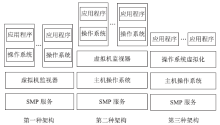
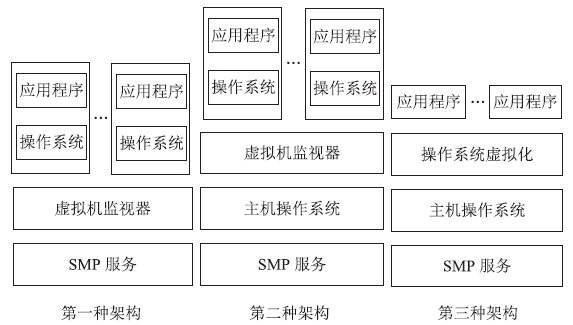
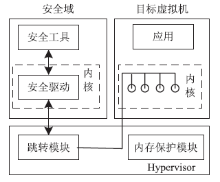
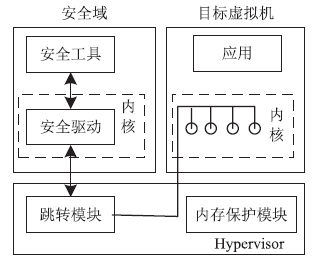
| [1] |
蒋万春,汤立,等. 虚拟化安全问题探析[J]. 信息网络安全,2010(8):83-86.
|
| [2] |
肖斐. 虚拟化云计算中资源管理的研究与实现[D]. 西安:西安电子科技大学,2010.
|
| [3] |
章恒,禄凯. 构建云计算环境的安全检查与评估指标体系[J]. 信息网络安全,2014(9):115-119.
|
| [4] |
冯登国. 可证明安全性理论与方法研究[J]. 软件学报,2005(16):1743-1756.
|
| [5] |
张显龙. 云计算安全总体框架与关键技术研究[J]. 信息网络安全,2013(7):28-31.
|
| [6] |
陈驰,于晶. 云计算安全体系[M]. 北京:科学出版社,2014.
|
| [7] |
SHINAGAWA T, EIRAKU H, TANIMOTO K, et al.Bitvisor: A Thin Hypervisor for Enforcing I/O Device Security[C]//ACM. 5th International Conference on Virtual Execution Environments, March 11-13, Washington, DC, USA. New York: ACM, 2009: 121-130.
|
| [8] |
STEINBERG U, KAUER B.NOVA: A Microhypervisor-based Secure Virtualization Architecture[C]//ACM. 5th European Conference on Computer Systems, April 13-16, 2010, Paris, France. New York: ACM, 2010: 209-222.
|
| [9] |
林昆,黄征. 基于Intel VT-d技术的虚拟机安全隔离研究[J]. 信息安全与通信保密,2011(5):101-103.
|
| [10] |
PAYNE B D, CARBONE M, SHARIF M, et al.Lares: An Architecture for Secure Active Monitoring Using Virtualization[C]//IEEE. 29th IEEE Symposium on Security and Privacy, May 18-22, 2008, Washington, DC, USA. New Jersey: IEEE, 2008: 233-247.
|
| [11] |
GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. , 2016-5-13.
|