Netinfo Security ›› 2020, Vol. 20 ›› Issue (11): 15-21.doi: 10.3969/j.issn.1671-1122.2020.11.003
Previous Articles Next Articles
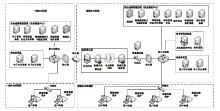
Design and Practice of Simulation Environment for Cyber Security Classified Protection Evaluation
ZHENG Guogang( ), YIN Xiangpei, WANG Kui, HE Kunpeng
), YIN Xiangpei, WANG Kui, HE Kunpeng
- MPS Information Security Classified Protection Evaluation Center, Beijing 100142, China
-
Received:2020-08-15Online:2020-11-10Published:2020-12-31 -
Contact:ZHENG Guogang E-mail:guogangzheng@qq.com
CLC Number:
Cite this article
ZHENG Guogang, YIN Xiangpei, WANG Kui, HE Kunpeng. Design and Practice of Simulation Environment for Cyber Security Classified Protection Evaluation[J]. Netinfo Security, 2020, 20(11): 15-21.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.11.003
| [1] | GB/T 25070-2019. Information Security Technology—Technical Requirements of Security Design for Classified Protection of Cybersecurity[S]. Beijing: Standards Press of China, 2019. |
| GB/T 25070-2019.信息安全技术网络安全等级保护安全设计技术要求[S]. 北京: 中国标准出版社, 2019. | |
| [2] | QU Jie, FAN Chunling, CHEN Guangyong, et al. Research on Establishment of Network Security Service Ability System for A New Era[J]. Netinfo Security, 2019,19(1):83-87. |
| [3] | NPC. Cybersecurity Law of the People’s Republic of China[EB/OL]. http://www.npc.gov.cn/npc/, 2016-11-7. |
| 全国人大. 中华人民共和国网络安全法[EB/OL]. http://www.npc.gov.cn/npc/, 2016-11-7. | |
| [4] | JI Hui. Controlling Information System Risk by Information Security Service[J]. Netinfo Security, 2010,10(5):17-18. |
| [5] | GUO Qiquan. Training Course on Cybersecurity Law and Classified Protection of Cybersecurity[M]. Beijing: Publishing House of Electronics Industry, 2018. |
| 郭启全. 网络安全法与网络安全等级保护制度培训教程[M]. 北京: 电子工业出版社, 2018. | |
| [6] | GB/T 22239-2008. Information Security Technology-Baseline for Classified Protection of Information System Security[S]. Beijing: Standards Press of China, 2008. |
| GB/T 22239-2008.信息安全技术信息系统安全等级保护基本要求[S]. 北京: 中国标准出版社, 2008. | |
| [7] | National Information Security Standardization Technical Committee. Information Security Technology—Baseline for Classified Protection of Cybersecurity(Draft)[EB/OL]. https://www.tc260.org.cn/, 2018-10-31. |
| 全国信息安全标准化技术委员会. 信息安全技术网络安全等级保护基本要求(征求意见稿)[EB/OL]. https://www.tc260.org.cn/, 2018-10-31. | |
| [8] | National Information Security Standardization Technical Committee. Information Security Technology—Evaluation Requirement for Classified Protection of Cybersecurity(Draft)[EB/OL]. https://www.tc260.org.cn/, 2018-10-31. |
| 全国信息安全标准化技术委员会. 信息安全技术网络安全等级保护测评要求(征求意见稿)[EB/OL]. https://www.tc260.org.cn/, 2018-10-31. |
| [1] | DUAN Xiaowei, HAN Yiliang, WANG Chao, LI Zhe. Analysis and Improvement of Public Key Reuse for A RLWE Key Exchange Protocol [J]. Netinfo Security, 2020, 20(11): 87-94. |
| [2] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract [J]. Netinfo Security, 2020, 20(11): 22-31. |
| [3] | WEN Weiping, CHEN Xiarun, YANG Fachang. Malicious Code Forensics Method Based on Hidden Behavior Characteristics of Rootkit on Linux [J]. Netinfo Security, 2020, 20(11): 32-42. |
| [4] | LANG Weimin, WANG Xueli, ZHANG Han, PEI Yunxiang. A Secure Data Deduplication Scheme Based on Secret Sharing Algorithm [J]. Netinfo Security, 2020, 20(11): 43-50. |
| [5] | LI Hongjiao, CHEN Hongyan. Research on Mobile Malicious Adversarial Sample Generation Based on WGAN [J]. Netinfo Security, 2020, 20(11): 51-58. |
| [6] | LIU Lijuan, LI Zhihui, ZHI Danli. A Multi-party Quantum Key Distribution Protocol with Quantum Identity Authentication [J]. Netinfo Security, 2020, 20(11): 59-66. |
| [7] | CHENG Yang, LEI Min, LUO Qun. Access Authentication Method for IoT Terminal Devices Based on Deep Learning [J]. Netinfo Security, 2020, 20(11): 67-74. |
| [8] | XIAO Biao, YAN Hongqiang, LUO Haining, LI Jucheng. Research on Improvement of Bayesian Network Privacy Protection Algorithm Based on Differential Privacy [J]. Netinfo Security, 2020, 20(11): 75-86. |
| [9] | GUO Qiquan, ZHANG Haixia. Technology System for Security Protection of Critical Information Infrastructures [J]. Netinfo Security, 2020, 20(11): 1-9. |
| [10] | FAN Bo, GONG Gangjun, SUN Shuxian. Research on Dynamic Security System of Distribution IoT Based on Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2020, 20(11): 10-14. |
| [11] | HUO Wei. Research and Thinking on Promoting the Application of Cryptography Fusion [J]. Netinfo Security, 2020, 20(10): 1-5. |
| [12] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [13] | LIU Yi, LI Jianhua, CHEN Yu, QI Zisen. A Shared Protection Algorithm for Data Center Network Nodes [J]. Netinfo Security, 2020, 20(10): 27-33. |
| [14] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| [15] | LIU Kaifang, FU Shaojing, SU Jinshu, ZHANG Fucheng. An Optimizing Scheme on Multi-domain Collaborative IOTA Blockchain Technology for the Internet of Things [J]. Netinfo Security, 2020, 20(10): 41-48. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||