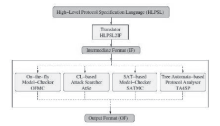
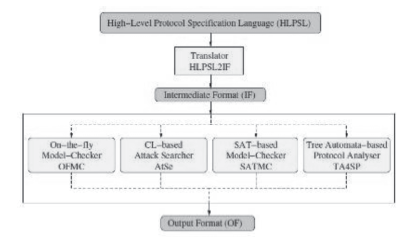
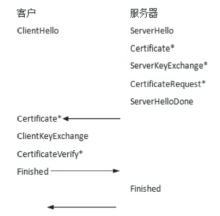
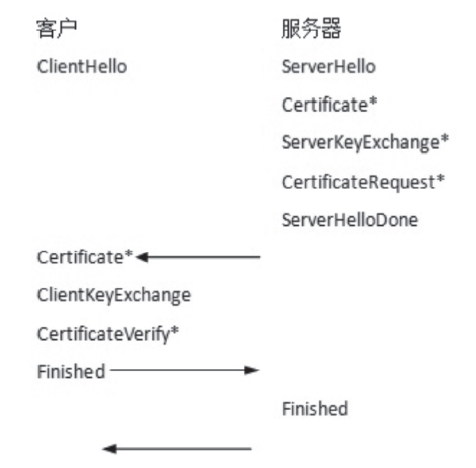
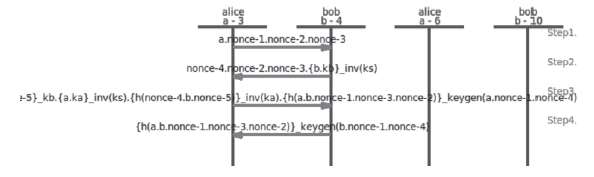
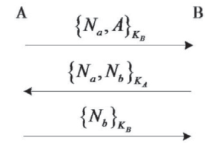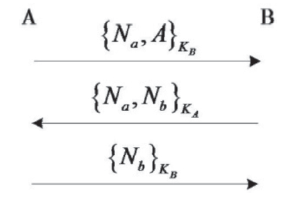| [1] |
Nachiketh R. Potlapally, Srivaths Ravi, Anand Raghunathan, Niraj K. Jha. A Study of the Energy Consumption Characteristics of Crytographic Algorithms and Security Protocols[J]. IEEE Transactions on mobile computing, 2006,5(2): 128-143.
|
| [2] |
Luca Vigano.Automated Security Protocol Analysis With the AVISPA Tool[C]//Electronic Notes in Theoretical Computer Science. Zurich:Elsevier,2006: 61-86.
|
| [3] |
Stefanos Gritzalis, Diomidis Spinellis.A taxonomy of flaws and related protocol analysis tools[C]//The 16th International Conference on Computer Safety, Reliability and Security. London:Springer-Verlag, 1997:123-137.
|
| [4] |
Xu Wei, Ma Yan, Liu Nan, Wu Dong-ying.A Formal Method for Analyzing Fair Exchange Protocols[C]//2009 WASE International Conference on Information Engineering. Taiyuan:IEEE,2009:645-652.
|
| [5] |
Laifeng Lu, Jianfeng Ma.Formal Analysis Model of Security Protocol Based on PCL[C]//2010 International Conference on Computer Application and System Modeling. Taiyuan:IEEE,2010:658-660.
|
| [6] |
Takahiro Minamikawa, Tatsuhiro Tsuchiya, Tohru Kikuno.Towards Automated Verification of Distributed Consensus Protocols[C]//2009 16th Asia-Pacific Software Engineering Conference. Penang:IEEE, 2009:276-291.
|
| [7] |
Peter Bokor, Johannes Kinder, Marco Serafini, Neeraj Suri.Efficient Model Checking of Fault-Tolerant Distributed Protocols[C]//2011 IEEE/IFIP 41st International Conference. Hong Kong:IEEE, 2011:63-72.
|
| [8] |
AVISPA Team. AVISPA V1.1 UserManual[N]. Information Society Technologies, 2014-1-20.
|
| [9] |
Wang Zhenzhong, Wang Yao.An Improvement SSL Protocol Application Research[C]//2011 International Conference on Electronic & Mechanical Engineering and Information Technology. Heilongjiang:IEEE, 2011:4010-4013.
|
| [10] |
Abdelmajid N.T., Hossain M.A., Shepherd, Mahmoud. Improved Kerberos Security Protocol Evaluation using Modified BAN Logic[C]//2010 10th IEEE Internatioinal Conference on Computer and Information Technology. Bradford:IEEE, 2010:1610-1615.
|
 )
)