Netinfo Security ›› 2025, Vol. 25 ›› Issue (2): 327-336.doi: 10.3969/j.issn.1671-1122.2025.02.012
Previous Articles Next Articles
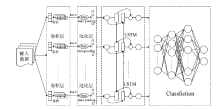
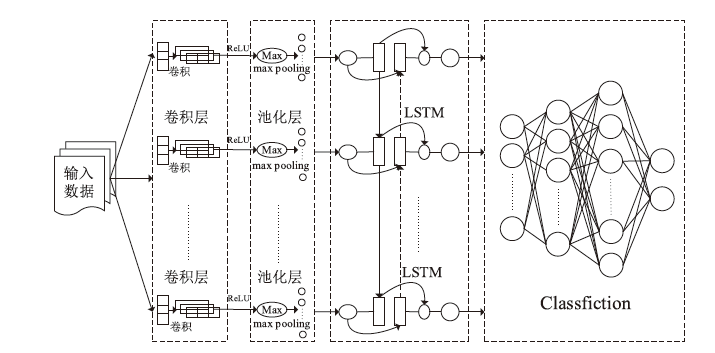
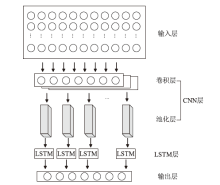
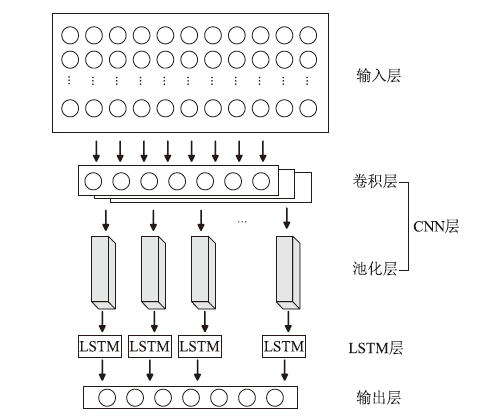
CNN-LSTM Algorithm-Based Insider Threat Detection Model
YANG Menghua, YI Junkai, ZHU Hejun( )
)
- School of Automation, Beijing Information Science and Technology University, Beijing 100085, China
-
Received:2024-12-03Online:2025-02-10Published:2025-03-07
CLC Number:
Cite this article
YANG Menghua, YI Junkai, ZHU Hejun. CNN-LSTM Algorithm-Based Insider Threat Detection Model[J]. Netinfo Security, 2025, 25(2): 327-336.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.02.012
| 符号 | 定义 |
|---|---|
| 内部人员集合,其中 | |
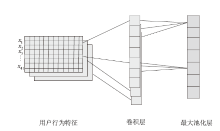
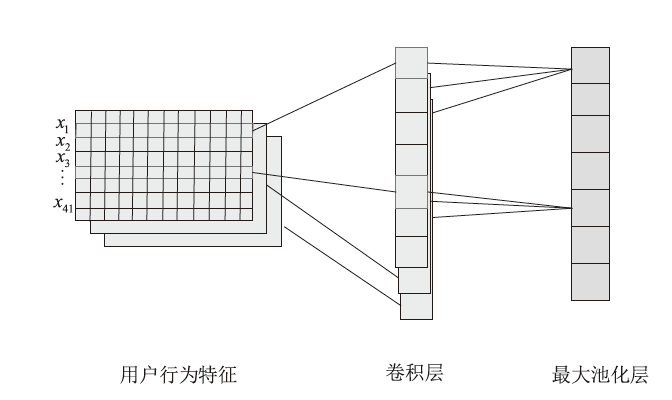
| 用户行为特征序列集合, | |
| 输入数据的批量大小,模型训练迭代中处理的样本数量,在本文实验中,批量大小设置为64 | |
| 时间步长,表示输入数据中每个样本包含的时间序列长度,为了捕捉用户行为的时序依赖关系,本文将时间步长T设置为5,表示每个输入样本包含连续5天的用户行为数据 |
| 特征类型 | 特征编号 | 特征 |
|---|---|---|
| Logon | 每个时间段内用户登录/登出的次数,全天内用户登录/登出的总次数,全天内用户登录/登出的最早/最晚时间,工作时间内用户登录/登出的最早/最晚时间,非工作时间内用户登录/登出的最早/最晚时间 | |
| device | 每个时间段内用户使用可移动设备连接/断开的次数,全天内用户使用可移动设备连接/断开的总次数,全天内用户使用可移动设备连接/断开的最早/最晚时间,工作时间内用户使用可移动设备连接/断开的最早/最晚时间,非工作时间内用户使用可移动设备连接/断开的最早/最晚时间 | |
| http | 每个时间段内用户访问可疑网站的次数,全天内用户访问可疑网站的总次数,全天内用户访问可疑网站的最早/最晚时间,工作时间内用户访问可疑网站的最早/最晚时间,非工作时间内用户访问可疑网站的最早/最晚时间,非工作时间内用户上传文件到可疑网站的次数 |
| 模型类别 | 主要参数 | 取值 |
|---|---|---|
| CNN | 学习率 | 0.001 |
| 卷积核个数 | 32 | |
| 卷积核大小 | 2、3、4 | |
| 池化核大小 | 2x2 | |
| 优化函数 | Adam | |
| 激活函数 | ReLU | |
| Dropout | 0.5 | |
| Dense 单元数 | 1 | |
| Dense 激活函数 | Sigmoid | |
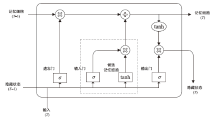
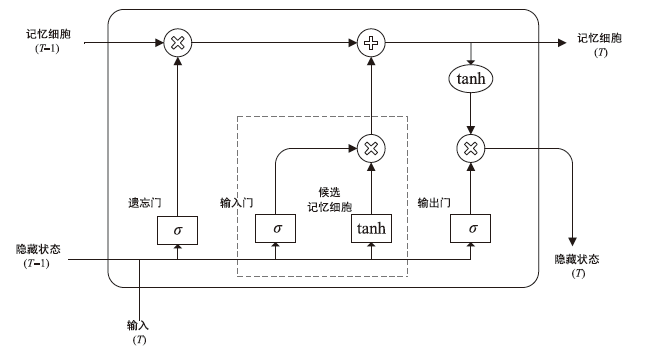
| LSTM | 学习率 | 0.001 |
| 隐藏层神经元数量 | 128 | |
| LSTM 隐藏层数量 | 1 | |
| 优化函数 | Adam | |
| Dropout | 0.5 | |
| Dense 单元数 | 1 | |
| Dense 激活函数 | Sigmoid | |
| CNN-LSTM | 学习率 | 0.001 |
| 卷积核个数 | 32 | |
| 卷积核大小 | 2、3、4 | |
| 池化核大小 | 2x2 | |
| 优化函数 | Adam | |
| Dropout | 0.5 | |
| Dense 单元数 | 1 | |
| Dense 激活函数 | Sigmoid |
| [1] | Gurucul. 2024 Insider Threat Report[EB/OL]. (2024-09-19)[2024-12-01]. https://gurucul.com/2024-insider-threat-report/. |
| [2] | YANG Guang, MA Jiangang, YU Aimin, et al. Survey of Insider Threat Detection[J]. Journal of Cyber Security, 2016, 1(3): 21-36. |
| [3] | DING Zixuan, CHEN Guo. Internal Network Security Threat Detection Method Based on XGBoost Algorithm[J]. Journal of Jilin University (Information Science Edition), 2024, 42(2): 366-371. |
| 丁梓轩, 陈国. 基于XGBoost算法的内部网络安全威胁检测方法[J]. 吉林大学学报(信息科学版), 2024, 42(2):366-371. | |
| [4] | LU Gaole, ZHANG Huixiang, LIU Tianluo, et al. Experimental Evaluation of Insider Threat Detection Methods Based on Temporal Representation[C]// IEEE. 2022 IEEE 10th International Conference on Information, Communication and Networks (ICICN). New York: IEEE, 2022: 682-688. |
| [5] | PADMAVATHI G, SHANMUGAPRIYA D, ASHA S. A Framework to Detect the Malicious Insider Threat in Cloud Environment Using Supervised Learning Methods[C]// IEEE. 2022 9th International Conference on Computing for Sustainable Global Development (INDIACom). New York: IEEE, 2022: 354-358. |
| [6] | HAIDAR D, GABER M M. Data Stream Clustering for Real-Time Anomaly Detection: An Application to Insider Threats[EB/OL]. (2018-11-28)[2024-12-01]. https://doi.org/10.1007/978-3-319-97864-2_6. |
| [7] | LE D C, ZINCIR-HEYWOOD N. Anomaly Detection for Insider Threats Using Unsupervised Ensembles[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1152-1164. |
| [8] | PREETAM P, PRATIK C, MAYANK S. Temporal Feature Aggregation with Attention for Insider Threat Detection from Activity Logs[EB/OL]. (2023-08-15)[2024-12-01]. https://www.sciencedirect.com/science/article/pii/S0957417423004268. |
| [9] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, et al. Internal Threat Detection Model Based on LSTM-Attention[J]. Netinfo Security, 2022, 22(2): 1-10. |
| 张光华, 闫风如, 张冬雯, 等. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2):1-10. | |
| [10] | BALARAM S, PRABHAT P, BASANTA J. User Behavior Analytics for Anomaly Detection Using LSTM Autoencoder-Insider Threat Detection[EB/OL]. (2020-07-03)[2024-12-01]. https://doi.org/10.1145/3406601.3406610. |
| [11] | SUN Degang, LIU Meichen, LI Meimei, et al. DeepMIT: A Novel Malicious Insider Threat Detection Framework Based on Recurrent Neural Network[C]// IEEE. 2021 IEEE 24th International Conference on Computer Supported Cooperative Work in Design (CSCWD). New York: IEEE, 2021: 335-341. |
| [12] | WANG Yifeng, GUO Yuanbo, LI Tao, et al. Research on Internal Threat Detection Method Under Small Sample Size[J]. Journal of Chinese Computer Systems, 2019, 40(11): 2330-2336. |
| 王一丰, 郭渊博, 李涛, 等. 一种小样本下的内部威胁检测方法研究[J]. 小型微型计算机系统, 2019, 40(11):2330-2336. | |
| [13] | GAYATHRI R G, SAJJANHAR A, YONG Xiang. Image-Based Feature Representation for Insider Threat Classification[EB/OL]. (2020-07-15)[2024-12-01]. https://www.mdpi.com/2076-3417/10/14/4945. |
| [14] | ANJU A, KRISHNAMURTHY M. M-EOS: Modified-Equilibrium Optimization-Based Stacked CNN for Insider Threat Detection[J]. Wireless Networks, 2024, 30: 2819-2838. |
| [15] | YUAN Fangfang, CAO Yanan, SHANG Yanmin, et al. Insider Threat Detection with Deep Neural Network[C]// Springer. Computational Science-ICCS 2018. Heidelberg: Springer, 2018: 43-54. |
| [16] | SINGH M, MEHTRE B M, SANGEETHA S. User Behavior Profiling Using Ensemble Approach for Insider Threat Detection[C]// IEEE. 2019 IEEE 5th International Conference on Identity, Security, and Behavior Analysis (ISBA). New York: IEEE, 2019: 1-8. |
| [17] | MORI H, KOBAYASHI H. Optimal Fuzzy Inference for Short-Term Load Forecasting[C]// IEEE. Proceedings of Power Industry Computer Applications Conference. New York: IEEE, 1995: 312-318. |
| [18] | LIU Yiqing, CHEN Xinfang. Research on Power Consumption Prediction Based on CNN+LSTM Hybrid Model[J]. Computer & Telecommunication, 2023(7): 65-69. |
| 刘义卿, 陈新房. 基于CNN+LSTM混合模型的电力消耗预测研究[J]. 电脑与电信, 2023(7):65-69. | |
| [19] | GLASSER J, LINDAUER B. Bridging the Gap: A Pragmatic Approach to Generating Insider Threat Data[C]// IEEE. 2013 IEEE Security and Privacy Workshops. New York: IEEE, 2013: 98-104. |
| [20] | PANTELIDIS E, BENDIAB G, SHIAELES S, et al. Insider Threat Detection Using Deep Autoencoder and Variational Autoencoder Neural Networks[C]// IEEE. 2021 IEEE International Conference on Cyber Security and Resilience (CSR). New York: IEEE, 2021: 129-134. |
| [21] | KAREV D, MCCUBBIN C, VAULIN R. Cyber Threat Hunting through the Use of an Isolation Forest[C]// ACM. CompSysTech’17: Proceedings of the 18th International Conference on Computer Systems and Technologies. New York: ACM, 2017: 163-170. |
| [22] | LE D C, ZINCIR-HEYWOOD N. Exploring Anomalous Behaviour Detection and Classification for Insider Threat Identification[EB/OL]. (2020-03-24)[2024-12-01]. https://doi.org/10.1002/nem.2109. |
| [1] | ZHANG Zhiqiang, BAO Yadong. Anomaly Traffic Detection Algorithm Integrating RF and CNN [J]. Netinfo Security, 2024, 24(11): 1655-1664. |
| [2] | LU Rui, LI Linying. A Named Entity Recognition Model for Legal Documents [J]. Netinfo Security, 2024, 24(11): 1783-1792. |
| [3] | LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure [J]. Netinfo Security, 2023, 23(6): 43-54. |
| [4] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [5] | ZHANG Yuchen, LI Lianghui, MA Chenyang, ZHOU Hongwei. A Log Anomaly Detection Method with Variables [J]. Netinfo Security, 2023, 23(10): 16-20. |
| [6] | YE Huanrong, LI Muyuan, JIANG Bo. Research on DGA Malicious Domain Name Detection Method Based on Transfer Learning and Threat Intelligence [J]. Netinfo Security, 2023, 23(10): 8-15. |
| [7] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [8] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [9] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention [J]. Netinfo Security, 2022, 22(2): 1-10. |
| [10] | YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model [J]. Netinfo Security, 2022, 22(12): 57-66. |
| [11] | YANG Ming, ZHANG Jian. Static Detection Model of Malware Based on Image Recognition [J]. Netinfo Security, 2021, 21(10): 25-32. |
| [12] | Yanchen QIAO, Qingshan JIANG, Liang GU, Xiaoming WU. Malware Classification Method Based on Word Vector of Assembly Instruction and CNN [J]. Netinfo Security, 2019, 19(4): 20-28. |
| [13] | Yong FANG, Guangxiatian ZHU, Luping LIU, Peng JIA. Research on Browser Fuzz Sample Generation Technology Based on Deep Learning [J]. Netinfo Security, 2019, 19(3): 26-33. |
| [14] | Xuruirui FENG, Jiayong LIU, Pengsen CHENG. Analyzing Malware Behavior and Capability Related Text Based on Feature Extraction [J]. Netinfo Security, 2019, 19(12): 72-78. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||