Minchen ZHU, Peihuang SU. Research on Classification Method of Network Security Data Based on Data Feature Learning [J]. Netinfo Security, 2019, 19(10): 50-56. |
| [8] | Zhongyuan QIN, Junrui ZHANG, Qunfang ZHANG, Zhiyong SONG. Android Terminals Control Technology Based on Inject and Hook [J]. Netinfo Security, 2018, 18(9): 66-73. |
| [9] | Yang ZHANG, Yuangang YAO. Research on Network Intrusion Detection Based on Xgboost [J]. Netinfo Security, 2018, 18(9): 102-105. |
| [10] | Yunchun LI, Wentao LU, Wei LI. Malware Detection Method Based on Shapelet [J]. Netinfo Security, 2018, 18(3): 70-77. |
| [11] | Xinlong SONG, Dong ZHENG, Zhonghuang YANG. Mobile Device Management System Based on AOSP and SELinux [J]. Netinfo Security, 2017, 17(9): 103-106. |
| [12] | Debing LU, Haoliang CUI, Wen ZHANG, Shaozhang NIU. Application Security Reinforcement Scheme Based on Intent Filter [J]. Netinfo Security, 2017, 17(11): 67-73. |
| [13] | Jiajia LIU, Yan YU, Hengwei HU, Jiashun WU. Research on a Protection Mechanism Based on Virtual Machine Customization [J]. Netinfo Security, 2017, 17(1): 63-67. |
| [14] | Yi WANG, Yong TANG, Zexin LU, Xin YU. Research on Features Selection in Malware Clustering [J]. Netinfo Security, 2016, 16(9): 64-68. |
| [15] | Jian ZHANG, Wenxu WANG, Pengfei NIU, Zhaojun GU. Research on Test Evaluation System of Anti-malware Products and Service [J]. Netinfo Security, 2016, 16(9): 113-117. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||