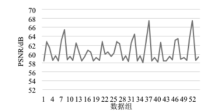
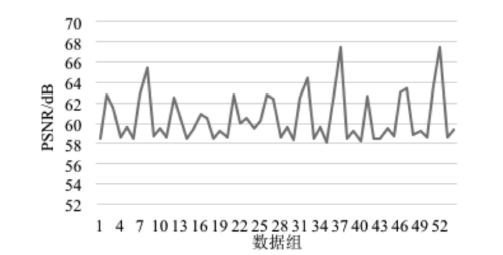
| [1] |
叶伟伟,欧庆于,柏小武. 基于服务架构的密码服务系统认证方案研究[J]. 信息网络安全,2016(5):37-43.
|
| [2] |
DAWSON E, GAURAVARAM P,MCCULLAGH A. Collision Attacks on MD5 and SHA-1: Is this the “Sword of Damocles” for Electronic Commerce?[EB/OL]. , 2017-1-22.
|
| [3] |
AL FARDAN N J, PATERSON K G. Lucky Thirteen: Breaking the TLS and DTLS Record Protocols[C]//IEEE. 2013 IEEE Symposium on Security and Privacy, May 19-22, 2013, Berkeley, CA, USA. Washington: IEEE, 2013: 526-540.
|
| [4] |
肖迪,马青青,王兰,等. 基于稀疏表示的云协助安全数字水印技术[J]. 信息网络安全,2017(1):1-7.
|
| [5] |
CHEN B, WORNELL G W.Quantization Index Modulation: A Class of Provably Good Methods for Digital Watermarking and Information Embedding[J]. Information Theory IEEE Transactions on, 2001, 47(4): 1423-1443.
|
| [6] |
马志伟,满春涛,李巍. 基于STDM与粒子群优化的音频水印算法[J]. 哈尔滨理工大学学报,2016(5):73-78.
|
| [7] |
BITAR A W, DARAZI R, COUCHOT J F,et, al. Blind Digital Watermarking in PDF Documents Using Spread Transform Dither Modulation[J]. Multimedia Tools and Applications, 2017, 76(1): 143-161.
|
| [8] |
毕洪波. 鲁棒性数字图像与视频水印算法研究[D]. 北京:北京邮电大学,2013.
|
| [9] |
张咏. 随机数发生器和随机数性能检验方法研究[D]. 四川:电子科技大学,2006.
|
| [10] |
吴永强. 国密SSL安全通信协议的研究与实现[M]. 西安:西安电子科技大学,2014.
|
| [11] |
KIM W G, LEE H K. Spatial Domain Adaptive QIM Watermarking Against Valumetric Scaling Attack[EB/OL]. .
|
| [12] |
肖迪,王莹,常燕廷,等. 基于加法同态与多层差值直方图平移的密文图像可逆信息隐藏算法[J]. 信息网络安全,2016(4):9-16.
|
| [13] |
吴明航. DES和RSA混合加密算法的研究[D]. 哈尔滨:哈尔滨工业大学,2013.
|
| [14] |
ZHENG Xiaoling, JIN Jidong.Research for the Application and Safety of MD5 Algorithm in Password Authentication[C]//IEEE. 9th International Conference on Fuzzy Systems and Knowledge Discovery, May 29-31, 2012, Chongqing, China. New Jersey: IEEE, 2012: 2216-2219.
|
| [15] |
毛明,陈少晖,袁征,等. 关于Hash函数MD5的解析[J]. 计算机科学,2009,36(11):106-108.
|
| [16] |
赵俭,张畅,汶向东. 主机资源远程控制系统研究与设计[J]. 信息网络安全,2016(7):29-34.
|
| [17] |
VARSHNEY V, GUPTA R, SINGH P.Hybrid DWT-DCT Based Method for Palm-print Recognition[C]//IEEE. 2014 IEEE International Symposium on Signal Processing and Information Technology, December 15-17, 2014, Noida, India. New Jersey: IEEE, 2014: 7-12.
|
 ), Ding CHENG3, Pengyu QIN1,2, Cheng CHENG4
), Ding CHENG3, Pengyu QIN1,2, Cheng CHENG4