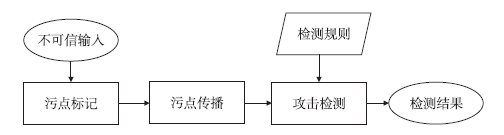
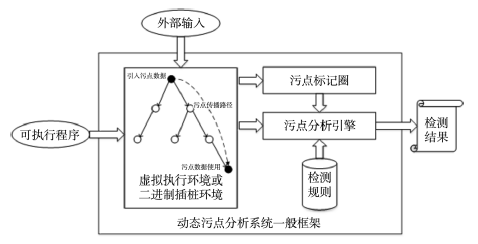
| [1] |
United States Federal Law. National Defense Authorization Act for Fiscal[EB/OL]. ,2015-10-15.
|
| [2] |
LAM M S, MARTIN M, LIVSHITS B, et al.Securing Web Applications with Static and Dynamic Information Flow Tracking[C]//ACM.The ACM SIGPLAN Symposium on Partial Evaluation and Semantics-based Program Manipulation, January 7-8, 2008,San Francisco, California, USA. New York:ACM,2008:2-3.
|
| [3] |
NEWSOME J, SONG D.Dynamic Taint Analysis for Automatic Detection, Analysis and Signature Generation of Exploits on Commodity Software[C]// NDSS '05. 12th Network and Distributed Systems Security Symposium, February 3-4 2005 ,San Diego,California. New York: ISOC,2005:1-14.
|
| [4] |
CLAUSE J, LI W, ORSO A.Dytan: A Generic Dynamic Taint Analysis Framework[C]//ACM.2007 International Symposium on Software Testing and Analysis, July 9-12, 2007,London, United Kingdom. New York:ACM,2007:196-206.
|
| [5] |
SONG D, BRUMLEY D, YIN H, et al.BitBlaze: A New Approach to Computer Security via Binary Analysis[C]// ICISS .4th International Conference on Information Systems Security, December 16-20, 2008, Hyderabad, India . Heidelberg:Springer,2008:1-25.
|
| [6] |
KEMERLIS V P, PORTOKALIDIS G, JEE K, et al.Libdft: Practical Dynamic Data Flow Tracking for Commodity Systems[J].Acm Sigplan Notices, 2002, 47(7):121-132.
|
| [7] |
DUMITRU C.Detecting Software Vulnerabilities Static Taint Analysis [D].Bucharest : University Politehnica of Bucharest, 2009.
|
| [8] |
CIFUENTES C. SCHOLZ B.Parfait-Designing a Scalable Bug Checker[C]//SAW '08. 2008 workshop on Static Analysis,June 7 - 13, 2008,Tucson, Arizona. New York:ACM,2008: 4-11.
|
| [9] |
JOVANOVIC N, KRUEGEL C, KIRDA E.Pixy: A Static Analysis Tool for Detecting Web Application Vulnerabilities[C]//IEEE. IEEE Symposium on Security and Privacy, May 21-24, 2006, Oakland, California . New Jersey: IEEE ,2006: 258-263.
|
| [10] |
DENNING D E.A Lattice Model of Secure Information Flow[J]. Communication of the ACM, 1976, 19(5):236-253.
|
| [11] |
代伟,刘智,刘益和. 基于二进制代码的动态污点分析[J]. 计算机应用与研究, 2014, 31(8):2497-2505.
|
| [12] |
NETHERCOTE N, SEWARD J.Valgrind: A Framework for Heavyweight Dynamic Binary Instrumentation[J]. ACM Sigplan Notices,2007, 42(6):89-100.
|
| [13] |
NEWSOME J, MCCAMANT S, SONG D.Measuring Channel Capacity to Distinguish Undue Influence[C]// ACM .2009 ACM SIGPLAN Fourth Workshop on Programming Languages and Analysis for Security(PLAS), June 15-20,2009,Dublin, Ireland. New York:ACM,2009: 73-85.
|
| [14] |
YIN H, SONG D, EGELE M, et al.Panorama: Capturing System-wide Information Flow for Malware Detection and Analysis[C]//ACM.14th ACM conference on Computer and Communications Security,October 29,2007,Alexandria,VA. New York:ACM,2007:116-127.
|
| [15] |
PORTOKALIDIS G, SLOWINSKA A, BOS H. Argos: An Emulator for Fingerprinting Zero-Day Attacks[EB/OL]..
|
| [16] |
PORTOKALIDIS G, BOS H.Eudaemon: Involuntary and On-Demand Emulation Against Zero-Day Exploits[C]// ACM. EuroSys 2008,April 2-4,2008,Glasgow, Scotland. New York:ACM,2008:287-299.
|
| [17] |
CHOW J, PFAFF B, GARFINKEL T, et al.Understanding Data Lifetime via Whole System Simulation[C]//Usenix. 13th Usenix Security Symposium, August 9-13, 2004, San Diego, CA. Berkeley:Usenix , 2004: 321-336.
|
| [18] |
ZHU D, JUNG J, SONG D, et al.TaintEraser: Protecting Sensitive Data Leaks Using Application-Level Taint Tracking[J].Acm Sigops Operating Systems Review, 2011, 45(1):142-154
|
| [19] |
EGELE M, KRUEGEL C, KIRDA E, et al. Dynamic Spyware Analysis[EB/OL]. .
|
| [20] |
SUH G E, LEE J W, ZHANG D, et al. Secure Program Execution via Dynamic Information Flow Tracking[EB/OL]. .
|
| [21] |
SHIYI W, RYDER B G.Practical Blended Taint Analysis for JavaScript[C]// ACM.2013 International Symposium on Software Testing and Analysis,July 15-20,2013,Lugano,Switzerland. New York:ACM,2013:336-346.
|
| [22] |
INIAN P, ENRICO B, SHWETA S, et al.DexterJS: Robust Testing Platform for DOM-based XSS Vulnerabilities[C]//ESEC/FSE,2015 10th Joint Meeting on Foundations of Software Engineering, August 30- September 4, 2015, Bergamo,Italy. New York:ACM, 2015:946-949.
|
| [23] |
NENTWICH F, JOVANOVIC N, KIRDA E, et al. Cross-site Scripting Prevention with Dynamic Data Tainting and Static Analysis[EB/OL].,2015-10-15.
|
| [24] |
JONATHAN B, GAIL K. Phosphor: Illuminating Dynamic Data Flow in Commodity JVMs[EB/OL].,2015-1-11.
|
| [25] |
ERIKA C, DAVID W, Efficient Character-level Taint Tracking for Java[C]//ACM.2009 ACM Workshop on Secure Web Services,November 9-13, 2009,Chicago, IL. New York:ACM,2009:3-12.
|
| [26] |
MCCLURG J, FRIEDMAN J, NG W. Android Privacy Leak Detection via Dynamic Taint Analysis[EB/OL]..
|
| [27] |
WILLIAM E, PETER G, BYUNG-GON C, et al.TaintDroid: An Information-flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2010, 57(3):393-407.
|
| [28] |
GANESH V, LEEK T, RINARD M.Taint-based Directed Whitebox Fuzzing[C]//IEEE.31st International Conference on Software Engineering( ICSE), May 16-24 2009, Vancouver, BC. New Jersey:IEEE, 2009: 474-484
|
| [29] |
WANG T L, WEI T, GU G, ZOU W.Checksum-Aware Fuzzing Combined with Dynamic Taint Analysis and Symbolic Execution[J]. ACM Transactions on Information and System Security (TISSEC), 2011, 14(2):613.
|
| [30] |
陈力波,诸葛建伟,田繁,等.基于类型的动态污点分析技术研究[C]//中国信息安全测评中心.第五届信息安全漏洞分析与风险评估大会(VARA)论文集,2012-12-26,上海.北京:中国信息安全测评中心,2012:195-214.
|
| [31] |
GANAI M, LEE D, GUPTA A.DTAM: Dynamic Taint Analysis of Multi-threaded Programs for Relevancy[C]//ACM.ACM SIGSOFT 20th International Symposium on the Foundations of Software Engineering, November 11-16 ,2012,Cary, North Carolina. New York:ACM,2012:1-11.
|
| [32] |
CHABBI M. Efficient Dynamic Taint Analysis Using Multicore Machines[EB/OL]. ,2015-07-20.
|
| [33] |
HO A, FETTERMAN M, CLARK C, et al.Practical Taint-based Protection Using Demand Emulation[J]. EuroSys, 2006, 40(4): 29-41.
|
 )
)