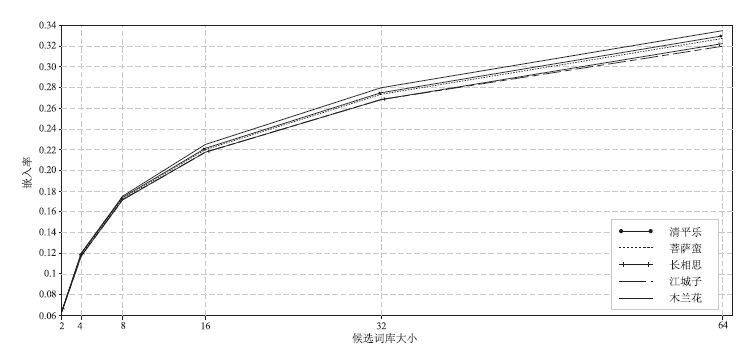
Netinfo Security ›› 2022, Vol. 22 ›› Issue (7): 46-54.doi: 10.3969/j.issn.1671-1122.2022.07.006
Previous Articles Next Articles
Information Steganography Algorithm for Automatic Generation of Song Ci
YANG Wanxia1,2( ), CHEN Shuai3, GUAN Lei4,5, YANG Zhongliang2,4
), CHEN Shuai3, GUAN Lei4,5, YANG Zhongliang2,4
- 1. College of Mechanical and Electrical Engineering, Gansu Agricultural University, Lanzhou 730070, China
2. Institute for Electronics and Information Technology in Tianjin, Tsinghua University, Tianjin 300467, China
3. Network Security Bureau of the Ministry of Public Security, Beijing 100006, China
4. Department of Electronic Engineering, Tsinghua University, Beijing 100084, China
5. The First Research Institute of the Ministry of Public Security, Beijing 100044, China
-
Received:2022-02-26Online:2022-07-10Published:2022-08-17 -
Contact:YANG Wanxia E-mail:yangwanxia@163.com
CLC Number:
Cite this article
YANG Wanxia, CHEN Shuai, GUAN Lei, YANG Zhongliang. Information Steganography Algorithm for Automatic Generation of Song Ci[J]. Netinfo Security, 2022, 22(7): 46-54.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.07.006
| [1] | ZHANG Zhenyu, LI Qianmu, QI Yong. Text Watermarking Design Based on Invisible Characters[J]. Journal of Nanjing University of Science and Technology, 2017, 41(4): 405-411. |
| 张震宇, 李千目, 戚湧. 基于不可见字符的文本水印设计[J]. 南京理工大学学报(自然科学版), 2017, 41(4): 405-411. | |
| [2] | WU Guohua, GONG Lichun, YUAN Lifeng, et al. Review of Information Hiding on Chinese Text[J]. Journal on Communications, 2019, 40(9): 145-156. |
| 吴国华, 龚礼春, 袁理锋, 等. 中文文本信息隐藏研究进展[J]. 通信学报, 2019, 40(9): 145-156. | |
| [3] | BEHROOZ K, BEHNAM K, BAHMAN K, et al. A New Method for pdf Steganography in Justified Texts[J]. Journal of Information Security and Applications, 2019(45): 61-70. |
| [4] | YU Zhenshan, HUANG Liusheng, CHEN Zhili, et al. High Embedding Ratio Text Steganography by Ci-Poetry of the Song Dynasty[J]. Journal of Chinese Information Processing, 2009, 23(4): 55-63. |
| 余振山, 黄刘生, 陈志立, 等. 用宋词实现高嵌入率文本信息隐藏[J]. 中文信息学报, 2009, 23(4): 55-63. | |
| [5] |
ALOTAIBI R A, ELREFAEI L A. Improved Capacity Arabic Text Watermarking Methods Based on Open Word Space[J]. Journal of King Saud University-Computer and Information Sciences, 2018, 30(2): 236-248.
doi: 10.1016/j.jksuci.2016.12.007 URL |
| [6] | ZHANG Wei, WANG Xiaomei, ZHANG Chenxu. Coverless Text Steganography Method Based on Tone Feature Mapping[J]. Journal of Information Engineering University, 2021, 22(1): 38-43. |
| 张维, 王晓梅, 张晨旭. 一种基于声调特征映射的无载体信息隐藏方法[J]. 信息工程大学学报, 2021, 22(1): 38-43. | |
| [7] | CHEN Xianyi, CHEN Sheng, WU Yulei. Coverless Information Hiding Method Based on the Chinese Character Encoding[J]. Journal of Internet Technology, 2017, 18(2): 313-320. |
| [8] | ZHANG Jianjun, WANG Lucai, LIN Haijun. Coverless Text Information Hiding Method Based on the Word Rank Map[J]. Journal of Internet Technology, 2017, 18(2): 427-434. |
| [9] |
YANG Zhongliang, GUO Xiaoqing, CHEN Ziming, et al. RNN-Stega: Linguistic Steganography Based on Recurrent Neural Networks[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(5): 1280-1295.
doi: 10.1109/TIFS.2018.2871746 URL |
| [10] | KANG Huixian, WU Hanzhou, ZHANG Xinpeng. Generative Text Steganography Based on LSTM Network and Attention Mechanism with Keywords[J]. Electronic Imaging, 2020(4): 291-298. |
| [11] | LIU Yanchen, WANG Jian, WANG Zhibin, et al. A Technique of High Embedding Rate Text Steganography Based on Whole Poetry of Song Dynasty[C]// Springer. Proceedings of the Second International Conference on Cloud Computing and Security. Berlin: Springer, 2016: 178-189. |
| [12] | LUO Yubo, HUANG Yongfeng, LI Fufang, et al. Text Steganography Based on Ci-Poetry Generation Using Markov Chain Model[J]. KSII Transactions on Internet and Information Systems, 2016, 10(9): 4568-4584. |
| [13] | YI Xiaoyuan, LI Ruoyu, SUN Maosong. Generating Chinese Classical Poems with RNN Encode-Decoder[C]// IEEE. Proceedings of the 16th Chinese Computational Linguistics. New York: IEEE, 2017: 211-223. |
| [14] | YI Xiaoyuan, SUN Maosong, LI Ruoyu, et al. Chinese Poetry Generation with a Working Memory Mode[C]// ACM. Proceding of the 27th International Joint Conference on Artificial Intelligence. New York: ACM, 2018: 4553-4559. |
| [15] | LUO Yubo, HUANG Yongfeng. Text Steganography with High Embedding Rate: Using Recurrent Neural Networks to Generate Chinese Classic Poetry[C]// ACM. Proceedings of the Seventh ACM Workshop on Information Hiding & Multimedia Security. New York: ACM, 2017: 99-104. |
| [16] | QIN Chuan, WANG Meng, SI Guangwen, et al. Constructive Information Hiding with Chinese Quatrain Generation[J]. Chinese Journal of Computers, 2021, 44(4): 773-785. |
| 秦川, 王萌, 司广文, 等. 基于绝句生成的构造式信息隐藏算法[J]. 计算机学报, 2021, 44(4): 773-785. | |
| [17] |
ZHENG Haitao, WANG Wei, CHEN Wang, et al. Automatic Generation of News Comments Based on Gated Attention Neural Networks[J]. IEEE Access, 2018, 6: 702-710.
doi: 10.1109/ACCESS.2017.2774839 URL |
| [18] | MA Liang, WANG Zili, YANG Fan, et al. Robust State of Charge Estimation Based on a Sequence-to-Sequence Mapping Model with Process Information[J]. Journal of Power Sources, 2020(474): 30-35. |
| [19] | LI Xuehong, GUO Hui, ANG Chaoqun. Text Digital Watermarking Algorithm Based on Improve Line Shift Coding[J]. Computer & Digital Engineering, 2014, 42(9): 1687-1690, 1712. |
| 李雪红, 郭晖, 昂朝群. 改进行移编码的文本数字水印算法研究[J]. 计算机与数字工程, 2014, 42(9): 1687-1690,1712. | |
| [20] | KIM M Y, ZAIANE O R. Natural Lanuage Watermarking Based on Syntactic Displacement and Morphological Divsion[C]// IEEE. Computer Software and Applications Conference Workshops (COMPSACW). New York:IEEE, 2010: 164-169. |
| [21] | CHAPMAN M, DAVIDA G. Hiding the Hidden: A Software System for Concealing Ciphertext in Innocuous Text[C]// Springer. Proceedings of the International Conference on Information and Communications Security. Berlin: Springer, 1997: 335-345. |
| [1] | FAN Mingyu, LI Ke. A Method to Distinguish DDoS Attack Types Based on RNN [J]. Netinfo Security, 2022, 22(7): 1-8. |
| [2] | LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion [J]. Netinfo Security, 2022, 22(7): 18-26. |
| [3] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [4] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| [5] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment [J]. Netinfo Security, 2022, 22(7): 55-63. |
| [6] | ZHANG Mengjie, WANG Jian, HUANG Kaijie, YANG Gang. A Static Detection Method of ROP Traffic Based on Bytes Fluctuation Characteristics [J]. Netinfo Security, 2022, 22(7): 64-72. |
| [7] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [8] | FU Zhibin, QI Shuren, ZHANG Yushu, XUE Mingfu. Localization Network of Deep Inpainting Based on Dense Connectivity [J]. Netinfo Security, 2022, 22(7): 84-93. |
| [9] | QIN Baodong, YU Peihang, ZHENG Dong. Decision Tree Classification Model Based on Double Trapdoor Homomorphic Encryption [J]. Netinfo Security, 2022, 22(7): 9-17. |
| [10] | WANG Juan, WANG Yunru, WENG Bin, GONG Jiaxin. Survey on Application of Machine Learning in Disassembly on x86 Binaries [J]. Netinfo Security, 2022, 22(6): 9-25. |
| [11] | GUO Baoxia, WANG Jiahui, MA Limin, ZHANG Wei. Research on Dynamic Access Control Model of Sensitive Data Based on Zero Trust [J]. Netinfo Security, 2022, 22(6): 86-93. |
| [12] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [13] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain [J]. Netinfo Security, 2022, 22(6): 61-72. |
| [14] | WANG Shengwen, HU Aiqun. Design of E-mail Encryption System Based on SM9 Algorithm [J]. Netinfo Security, 2022, 22(6): 53-60. |
| [15] | ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning [J]. Netinfo Security, 2022, 22(6): 44-52. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||