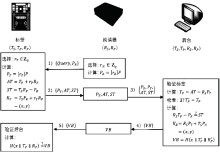
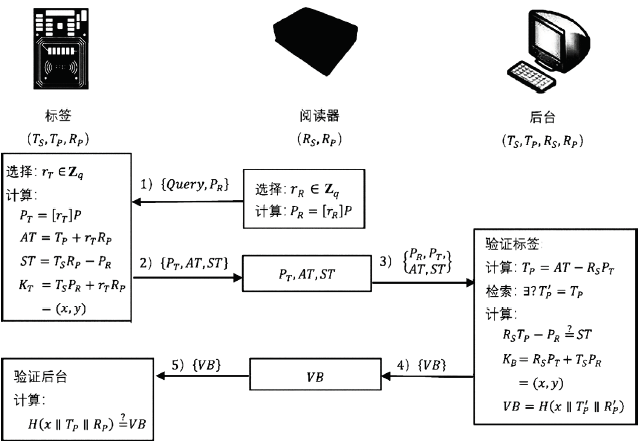
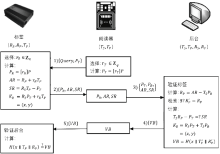
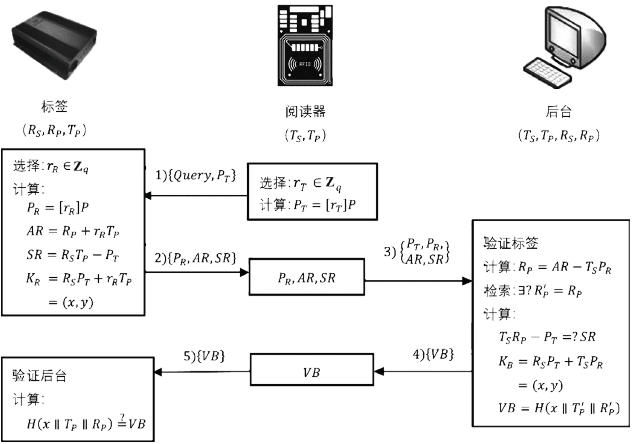
| [1] |
SHEN Han, SHEN Jian, MUHAMMAD K K, et al.Efficient RFID Authentication Using Elliptic Curve Cryptography for the Internet of Things[J]. Wireless Personal Communications, 2017, 96(4): 5253-5266.
|
| [2] |
HUO Weiguang, DONG Qingkuan, CHENG Yuan.ECC-based RFID/NFC Mutual Authentication Protocol[C]//IWMECS. 2nd International Workshop on Materials Engineering and Computer Sciences(IWMECS 2015), October 10-11, 2015, Jinan, China. Paris:IWMECS, 2015: 169-177.
|
| [3] |
PAN Yaomin, SHAN Zheng, DAI Qing, et al.CPK-ECC-based Mutual Authentication Protocol for Large-scale RFID System[J]. Journal on Communications, 2017, 38(8): 165-171.
|
|
潘耀民,单征,戴青,等.大规模RFID系统中基于CPK-ECC的双向认证协议[J].通信学报,2017,38(8):165-171.
|
| [4] |
BATINA L, GUAJARDO J, KERINS T, et al.Public-key Cryptography for RFID-tags[C]//IEEE. Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops(PerComW’7), March 19-23, 2007, White Plains, NY, USA. NJ: IEEE, 2007: 217-222.
|
| [5] |
LEE Y K, BATINA L, VERBAUWHEDE I.EC-RAC(ECDLP-based Randomized Access Control): Provably Secure RFID Authentication Protocol[C]//IEEE. 2008 IEEE International Conference on RFID, April 16-17, 2008, Las Vegas, NV, USA. NJ: IEEE, 2008: 97-104.
|
| [6] |
ZHANG Xinglei, LI Linsen, WU Yue, et al.An ECDLP-based Randomized Key RFID Authentication Protocol[C]//IEEE. 2011 International Conference on Network Computer and Computing and Information Security(NCIS), May 14-15, 2011, Guilin, China. NJ: IEEE, 2011: 146-149.
|
| [7] |
MOOSAVI S R, NIGUSSIE E, VIRTANEN S, et al.An Elliptic Curve-based Mutual Authentication Scheme for RFID Implant Systems[J]. Procedia Computer Science, 2014, 32: 198-206.
|
| [8] |
LIAO Yipin, HSIAO C M.A Secure ECC-based RFID Authentication Scheme Integrated with ID-verifier Transfer Protocol[J]. Ad Hoc Networks, 2014, 18: 133-146.
|
| [9] |
RYU E K, KIM D S, YOO KY.On Elliptic Curve Based Untraceable RFID Authentication Protocols[C]//ACM. The 3rd ACM Workshop in Information Hiding and Multimedia Security, June 17-19, 2015, Portland, Oregon, USA. New York: ACM, 2015: 147-153.
|
| [10] |
KANG Hongyan.Analysis and Improvement of Grouping-proof Protocol for RFID Based on ECC[J]. International Journal of Control and Automation. 2013, 39(1): 153-156, 163.
|
|
康鸿雁. 基于ECC的RFID组证明协议分析及改进[J].计算机工程,2013,39(1):153-156,163.
|
| [11] |
ALAMR A A, KAUSAR F, KIM J, et al.A Secure ECC-based RFID Mutual Authentication Protocol for Internet of Things[J]. Journal of Supercomputing, 2018, 74(9): 4281-4294.
|
| [12] |
ZHENG Lijuan, XUE Yujuan, ZHANG Linhao, et al.Mutual Authentication Protocol for RFID-based on ECC[C]//IEEE. 20th IEEE International Conference on Computational Science and Engineering(CSE) and/ 15th IEEE/IFIP International Conference on Embedded and Ubiquitous Computing(EUC), July 21-24, 2017, Guangzhou, China. NJ: IEEE, 2017: 320-323.
|
| [13] |
WANG Huanbao, ZHANG Yousheng, HOU Zhengfeng.Strand Space Model to Prove the Security of Cryptographic Protocols[J]. Journal of Hefei University of Technology(Natural Science), 2005, 28(5): 449-455.
|
|
王焕宝,张佑生,侯整风.用于密码协议安全性证明的串空间模型[J]. 合肥工业大学学报(自然科学版),2005,28(5):449-455.
|
| [14] |
DING Mengwei, ZHOU Qinglei, ZHAO Dongming.Strand Space Model of Yahalom-Paulson Protocol and Its Analysis[J]. Computer Engineering and Applications, 2008, 44(22): 97-99, 103.
|
|
丁萌伟,周清雷,赵东明. Yahalom-Paulson协议的串空间模型与分析[J].计算机工程与应用,2008,44(22):97-99,103.
|
| [15] |
TAN Lili, LIU Jing, XIE Hongbo, et al.Theory and Application of Strand Spaces Model[J]. Journal of Computer Applications, 2005, 25(8): 1747-1749, 1752.
|
|
谭立力,刘璟,谢鸿波,等.串空间模型的原理与应用[J].计算机应用,2005,25(8):1747-1749,1752.
|
| [16] |
THAYER F J, HERZOG J C, GUTTMAN J D.Strand Spaces: Honest Ideals on Strand Spaces[C]//IEEE. The 11th IEEE Workshop on Computer Security Foundations, June 9-11, 1998, Rockport, MA, USA. New York: ACM, 1998: 66-77.
|
| [17] |
ZHAO Zhengguo.A Secure RFID Authentication Protocol for Healthcare Environments Using Elliptic Curve Cryptosystem[J]. Journal of Medical Systems, 2014, 38(5): 46.
|
| [18] |
LIU Guoliang, ZHANG Huichuan, KONG Fanyue, et al.A Novel Authentication Management RFID Protocol Based on Elliptic Curve Cryptography[J]. Wireless Personal Communications, 2018, 101(3): 1445-1455.
|
 ), Jianhua CHEN1, Yongmei WEI2
), Jianhua CHEN1, Yongmei WEI2