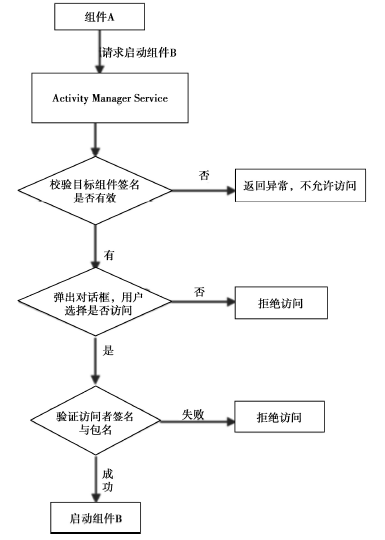
| [1] |
环球网. 2015年Android恶意软件样本数量超230万[EB/OL]. , 2016-06-16.
|
| [2] |
卿斯汉. Android安全研究进展[J]. 软件学报,2016(1):45-71.
|
| [3] |
Android Developers. Android Permissions[EB/OL].,2016-06-15.
|
| [4] |
FANG Z, HAN W, LI Y.Permission Based Android Security: Issues and Countermeasures[J]. Computers & Security, 2014, 43(6):205-218.
|
| [5] |
BARRERA D, KAYACIK, SOMAYAJI A, et al. A Methodology for Empirical Analysis of Permission-based Security Models and its Application to Android[EB/OL]., 2016-06-16.
|
| [6] |
JEON J, MICINSKI K K, VAUGHAN J A, et al. Dr. Android and Mr. Hide: Fine-grained Permissions in Android Applications[EB/OL]., 2016-06-16.
|
| [7] |
XU R, SAIDI H, ANDERSON R. Aurasium: Practical Policy Enforcement for Android Applications[EB/OL].,2016-06-16.
|
| [8] |
CUI X, YU D, CHAN P, et al. CoChecker: Detecting Capability and Sensitive Data Leaks from Component Chains in Android[EB/OL]..
|
| [9] |
ROHRER F, ZHANG Y, LOU C, et al. DR BACA: Dynamic Role Based Access Control for Android[EB/OL]., 2016-06-16.
|
| [10] |
NAUMAN M, KHAN S, OTHMAN A T, et al.Realization of a User-centric, Privacy Preserving Permission Framework for Android[J]. Security & Communication Networks, 2014, 8(3):368-382.
|
| [11] |
孟康,周小兵,韩强. 基于Android签名及敏感权限分组的安全检测系统[J]. 云南民族大学学报:自然科学版,2015,24(5):418-421.
|
| [12] |
吴文焕. Android应用程序数字签名机制研究[J]. 软件, 2014(2):109-110.
|
| [13] |
王少辉,王超,孙国梓. DroidDefence:细粒度的Android应用权限管理系统[J]. 四川大学学报:工程科学版,2014,46(6):14-18.
|
| [14] |
闫梅,彭新光. 基于Android安全机制的权限检测系统[J]. 计算机工程与设计,2013,34(3):854-858.
|
| [15] |
朱佳伟,喻梁文,关志,等. Android权限机制安全研究综述[J]. 计算机应用研究,2015,32(10):2881-2885.
|
| [16] |
张金鑫,杨晓辉. 基于权限分析的 Android 应用程序检测系统[J]. 信息网络安全,2014(7):30-34.
|
| [17] |
Android Community. Downloading and Building[EB/OL], .
|
 ), Shaozhang NIU
), Shaozhang NIU