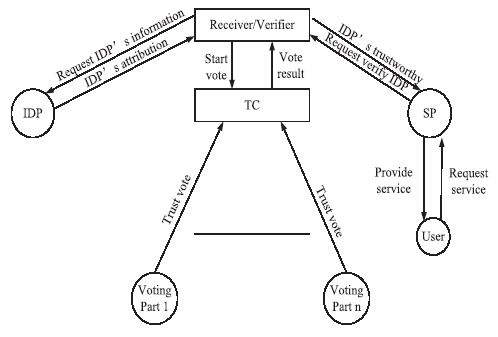
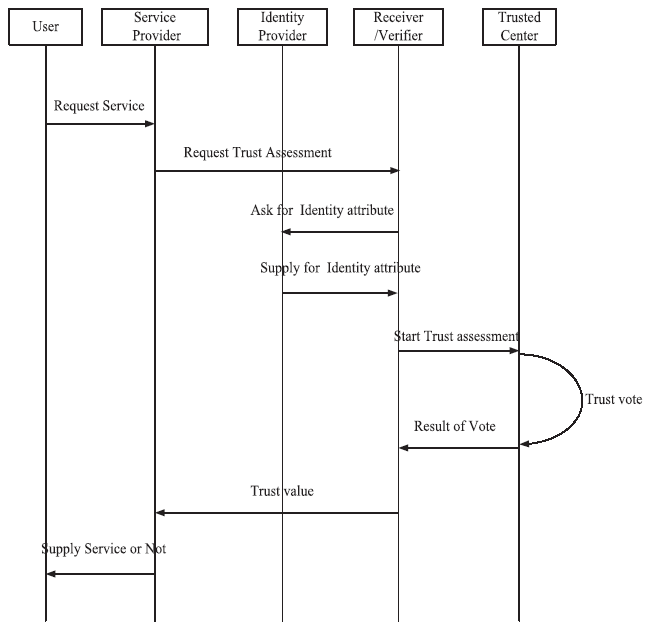
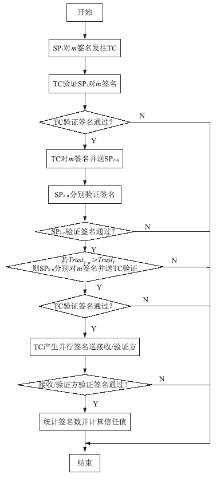
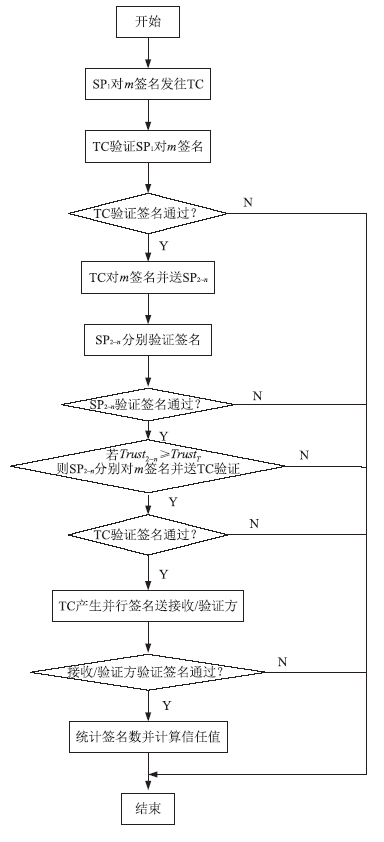
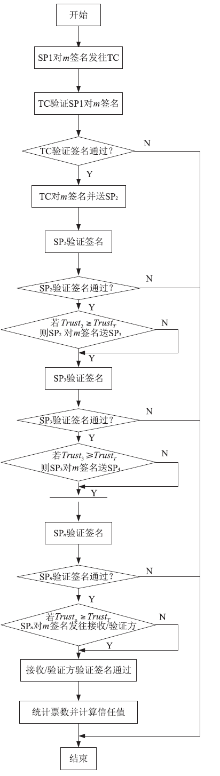
| [1] |
ABHILASHA BHARGAV-SPANTZEL,ANNAC.SQUICCIARINI,AND ELISA BERTINO.Trust Negotiation in Identity Management[J]. Security & Privacy, 2007,5(2) :55-63
|
| [2] |
Rajarajan Sampath, Deepak Goel.RATING: Rigorous Assessment of Trust in Identity Management[C]//Proceedings of the First International Conference on Availability, Reliability and Security. IEEE COMPUTER SOCIETY, 2006 : 10-19.
|
| [3] |
Altmann, J. Sampath, R. UNIQuE: A User-Centric Framework for Network Identity Management[C]//Network Operations and Management Symposium. 10th IEEE/IFIP, 10.1109/NOMS. 2006: 495-506
|
| [4] |
Daeseon Choi,Seung-Hun Jin and Hyunsoo Yoon. Trust Management for User-Centric Identity Management on the Internet[C]// ISCE 2007, IEEE International Symposium. Consumer Electronics, 2007:1-4.
|
| [5] |
李建,周化钢,彭越,等. 以用户为中心的可信终端身份管理模型[J], 信息网络安全,2014,(4):1-6
|
| [6] |
李建,王青龙,沈昌祥,等. 无单向Hash函数的数字多签名方案[J]. 计算机工程与设计,2008.29(8):1938-1941.
|
| [7] |
M. Burmester, Y. Desmedt, Hiroshi Doi, et al. A Structured ElGamal-Type Multisignature Scheme[J]. PKC2000, 2000,LNCS1751: 466-483.
|
| [8] |
袁艳祥,游林. 基于身份加密的可认证密钥协商协议[J]. 信息网络安全,2014,(3):1-6.
|
| [9] |
Mitsuru Tada.An Order-Specified Multisignature Scheme Secure Against Active Insider Attacks[C]//L. Batten, J. Seberry. ACISP2002. Melbourne: Springer Berlin/Heidelberg 2002: 57-106.
|
| [10] |
王标,陈持协,孙谋,等. 环Zn上广义圆锥曲线多重数字签名方案的分析与改进[J]. 信息网络安全,2014,(4):60-63.
|
| [11] |
Gangishetti R, choudary Gorantla M, Lal Das M, et al. Identity Based Multisignatures[J]. IOS press, 2006, 17( 2) : 177-186.
|
| [12] |
Bart De Decker, Frank Piessens, Jan Smith, et al.Advances in Network and Distributed Systems Security[M]. Boston :Springer, 2002.
|
| [13] |
C. C. Chang, E.-H. Lu, S.-F. Pon, and J.-Y. Lee, Applying Harn-Kiesler multisignature scheme to electronic document systems[C]// Proc. National Information Security Conf., R.O.C., 1995: 35-38.
|
| [14] |
L. Harn, T. Kiesler, New scheme for digital multisignature[J].Electron. Lett,1989, 25(15): 1002-1003.
|
| [15] |
Kiesler, T. Harn, L. RSA blocking and multisignature schemes with no bit expansion[J]. Electron. Lett, 1990,26(18):1490-1491.
|
| [16] |
Okamoto T, A digital multisignature scheme using bijective public-key cryptosystems[J]. ACM Trans. Comput. Syst,1988, 6(8) :432-441.
|
| [17] |
S.-P. Shieh, C.-T. Lin, W.-B. Yang, et al. Digital multisignature schemes for authenticating delegates in mobile code systems[J]. IEEE Trans. Veh. Technol, 2000, (49): 1464-1473.
|
| [18] |
Harn L.New digital signature scheme based on discrete logarithm[J]. Electronics Letters, 1994, 30(5): 296-298.
|
| [19] |
S.-J. Hwang, E.-T. Li. Cryptanalysis of Shieh-Lin-Yang-Sun signature scheme[J]. IEEE Commun. Lett, 2003, (7): 195-199.
|
| [20] |
Chin-Chen Chang, Ya-Fen Chang.Signing a Digital Signature Without Using One-Way Hash functions and Message Redundancy Schemes[J]. IEEE Commun. Lett, 2004, (8): 485-487.
|
| [21] |
Fang-guo Zhang. ryptanalysis of Chang et al. s Signature Scheme with Message Recovery[EB/OL]. , 2006-3-16.
|
 ), GUAN Wei-li3, LIU Ji-qiang1, WU Xing3
), GUAN Wei-li3, LIU Ji-qiang1, WU Xing3