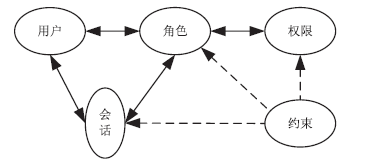
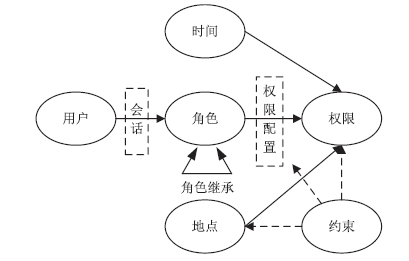
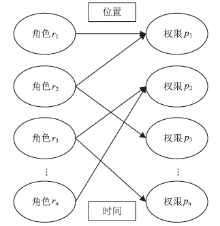
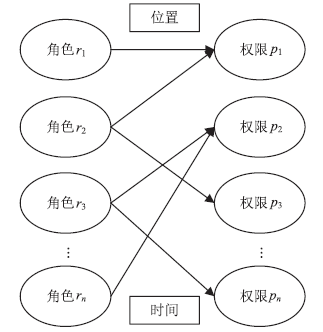
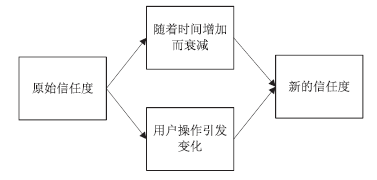
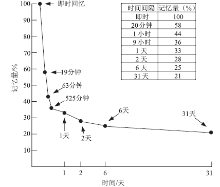
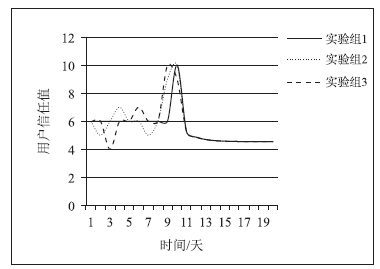
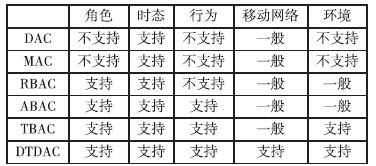
| [1] |
DOWNS D D, RUB J R, KUNG K C, et al.Issues in Discretionary Access Control[C]//IEEE. 1985 IEEE Symposium on Security and Privacy, April 22-24, 1985, Oakland, CA, USA. New Jersey: IEEE, 1985: 208.
|
| [2] |
郑周,张大军,李运发. 云计算中面向数据存储的安全访问控制机制[J]. 信息网络安全,2015(9):221-226.
|
| [3] |
SANDHU R S, SAMARATI P.Access Control: Principle and Practice[J]. IEEE Communications Magazine, 1994, 32(9): 40-48.
|
| [4] |
SANDHU R.Rationale for the RBAC96 Family of Access Control Models[C]//ACM. The First ACM Workshop on Role-based Access Control, November 30-December 1, 1995, Gaithersburg, MD, USA. New York: ACM, 1996: 9.
|
| [5] |
SANDHU R S, COYNE E J, FEINSTEIN H L, et al.Role-based Access Control Models[J]. Computer, 1996, 29(2): 38-47.
|
| [6] |
SANDHU R, BHAMIDIPATI V, MUNAWER Q.The ARBAC97 Model for Role-based Administration of Roles[J]. ACM Transactions on Information and System Security (TISSEC), 1999, 2(1): 105-135.
|
| [7] |
陈晓,赵晶玲. 大数据处理中混合型聚类算法的研究与实现[J]. 信息网络安全,2015(4):45-49.
|
| [8] |
徐仰彬. 基于SOM的文本聚类及其在搜索结果中的应用[D]. 西安:西安电子科技大学,2007.
|
| [9] |
皮佳明. 基于用户兴趣变化的协同过滤推荐算法研究[D]. 昆明:云南财经大学,2014.
|
| [10] |
李凤华,王巍,马建峰,等. 基于行为的访问控制模型及其行为管理[J].电子学报,2008,36(10):1881-1890.
|
| [11] |
邓集波,洪帆. 基于任务的访问控制波形[J]. 软件学报,2003,14(1):76-82.
|
| [12] |
张涛,张勇,宁戈,等. 基于SELinux强制访问控制的进程权限控制技术研究与实现[J]. 信息网络安全,2015(12):34-41.
|
| [13] |
LINDQVIST H.Mandatory Access Control[J]. Medical Teacher, 2010, 32(7) : 972.
|
| [14] |
WAGSTAFF K, CARDIE C, ROGERS S, et al.Constrained k-means Clustering with Background Knowledge[C]//Williams College. 18th International Conference on Machine Learning, June 28, 2001, Williamstown, MA, USA. New York: ACM, 2001: 577-584.
|
| [15] |
唐春明,郑晓龙. 云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全,2015(2):19-25.
|
 ), Fuzhen CHEN1,2, Pengyu QIN1,2, Jiujun CHENG1,2
), Fuzhen CHEN1,2, Pengyu QIN1,2, Jiujun CHENG1,2