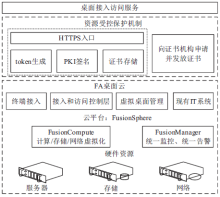
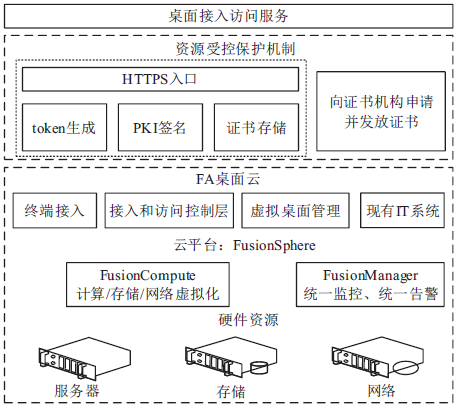
| [1] |
唐兴助,解月江,马颖劲. 基于OpenStack的桌面云的应用与挑战[J]. 计算机技术与发展,2017,27(2):147-150.
|
| [2] |
MELL P, GRANCE T.The NIST Definition of Cloud Computing[J]. Communications of the ACM, 2009, 53(6): 50.
|
| [3] |
王峰,江峰,李朝阳. 虚拟桌面及关键技术分析云计算时代的数据库研究[J].电信技术,2011(1):24-26.
|
| [4] |
曾睿,宁春玲. 基于云桌面虚拟的办公多元化网络虚拟技术[J].中国新通信,2014(4):104-104.
|
| [5] |
SREENIVAS V, ARUNAKUMARI B, VENKATARAO J. Enhancing the Security for Information with Virtual Data Centers in Cloud[EB/OL]. , 2017-6-11.
|
| [6] |
CHEN Deyan, ZHAO Hong.Data Security and Privacy Protection Issues in Cloud Computing[C]// IEEE. 2012 International Conference on Computer Science and Electronics Engineering, March 23-25, 2012, Hangzhou, China. New Jersey: IEEE, 2012: 647-651.
|
| [7] |
LIU Zhigui, YANG Lichun, PU Jie, et al.The System of Digital Signature Authentication Based on PKI[J]. Application Research of Computers, 2004, 21(9): 158-160.
|
| [8] |
莫止卿. 桌面虚拟化的安全分析与设计[J].信息安全与通信保密,2014(9):154-155.
|
| [9] |
国杰彬,李运发,张大军. 云计算中面向数据安全的身份认证策略研究[J].信息网络安全,2017(3):72-77.
|
| [10] |
龚强. 云计算关键技术之云安全问题认知研究[J].信息技术,2014(4):1-3.
|
| [11] |
林伟伟,齐德昱. 云计算资源调度研究综述[J]. 计算机科学,2012,39(10):1-6.
|
| [12] |
冯朝胜,秦志光,袁丁,等. 云计算环境下访问控制关键技术[J]. 电子学报,2015,43(2):312-319.
|
| [13] |
PALADI N, GEHRMANN C, MICHALAS A.Providing User Security Guarantees in Public Infrastructure Clouds[J]. IEEE Transactions on Cloud Computing, 2016, 5(3): 405-419.
|
| [14] |
MARTINELLI S, NASH H, TOPOL B. Identity, Authentication,Access Management in OpenStack: Implementing and Deploying Keystone[M]. Sebastopol: O'Reilly Media, Inc., 2015.
|
| [15] |
孙勇. NET下使用虚拟Token的安全认证方案[J]. 计算机工程与科学,2008,30(4):15-16.
|
| [16] |
KHALID U, GHAFOOR A, IRUM M, et al. Cloud Based Secure and Privacy Enhanced Authentication & Authorization Protocol[EB/OL]. , 2017-6-12.
|
| [17] |
张永强,卢伟龙,唐春明,等. 一种高效实用的基于云服务的数字签名方案研究[J].信息网络安全,2016(7):1-6.
|
| [18] |
WEI Lifei, ZHU Haojin, CAO Zhenfu, et al.Security and Privacy for Storage and Computation in Cloud Computing[J]. Information Sciences, 2014, 258(3): 371-386.
|
| [19] |
WANG Huaqun, WU Qianhong, QIN Bo, et al.Identity-based Remote Data Possession Checking in Public Clouds[J]. IET Information Security, 2014, 8(2): 114-121.
|
| [20] |
吕从东,韩臻,马威. 云存储服务端数据存储加密机制的设计和实现[J].信息网络安全,2014(6):1-5.
|
 ), Lei HAN2, Zhen HAN1
), Lei HAN2, Zhen HAN1