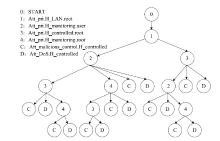
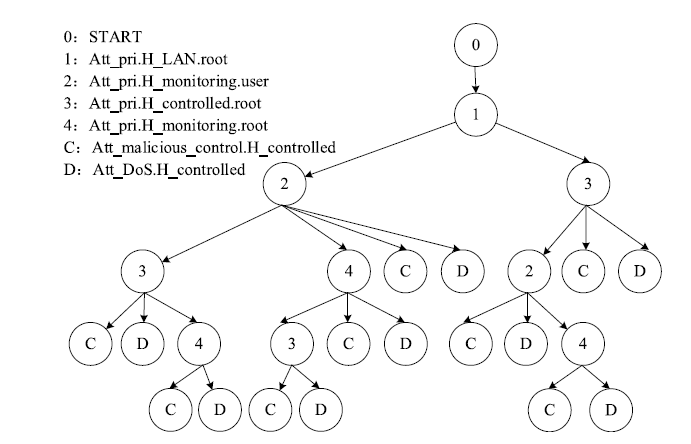
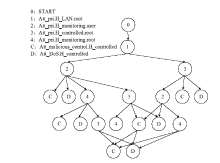
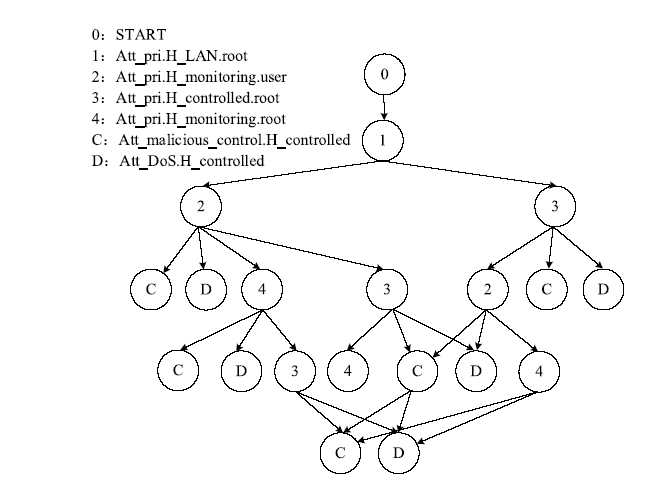
| [1] |
LIU Wei, LI Dong, SUN Bo.ICS Security Analysis[J]. Netinfo Security, 2012, 12(8): 41-43.
|
|
刘威,李冬,孙波. 工业控制系统安全分析[J]. 信息网络安全,2012,12(8):41-43.
|
| [2] |
YANG An, SUN Limin, WANG Xiaoshan, et al.Intrusion Detection Techniques for Industrial Control Systems[J]. Journal of Computer Research and Development, 2016, 53(9): 2039-2054.
|
|
杨安,孙利民,王小山,等. 工业控制系统入侵检测技术综述[J]. 计算机研究与发展,2016,53(9):2039-2054.
|
| [3] |
WANG Xiaoshan, YANG An, SHI Zhiqiang, et al.New Trend of Information Security in Industrial Control Systems[J]. Netinfo Security, 2015, 15(1): 6-11.
|
|
王小山,杨安,石志强,等. 工业控制系统信息安全新趋势[J]. 信息网络安全,2015,15(1):6-11.
|
| [4] |
LU Jijun, HUANG Liusheng, WU Shufeng.An Attack Tree Approach for Network Intrusion Modeling[J]. Computer Engineering and Applications, 2003, 39(27): 160-163.
|
|
卢继军,黄刘生,吴树峰. 基于攻击树的网络攻击建模方法[J]. 计算机工程与应用,2003,39(27):160-163.
|
| [5] |
LI Hui, ZHANG Ru, LIU Jianyi, et al.Safety Assessment on Digital Radio Transmission Based on Attack Tree Model[J]. Netinfo Security, 2014, 14(8): 71-76.
|
|
李慧,张茹,刘建毅,等. 基于攻击树模型的数传电台传输安全性评估[J]. 信息网络安全,2014,14(8):71-76.
|
| [6] |
YUAN Jinming.Research on Attack Graph Generation for Industrial Control Network Security and Vulnerability[J]. Modern Electronics Technique, 2016, 39(11): 103-107.
|
|
原锦明. 面向工控网络安全和漏洞分析的攻击图生成研究[J]. 现代电子技术,2016,39(11):103-107.
|
| [7] |
PRASAD K, KUMAR S, NEGI A, et al. Generation and Risk Analysis of Network Attack Graph[EB/OL]. .
|
| [8] |
CHEN Xiaojun, FANG Binxing, TAN Qingfeng.et al.Inferring Attack Intent of Malicious Insider Based on Probabilistic Attack Graph Model[J]. Chinese Journal of Computers, 2014, 37(1): 62-72.
|
|
陈小军,方滨兴,谭庆丰,等. 基于概率攻击图的内部攻击意图推断算法研究[J]. 计算机学报,2014,37(1):62-72.
|
| [9] |
CHEN Feng, MAO Handong, ZHANG Weiming, et al.Survey of Attack Graph Technique[J]. Computer Science, 2011, 38(11): 12-18.
|
|
陈锋,毛捍东,张维明,等. 攻击图技术研究进展[J]. 计算机科学,2011,38(11):12-18.
|
| [10] |
WU Di, LIAN Yifeng, CHEN Kai, et al.A Security Threats Identification and Analysis Method Based on Attack Graph[J]. Chinese Journal of Computers, 2012, 35(9): 1938-1950.
|
|
吴迪,连一峰,陈恺,等. 一种基于攻击图的安全威胁识别和分析方法[J]. 计算机学报,2012,35(9):1938-1950.
|
| [11] |
CHEN Feng, ZHANG Yi, SU Jinshu, et al.Two Formal Analyses of Attack Graphs[J]. Journal of Software, 2010, 21(4): 838-848.
|
|
陈锋,张怡,苏金树,等. 攻击图的两种形式化分析[J]. 软件学报,2010,21(4):838-848.
|
| [12] |
ZHANG Haixia, SU Purui, FENG Dengguo.A Network Security Analysis Model Based on the Increase in Attack Ability[J]. Journal of Computer Research and Development, 2007, 44(12): 2012-2019.
|
|
张海霞,苏璞睿,冯登国. 基于攻击能力增长的网络安全分析模型[J]. 计算机研究与发展,2007,44(12):2012-2019.
|
| [13] |
JHA S, SHEYNER O, WING J. Two Formal Analyses of Attack Graphs[EB/OL]. .
|
 ), Zemao CHEN1, Hao WANG2
), Zemao CHEN1, Hao WANG2