Netinfo Security ›› 2019, Vol. 19 ›› Issue (4): 63-72.doi: 10.3969/j.issn.1671-1122.2019.04.008
Previous Articles Next Articles
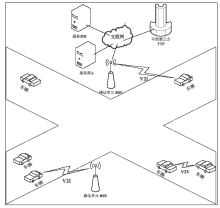
Survey of Privacy Preservation in VANET
Yilin LI1, Zheng YAN1,2( ), Haomeng XIE1
), Haomeng XIE1
- 1. School of Cyber Engineering, Xidian University, Xi’an Shaanxi 710071, China;
2. Key Lab of Information Network Security of Ministry of Public Security, The Third Research Institute of Ministry of Public Security, Shanghai 201204, China
-
Received:2019-01-10Online:2019-04-10Published:2020-05-11
CLC Number:
Cite this article
Yilin LI, Zheng YAN, Haomeng XIE. Survey of Privacy Preservation in VANET[J]. Netinfo Security, 2019, 19(4): 63-72.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.04.008
| 位置隐私 保护方案 | 抵抗 相关性攻击 | 抵抗恶意服务商 攻击 | 查询内容加密 | 是否 依靠 可信 第三方 | 服务 质量 | 计算 开销 | 条件 隐私 保护 | |
|---|---|---|---|---|---|---|---|---|
| 针对V2V通信的 位置隐私保护方案 | 文献[ | 高 | 高 | 是 | 是 | 低 | 中 | 是 |
| 文献[ | 中 | 中 | 是 | 是 | 高 | 中 | 是 | |
| 文献[ | 否 | 不涉及 | 是 | 是 | 高 | 低 | 是 | |
| 针对V2I通信的 位置隐私保护方案 | 文献[ | 不涉及 | 高 | 是 | 是 | 高 | 高 | 是 |
| 文献[ | 不涉及 | 高 | 是 | 否 | 中 | 高 | 否 | |
| 文献[ | 不涉及 | 高 | 是 | 是 | 中 | 中 | 是 | |
| 文献[ | 否 | 低 | 否 | 否 | 高 | 中 | 否 | |
| 文献[ | 低 | 中 | 是 | 是 | 中 | 高 | 是 | |
| 文献[ | 不涉及 | 高 | 否 | 否 | 高 | 高 | 否 | |
| [1] | RAYA M, HUBAUX J P.Securing Vehicular Ad-hoc Networks[J]. Journal of Computer Security, 2007, 15(1): 39-68. |
| [2] | TALEB T, SAKHAEE E, JAMALIPOUR A, et al.A Stable Routing Protocol to Support ITS Services in VANET Networks[J]. IEEE Transactions on Vehicular Technology, 2007, 56(6): 3337-3347. |
| [3] | SHEN Xia, CHENG Xiang, YANG Liuqing, et al.Data Dissemination in VANETs: A Scheduling Approach[J]. IEEE Transactions on Intelligent Transportation Systems, 2014, 15(5): 2213-2223. |
| [4] | YANG Liuqing, WANG FeiYue. Driving into Intelligent Spaces with Pervasive Communications[J]. IEEE Intelligent Systems, 2007, 22(1): 12-15. |
| [5] | ZHANG Jianming, ZHAO Yujuan, JIANG Haobin, et al.Research on Protection Technology for Location Privacy in VANET[J]. Journal on Communications, 2012, 33(8): 180-189. |
| 张建明,赵玉娟,江浩斌,等. 车辆自组网的位置隐私保护技术研究[J]. 通信学报,2012,33(8):180-189. | |
| [6] | KALAIARASY C, SREENATH N.An Incentive Based Cooperation Motivating Pseudonym Changing Strategy for Privacy Preservation in Mixed Zones in Vehicular Networks[J]. Journal of King Saud University Computer and Information Sciences, 2018, 18(5): 1-11. |
| [7] | QU Fengzhong, WU Zhihui, WANG Feiyue, et al.A Security and Privacy Review of VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2015, 16(6): 2985-2996. |
| [8] | BOUALOUACHE A, SENOUCI S M, MOUSSAOUI S.A Survey on Pseudonym Changing Strategies for Vehicular Ad-hoc Networks[J]. IEEE Communications Surveys & Tutorials, 2017, 20(1): 770-790. |
| [9] | MA Mingjie, DU Yuejin, LI Fenghua, et al.Review of Semantic-Based Privacy-Preserving Approaches in LBS[J]. Chinese Journal of Network and Information Security, 2016, 2(12): 1-11. |
| 马明杰,杜跃进,李凤华,等. 基于语义的位置服务隐私保护综述[J].网络与信息安全学报,2016,2(12): 1-11. | |
| [10] | LUCKSHETTY A, DONTAL S, TANGADE S, et al.A Survey: Comparative Study of Applications, Attacks, Security and Privacy in VANETs[C]// IEEE. 2016 International Conference on Communication and Signal Processing (ICCSP), April 6-8, 2016, Melmaruvathur, India. New York: IEEE, 2016: 1594-1598. |
| [11] | HUANG Leping, MATSUURA K, YAMANE H, et al.Enhancing Wireless Location Privacy Using Silent Period[C]// IEEE. IEEE Wireless Communications and Networking Conference, March 13-17, 2005, New Orleans, LA, USA. New York: IEEE, 2005: 1187-1192. |
| [12] | YAN Zheng, WANG Mingjun.Protect Pervasive Social Networking Based on Two Dimensional Trust Levels[J]. IEEE Systems Journal, 2017, 11(1): 207-218. |
| [13] | MEJRI M N, BEN O J.GDVAN: A New Greedy Behavior Attack Detection Algorithm for VANETs[J]. IEEE Transactions on Mobile Computing, 2017, 16(3): 759-771. |
| [14] | KANG Jiawen, YU Rong, HUANG Xumin, et al.Location Privacy Attacks and Defenses in Cloud-enabled Internet of Vehicles[J]. IEEE Wireless Communications, 2016, 23(5): 52-59. |
| [15] | CORSER G, FU Huirong, SHU Tao, et al.Privacy by Decoy: Protecting Location Privacy Against Collusion and Deanonymization in Vehicular Location Based Services[C]// IEEE. 2014 IEEE Intelligent Vehicles Symposium Proceedings, June 8-11, 2014, Dearborn, MI, USA. New York: IEEE, 2014: 1030-1036. |
| [16] | JIANG Hong, KANG Baoyuan, LI Chunqing.Improved Auditing Schemes with Identity Preserving for The Integrity of Shared Data in The Cloud[J]. Netinfo Security, 2018, 18(10): 85-91. |
| 姜红,亢保元,李春青. 改进的保护身份的云共享数据完整性公开审计方案[J]. 信息网络安全,2018,18(10):85-91. | |
| [17] | PAN Xiao, XIAO Zhen, MENG Xiaofeng.Survey of Location Privacy Preserving[J]. Journal of Computer Science and Frontiers, 2007, 1(3): 268-281. |
| 潘晓,肖珍,孟小峰. 位置隐私研究综述[J]. 计算机科学与探索,2007,1(3):268-281. | |
| [18] | TAHA S, SHEN Xuemin.A Physical layer Location Privacy Preserving Scheme for Mobile Public Hotspots in NEMO Based VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2013, 14(4): 1665-1680. |
| [19] | CORSER G P, FU Huirong, BANIHANI A.Evaluating Location Privacy in Vehicular Communications and Applications[J]. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(9): 2658-2667. |
| [20] | NIU Ben, LI Qinghua, ZHU Xiaoyan, et al.Achieving K-Anonymity in Privacy Aware Location Based Services[C]// IEEE. IEEE INFOCOM 2014-IEEE Conference on Computer Communications, April 27- May 2, 2014, Toronto, ON, Canada. New York: IEEE, 2014: 754-762. |
| [21] | YU Ruiyun, BAI Zhihong, YANG Leyou, et al.A Location Cloaking Algorithm Based on Combinatorial Optimization for Location Based Services in 5G Networks[J]. IEEE Access, 2016, 4(10): 6515-6527. |
| [22] | CUI Jie, WEN Jingyu, HAN Shunshun, et al.Efficient Privacy Preserving Scheme for Real ime Location Data in Vehicular Ad-hoc Network[J]. IEEE Internet of Things Journal, 2018, 5(5): 3491-3498. |
| [23] | SAMPIGETHAYA K, HUANG Leping, LI Mingyan, et al.CARAVAN: Providing Location Privacy for VANET[R]. Seattle: University of Washington, Department of Electrical Engineering, 98195, 2005. |
| [24] | HU Hao, LU Rongxing, ZHANG Zonghua, et al.REPLACE: A Reliable Trust Based Platoon Service Recommendation Scheme in VANET[J]. IEEE Transactions on Vehicular Technology, 2017, 66(2): 1786-1797. |
| [25] | HUANG Yan, CAI Zhipeng, BOURGEOIS A G.Search Locations Safely and Accurately: A Location Privacy Protection Algorithm with Accurate Service[J]. Journal of Network and Computer Applications, 2018, 10(3): 146-156. |
| [26] | LIU J K, CHU ChengKang, CHOW S S M, et al. Time Bound Anonymous Authentication for Roaming Networks[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(1): 178-189. |
| [27] | CABALLERO G C, MOLINA G J, HERNANDEZ S J, et al.Providing K-Anonymity and Revocation in Ubiquitous VANETs[J]. Ad Hoc Networks, 2016, 36(2): 482-494. |
| [28] | YAO Lin, LIN Chi, DENG Jing, et al.Biometrics-based Data Link Layer Anonymous Authentication in VANETs[C]// IEEE. 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, July 3-5, 2013, Taichung, Taiwan, China. New York: IEEE, 2013: 182-187. |
| [29] | BISWAS S, MIŠIC J. A Cross Layer Approach to Privacy-Preserving Authentication in Wave-enabled VANETs[J]. IEEE Transactions on Vehicular Technology, 2013, 62(5): 2182-2192. |
| [30] | SUN Yipin, FENG Zhenqian, HU Qiaolin, et al.An Efficient Distributed Key Management Scheme for Group-Signature Based Anonymous Authentication in VANET[J]. Security and Communication Networks, 2012, 5(1): 79-86. |
| [31] | CHAURASIA B K, VERMA S.Transactions on Computational Science[M]. Berlin, Heidelberg: Springer, 2011. |
| [32] | WANG Mingjun, YAN Zheng.Privacy Preserving Authentication and Key Agreement Protocols for D2D Group Communications[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3637-3647. |
| [33] | YAN Zheng, WANG Pu, FENG Wei.A Novel Scheme of Anonymous Authentication on Trust in Pervasive Social Networking[J]. Information Sciences, 2018, 445(20): 79-96. |
| [34] | JIANG Yixin, SHI Minghui, SHEN Xuemin, et al.BAT: A Robust Signature Scheme for Vehicular Networks Using Binary Authentication Tree[J]. IEEE Transactions on Wireless Communications, 2009, 8(4): 1974-1983. |
| [35] | CUI Jie, WEI Lu, ZHANG Jing, et al.An Efficient Message Authentication Scheme Based on Edge Computing for Vehicular Ad-hoc Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2018, 18(5): 1-12. |
| [36] | LI Ning, YAN Zheng, WANG Mingjun, et al.Securing Communication Data in Pervasive Social Networking Based on Trust with KP-ABE[J]. ACM Transactions on Cyber Physical Systems, 2018, 3(1): 1-17. |
| [37] | CAO Suzhen, LANG Xiaoli, LIU Xiangzhen, et al.A New Heterogeneous Signcryption Scheme in 5G Network[J]. Netinfo Security, 2018, 18(11): 33-39. |
| 曹素珍,郎晓丽,刘祥震,等. 5G网络下新的异构签密方案[J]. 信息网络安全,2018,18(11):33-39. | |
| [38] | LU Zhaojun, QU Gang, LIU Zhenglin.A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy[J]. IEEE Transactions on Intelligent Transportation Systems, 2019, 20(2): 760-776. |
| [39] | FENG Wei, YAN Zheng, ZHANG Hengrun, et al.A Survey on Security, Privacy, and Trust in Mobile Crowdsourcing[J]. IEEE Internet of Things Journal, 2018, 5(4): 2971-2992. |
| [40] | CHEN Yang, WANG Yong.A New Trust-Based AODV Routing Protocol and Performance Optimization towards Wireless Ad-hoc Networks[J]. Netinfo Security, 2018, 18(2): 40-47. |
| 陈阳,王勇. 移动Ad Hoc网络中一种安全的AODV路由协议及性能优化[J]. 信息网络安全,2018,18(2):40-47. |
| [1] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [2] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [3] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [4] | Ning LI, Bochao LI. Token-based UTM Architecture for Mobile Internet [J]. Netinfo Security, 2020, 20(3): 18-28. |
| [5] | Xinglong ZHANG, Yuting LI, Qingfeng CHENG, Lulu GUO. A Browser Security Model for Preventing TLS Protocol Downgrade Attacks [J]. Netinfo Security, 2020, 20(3): 65-74. |
| [6] | Shuilin LI, Guobang ZHU, Chunling FAN, Guangyong CHEN. Research on a New Scoring Algorithm of Testing and Evaluation for Classified Cybersecurity Protection [J]. Netinfo Security, 2020, 20(2): 1-6. |
| [7] | Xiao WANG, Jun ZHAO, Jianbiao ZHANG. Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base [J]. Netinfo Security, 2020, 20(2): 7-13. |
| [8] | Weimin LANG, Han ZHANG, Yifeng ZHAO, Jinfang YAO. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [9] | Mengmeng YAO, Li TANG, Yongxing LING, Weidong XIAO. Formal Analysis of Security Protocol Based on Strand Space [J]. Netinfo Security, 2020, 20(2): 30-36. |
| [10] | Lu YU, Senlin LUO. A Method of Internal Intrusion Detection of Database in RBAC Mode [J]. Netinfo Security, 2020, 20(2): 83-90. |
| [11] | Tao JING, Wei WAN. Research on a P2P Network Communication Behavior Analytical Method for Status Migration Attribute-oriented [J]. Netinfo Security, 2020, 20(1): 16-25. |
| [12] | Die HU, Dongtang MA, Ming GONG, Zhao MA. A Physical Layer Security Authentication Method Based on PUF [J]. Netinfo Security, 2020, 20(1): 61-66. |
| [13] | WANG Chonghua, LI Jun, CHEN Xuehong. Research on Industrial Internet Platform Security Protection [J]. Netinfo Security, 2019, 19(9): 6-10. |
| [14] | ZHENG Guogang. Implementation Methods and Technical Measures for Security Inspection of Important Information Systems [J]. Netinfo Security, 2019, 19(9): 16-20. |
| [15] | LI Meng. Mobile Application Security Construction of the National Medical Products Administration [J]. Netinfo Security, 2019, 19(9): 46-50. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||