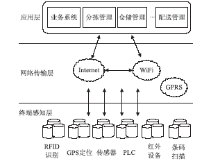
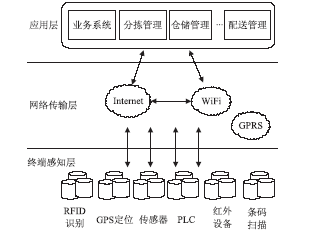
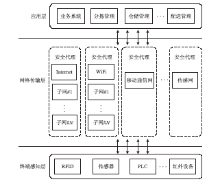
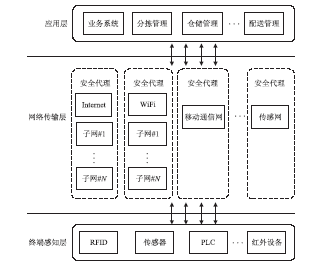
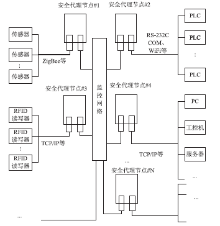
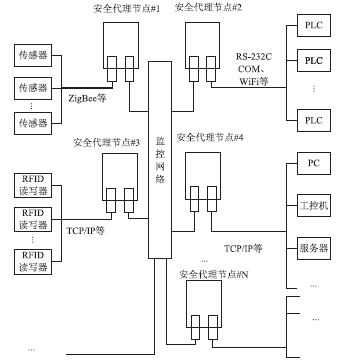
| [1] |
孙其博,刘杰,黎羴,等. 物联网:概念、架构与关键技术研究综述[J]. 北京邮电大学学报,2010,33(3):1-9.
|
| [2] |
中国科技网. IEEE 1888标准:全球能源互联网有了中国主导的国际标准[EB/OL]. .
|
| [3] |
ITU-T.Y. 2002-2009. Overview of ubiquitous networking and of its support in NGN[S]. Geneva: 2010.
|
| [4] |
GRANJAL J, MONTEIRO E, SILVA J S.Security in the integration of low-power Wireless Sensor Networks with the Internet: A survey[J]. Ad Hoc Networks, 2015, (24): 264-287.
|
| [5] |
AGGARWAL R, DAS M L.RFID Security in the Context of "Internet of Things"[C]// Proceedings of the First International Conference on Security of Internet of Things. New York, 2012.
|
| [6] |
LI C, ZHANG J.Research of ZigBee's Data Security and Protection[C]//IFCSTA '09. International Forum on IEEE, 2009: 298-302.
|
| [7] |
BARKER R.Security aspects in 6LowPan networks[C]//Proceedings of the Conference on Design. Automation and Test in EuropeEuropean Design and Automation Association, 2010: 660-660.
|
| [8] |
王景中,凌晨. 基于节点认证的物联网感知层信息安全传输机制的研究[J]. 信息网络安全,2014,(2):53-57.
|
| [9] |
张鸿亮,刘文予,符明丽. 基于需求等级的传感器网络安全策略模型[J]. 微计算机信息,2008,24(13):134-136.
|
| [10] |
许开立,陈全. 安全等级特征量及其计算方法[J]. 中国安全科学学报,1999,9(6):6-12.
|
| [11] |
GARFINKEL S L, JUELS A, PAPPU R.RFID privacy: an overview of problems and proposed solutions[J]. Security & Privacy, IEEE, 2005, 3(3): 34-43.
|
| [12] |
聂金慧,苏红旗. 物联网位置数据安全策略研究[J]. 信息网络安全,2014,(6):6-10.
|
| [13] |
范一鸣,屠雄刚. 一种基于谱聚类分析的物联网节点安全控制域划分算法[J]. 传感技术学报,2014,(5):675-679.
|
| [14] |
吴振强,周彦伟,马建峰. 物联网安全传输模型[J]. 计算机学报,2011,34(8):1351-1364.
|
| [15] |
SCHWARTAU W.Time-based security explained: Provable security models and formulas for the practitioner and vendor[J]. Computers & Security, 1998, 17(8): 693-714.
|
| [16] |
刘波,陈晖,王海涛,等. 物联网安全问题分析及安全模型研究[J]. 计算机与数字工程,2012,40(11):21-24.
|
| [17] |
孙知信,骆冰清,罗圣美,等. 一种基于等级划分的物联网安全模型[J]. 计算机工程,2011,37(10):1-7.
|
| [18] |
范红,邵华,李程远,等. 物联网安全技术体系研究[J]. 信息网络安全,2011,(9):5-8.
|
| [19] |
SAID O.Development of an Innovative Internet of Things Security System[J]. International Journal of Computer Science Issues, 2013, 10(6): 155-161.
|
| [20] |
WU M, LU T, LING F, et al.Research on the architecture of Internet of Things[C]//Advanced Computer Theory and Engineering (ICACTE), 2010 3rd International Conference on, 2010.
|
| [21] |
邵华,范红. 物联网信息安全模型综述[J]. 信息安全与技术,2014,(9):16-19.
|
| [22] |
陈达,马威,李晓勇. 一种单向安全隔离与信息交换机制[J]. 信息网络安全,2014,(6):48-52.
|
| [23] |
DOLEV D, STRONG H R.Authenticated Algorithms for Byzantine Agreement.[J]. SIAM JOURNAL ON COMPUTING, 1983, 12(4): 656-666.
|
| [24] |
NASH A, DUANE W, JOSEPH C.PKI: Implementing and Managing E-Security[M]. New York, NY, USA: McGraw-Hill, Inc., 2001.
|
| [25] |
何鹏程,方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全,2015,(1):61-65.
|