| [1] |
GUAN Lei, HU Guangjun, WANG Zhuan.Research on Network Security Situational Awareness Technology Based on Big Data[J]. Netinfo Security, 2016, 16(9): 45-50.
|
|
管磊,胡光俊,王专.基于大数据的网络安全态势感知技术研究[J].信息网络安全,2016,16(9):45-50.
|
| [2] |
BLUM A, LIGETT K, ROTH A.A Learning Theory Approach to Non-interactive Database Privacy[J]. Journal of the ACM, 2013, 60(2): 1-25.
|
| [3] |
DWORK C.Differential Privacy[C]//Springer. International Colloquium on Automata, Languages, and Programming, July 10-14, 2006, Venice, Italy. Heidelberg: Springer, 2006: 1-12.
|
| [4] |
FANG Yuejian, ZHU Jinzhong, ZHOU Wen, et al.A Survey on Data Mining Privacy Protection Algorithms[J]. Netinfo Security, 2017, 17(2): 6-11.
|
|
方跃坚,朱锦钟,周文,等.数据挖掘隐私保护算法研究综述[J].信息网络安全,2017,17(2):6-11.
|
| [5] |
XUN Yaling, ZHANG Jifu, QIN Xiao, et al.FiDoop-DP: Data Partitioning in Frequent Itemset Mining on Hadoop Clusters[J]. IEEE Transactions on Parallel & Distributed Systems, 2017, 28(1): 101-114.
|
| [6] |
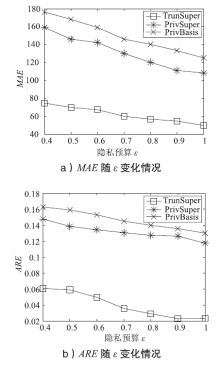
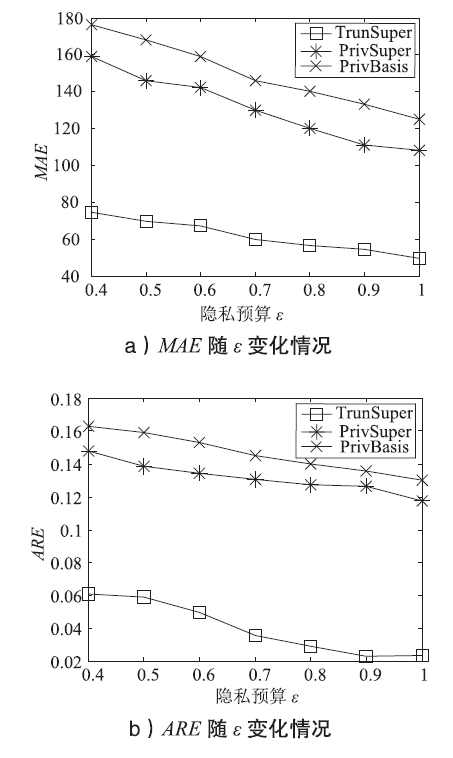
WANG Ning, XIAO Xiaokui, YANG Yin, et al.PrivSuper: A Superset-first Approach to Frequent Itemset Mining under Differential Privacy[C]//IEEE. IEEE 3rd International Conference on Data Engineering, April 19-22, 2017, San Diego, CA, USA. New Jersey: IEEE, 2017: 809-820.
|
| [7] |
BHASKAR R, LAXMAN S, THAKURTA A.Discovering Frequent Patterns in Sensitive Data[C]//ACM. 16th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, July 25-28, 2010, Washington, DC, USA. New York: ACM, 2010: 503-512.
|
| [8] |
LI Ninghui, QARDAJI W, SU Dong, et al.PrivBasis: Frequent Itemset Mining with Differential Privacy[J]. VLDB Endowment, 2012, 5(11): 1340-1351.
|
| [9] |
ZENG Chen, NAUGHTON J F, CAI Jinyi.On Differentially Private Frequent ItemsetMining[J]. VLDB Endowment, 2012, 6(1): 25-36.
|
| [10] |
DWORK C, MCSHERRY F, NISSIM K, et al.Calibrating Noise to Sensitivity in Private Data Analysis[J]. VLDB Endowment, 2006, 7(8): 637-648.
|
| [11] |
MCSHERRY F.Mechanism Design via Differential Privacy[C]//IEEE. The 48th Annual IEEE Symposium on Foundations of Computer Science, October 21-23, 2007, Washington, DC, USA. New Jersey: IEEE, 2007: 94-103.
|
| [12] |
GHORBANI M, ABESSI M.A New Methodology for Mining Frequent Itemsets on Temporal Data[J]. IEEE Transactions on Engineering Management, 2017, 64(4): 566-573.
|
| [13] |
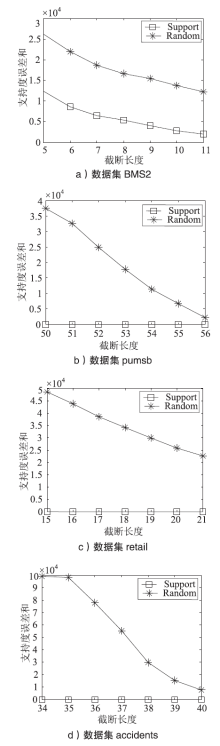
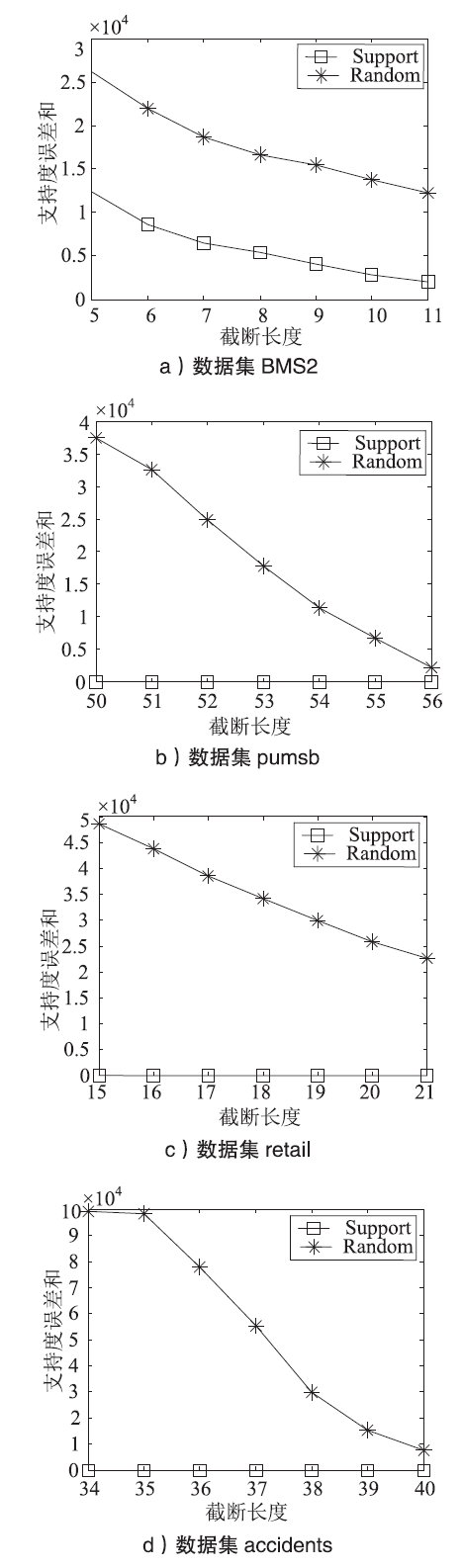
GAN Wenyong, WU Yingjie, SUN Lan, et al.Frequent Pattern Mining with Differential Privacy Based on Transaction Truncation[J]. Journal of Chinese Computer Systems, 2015, 36(11): 2583-2587.
|
|
甘文勇,吴英杰,孙岚,等.基于事务截断的差分隐私频繁模式挖掘算法[J].小型微型计算机系统,2015,36(11):2583-2587.
|
| [14] |
ZHANG Xiaojian, WANG Miao, MENG Xiaofeng.An Accurate Method for Mining Top-k Frequent Pattern Under Differential Privacy[J]. Journal of Computer Research and Development, 2014, 51(1): 104-114.
|
|
张啸剑,王淼,孟小峰.差分隐私保护下一种精确挖掘top-k频繁模式方法[J].计算机研究与发展,2014,51(1):104-114.
|
| [15] |
SU Sen, XU Shengzhi, CHENG Xiang, et al.Differentially Private Frequent Itemset Mining via Transaction Splitting[J]. IEEE Transactions on Knowledge & Data Engineering, 2015, 27(7): 1875-1891.
|
| [16] |
CHENG Xiang, SU Sen, XU Shengxiang, et al. DP-Apriori: A Differentially Private Frequent Itemset Mining Algorithm Based on Transaction Splitting[EB/OL]. , 2018-9-10.
|
| [17] |
DING Liping, LU Guoqing.Survey of Differential Privacy in Frequent Pattern Mining[J]. Journal on Communications, 2014, 35(10): 200-209.
|
 ), Geng YANG1,2, Yunlu BAI1,3, Junmei MA4
), Geng YANG1,2, Yunlu BAI1,3, Junmei MA4