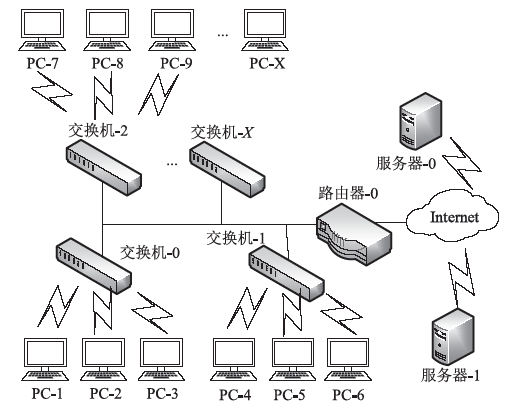
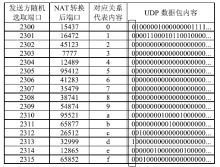
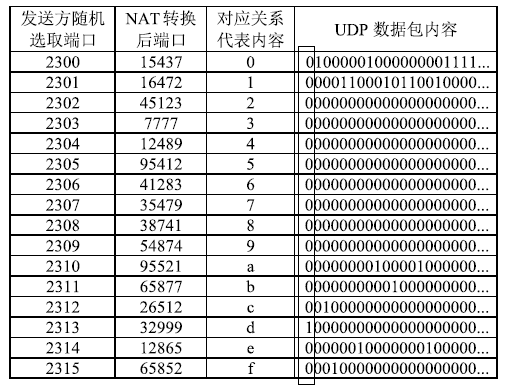
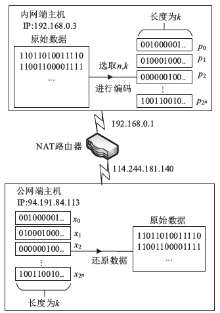
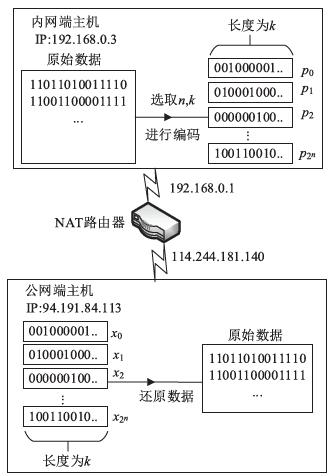
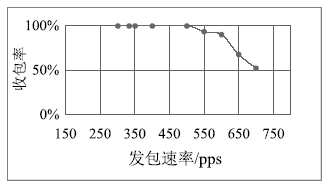
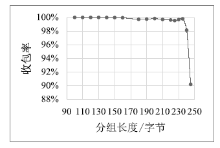
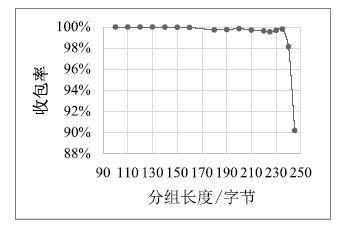
| [1] |
FRANCIS P.IP Network Address Translator(NAT) [EB/OL]., 1994-2-22.
|
| [2] |
SRISURESH P, HOLDREGE M.IP Network Address Translator(NAT) Terminology and Considerations[M]. Fremont: RFC Editor, 1999.
|
| [3] |
LAMPSON B W.A Note on the Confinement Problem[J]. Communications of the ACM, 1973, 16(10): 613-615.
|
| [4] |
GIRLING C G.Covert Channels in LAN’s[J]. IEEE Transactions on Software Engineering, 1987, SE-13(2): 292-296.
|
| [5] |
HANDEL T G, SANDFORD M T.Hiding Data in the OSI Network Model[C]//ACM. 1st International Workshop on Information Hiding, May 30-June 1, 1996, London. New York: ACM, 1996: 23-38.
|
| [6] |
ROWLAND C H.Covert Channels in the TCP/IP Protocol Suite[J]. Peer Reviewed Journal on the Internet, 1997, 2(5): 1-5.
|
| [7] |
LOU Jiapeng, ZHANG Meng, FU Peng, et al.Design of a Network Covert Transmission Scheme Based on TCP Protocol[J]. Netinfo Security, 2016, 16(1): 34-39.
|
|
娄嘉鹏,张萌,付鹏,等. 一种基于TCP协议的网络隐蔽传输方案设计[J]. 信息网络安全,2016,16(1):34-39.
|
| [8] |
ZHANG Ran, YIN Yifeng, HUANG Xinpeng, et al.Research and Implementation of Network Covert Channels[J]. Netinfo Security, 2013, 13(7): 44-46.
|
|
张然,尹毅峰,黄新彭,等. 网络隐蔽通道的研究与实现[J]. 信息网络安全,2013,13(7):44-46.
|
| [9] |
AMERI A, JOHNSON D.Covert Channel over Network Time Protocol[EB/OL]. , 2019-1-11.
|
| [10] |
SEBASTIAN Z, ARMITAGE G, BRANCH P.Covert Channels in Multiplayer First Person Shooter Online Games[C]//IEEE. 33rd IEEE Conference on Local Computer Networks, October 14-17, 2008, Montreal, Que, Canada. New Jersey: IEEE, 2008: 215-222.
|
| [11] |
LIPNER S B.A Comment on the Confinement Problem[J]. ACM SIGOPS Operating Systems Review, 1975, 9(5): 192-196.
|
| [12] |
ZANDER S, ARMITAGE G, BRANCH P.An Empirical Evaluation of IP Time to Live Covert Channels[C]//IEEE. 15th IEEE International Conference on Networks, November 19-21, 2007, Adelaide, SA, Australia. New Jersey: IEEE, 2007: 42-47.
|
| [13] |
CABUK S, BRODLEY C, SHIELDS C.IP Covert Timing Channels Design and Detection[C]//ACM. 11th ACM Conference on Computer and Communications Security, October 25-29, 2004, Washington DC, USA. New York: ACM, 2004: 178-187.
|
| [14] |
BERK V, GIANI A, CYBENKO G,et al.Detection of Covertchannel Encoding in Network Packet Delays[EB/OL]. , 2019-1-12.
|
| [15] |
KEMMERER R A.Shared Resource Matrix Methodology: An Approach to Identifying Storage and Timing Channels[J]. ACM Transactions on Computer Systems, 1983, 1(3): 256-277.
|
| [16] |
LI Wei, SONG Tian.Concealed Channel Construction Method for NAT Environment[J]. Computer Engineering and Applications, 2018, 54(17): 108-114.
|
|
李卫,嵩天. 适用于NAT环境的隐蔽通道构建方法[J]. 计算机工程与应用,2018,54(17):108-114.
|
| [17] |
ZHANG Jiuwen, LIU Li, MA Yide.Research on Optimal State Coding[J]. Journal of Gansu Science, 2002, 14(4): 45-48.
|
|
张久文,刘莉,马义德. 最优状态编码研究[J]. 甘肃科学学报,2002,14(4):45-48.
|
| [18] |
XIE Weihua.Design and Implementation of Embedded Video Surveillance System Server[D]. Chengdu: Southwest Jiaotong University, 2009.
|
|
谢韦华. 嵌入式视频监控系统服务器的设计与实现[D]. 成都:西南交通大学,2009.
|