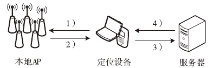
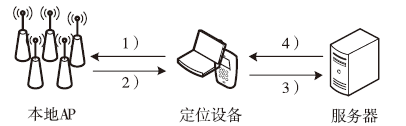
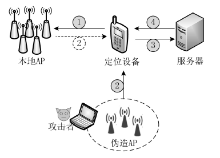
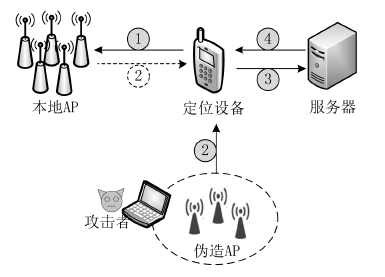
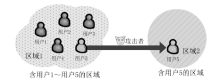
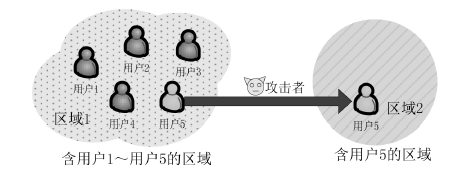
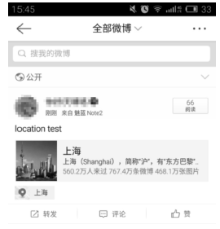
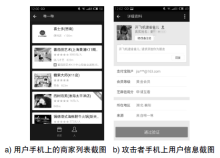
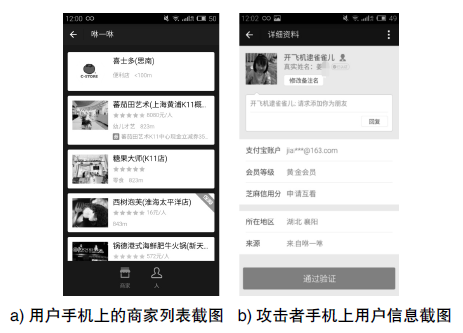
Netinfo Security ›› 2017, Vol. 17 ›› Issue (5): 51-56.doi: 10.3969/j.issn.1671-1122.2017.05.008
• Orginal Article • Previous Articles Next Articles
Research on Privacy Attack Based on Location Cheating in Social Network
- College of Mathematics and Computer Science, Fujian Normal University, Fuzhou Fujian 350007, China
-
Received:2016-03-31Online:2017-05-20Published:2020-05-12
CLC Number:
Cite this article
Qing LI, A-yong YE, Li XU. Research on Privacy Attack Based on Location Cheating in Social Network[J]. Netinfo Security, 2017, 17(5): 51-56.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2017.05.008
| [1] | 刘树栋,孟祥武.基于位置的社会化网络推荐系统[J].计算机学报,2015,38(2):322-336. |
| [2] | FERRARO R, AKTIHANOGLU M.Location-Aware Applications[J]. Manning, 2011(4849):377-383. |
| [3] | 王乐,王勇,王东安,等.社交网络中信息传播预测的研究综述[J]. 信息网络安全,2015(5):47-55. |
| [4] | WANG Xiangyu, ZHAO Yiliang L, Nie Liqiang, et al.Semantic-Based Location Recommendation With Multimodal Venue Semantics[J]. IEEE Transactions on Multimedia, 2015, 17(3):409-419. |
| [5] | QIAO Xiuquan, SU Jianchong, ZHANG Jinsong, et al.Recommending Friends Instantly in Location-based Mobile Social Networks[J]. China Communications, 2014, 11(2):109-127. |
| [6] | BROOKER D, CAREY T, WARREN I.Middleware for Social Networking on Mobile Devices[C]// IEEE.ASWEC ‘10 Proceedings of the 2010 21st Australian Software Engineering Conference, April 6 - 9, 2010 .Washington, DC, USA .NJ: IEEE, 2010:202-211. |
| [7] | TIPPENHAUER N O, RASMUSSEN K B, PÖPPER C,et al. Attacks on Public WLAN-based Positioning Systems[C]//ACM. Proceedings of the 7th International Conference on Mobile Systems, Applications, and Services, June 22 - 25, 2009. Kraków, Poland .New York:ACM, 2009:29-40. |
| [8] | 周傲英,杨彬,金澈清,等.基于位置的服务:架构与进展[J].计算机学报,2011,34(7): 1155-1171. |
| [9] | 梁颖升,王琼霄,马存庆,等. 一种基于移动终端的可信消息传输方案设计[J]. 信息网络安全,2015(9):158-162. |
| [10] | 车延辙. 基于位置服务中用户位置隐私保护关键技术研究[D].杭州:浙江大学,2013. |
| [11] | BETTINI C, WANG X S, JAJODIA S.Protecting Privacy against Location- based Personal Identification[A]// Secure Data Management[M]. Heidelberg: Springer, Berlin, Heidelberg, 2005:185-199. |
| [12] | SAPUTRO W U. Analisis Performance Jaringan Nirkabel Menggunakan Aircrack-Ng Dan Wireshark[EB/OL]. . |
| [13] | ASPj of k2wrlz.mdk3 Package Description[EB/OL]. . |
| [14] | BAHL P, PADMANABHAN V N.RADAR: An In-building RF-based User Location and Tracking System[J]. Proceedings - IEEE INFOCOM, 2000(2):775-784. |
| [15] | LI Binghao, SALTER J, DEMPSTER A G, et al. Indoor Positioning Techniques Based on Wireless LAN[EB/OL]. https://www.researchgate.net/publication/228998356_Indoor_positioning_techniques_based_on_wireless_LAN, 2017-3-10. |
| [16] | WiGLE.WiGLE: Wireless Network Mapping[EB/OL]. /,2017-2-12. |
| [17] | MATTE C, ACHARA J P, CUNCHE M.Short: Device-to-Identity Linking Attack Using Targeted Wi-Fi Geolocation Spoofing[C]// ACM.Proceedings of the 8th ACM Conference on Security & Privacy in Wireless and Mobile Networks, June 22 - 26, 2015 . New York . New York :ACM,2015:1-6. |
| [18] | CUNCHE M.I Know Your MAC Address: Targeted Tracking of Individual Using WiFi[J]. Journal of Computer Virology and Hacking Techniques, 2014,10(4):219-227. |
| [19] | 李凌云,敖吉,乔治,等. 基于微博的安全事件实时监测框架研究 [J].信息网络安全,2015(1):16-23. |
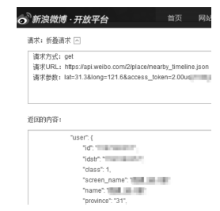
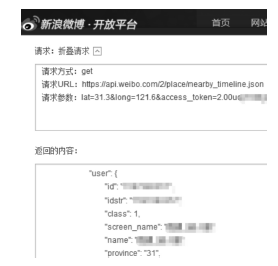
| [20] | 新浪公司.位置服务-微博API [EB/OL]. . |
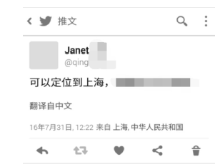
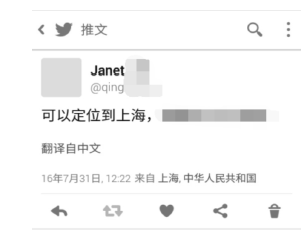
| [21] | Twitter. Streaming API Request Parameters-Twitter Developers [EB/OL]., 2010-6-22. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||