Netinfo Security ›› 2016, Vol. 16 ›› Issue (7): 7-8.doi: 10.3969/j.issn.1671-1122.2016.07.002
• Orginal Article • Previous Articles Next Articles
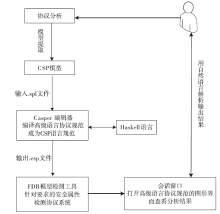
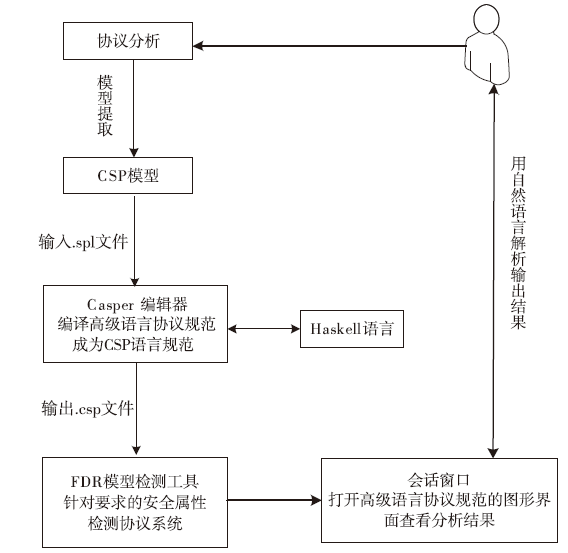
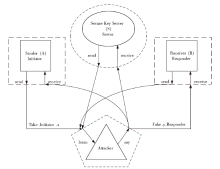
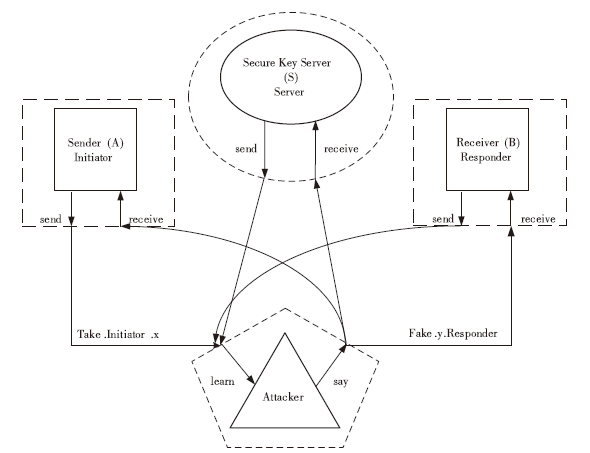
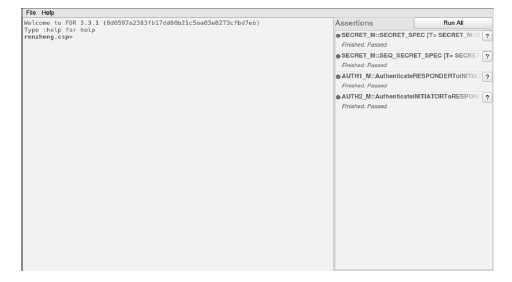
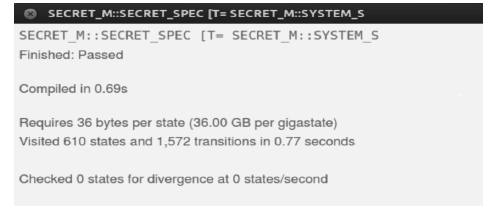
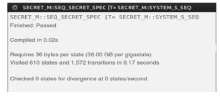
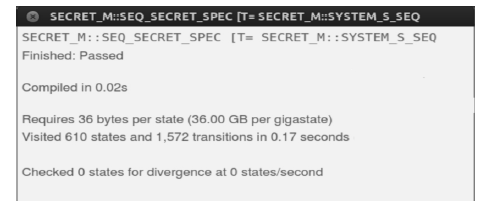
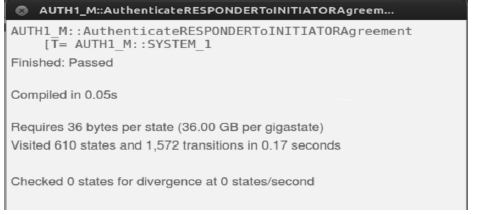
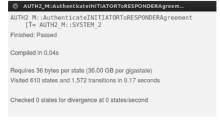
RSSP-II Protocol Security Analysis Based on Communicating Sequential Process Method
Debiao LU, Shengjiao HE, Jian WANG
- College of Electric Information Engineering, Beijing Jiaotong University,Beijing 100044, China