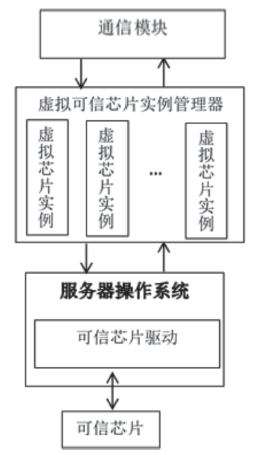
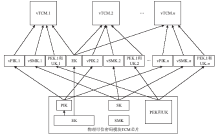
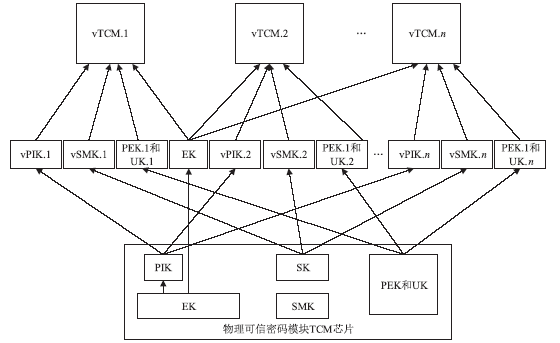
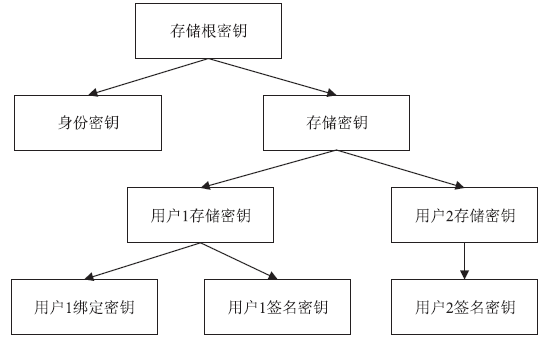
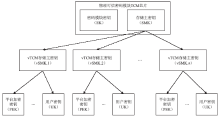
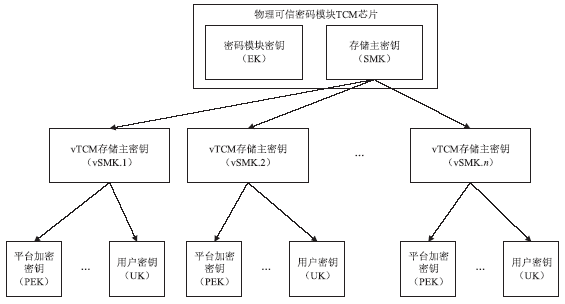
Netinfo Security ›› 2016, Vol. 16 ›› Issue (4): 17-22.doi: 10.3969/j.issn.1671-1122.2016.04.003
• Orginal Article • Previous Articles Next Articles
Research of Virtual Trusted Cryptography Module’s Secret Key Management Based on the Trusted Root Server
Guan WANG1,2, Huahao YUAN1,2( )
)
- 1. College of Computer, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
-
Received:2016-02-10Online:2016-04-20Published:2020-05-13
CLC Number:
Cite this article
Guan WANG, Huahao YUAN. Research of Virtual Trusted Cryptography Module’s Secret Key Management Based on the Trusted Root Server[J]. Netinfo Security, 2016, 16(4): 17-22.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.04.003
| [1] | 文莎. 虚拟化技术及其安全问题[J]. 网络安全技术与应用, 2014 (7):165-165. |
| [2] | 王因传,杨林,孙伟峰. IBM vTPM的Xen实现研究[J].军事通信技术,2010(3):67-71. |
| [3] | 张少华. 基于云平台可信根关键技术的研究[D].北京:北京工业大学, 2015. |
| [4] | SADEGHI A R, STUBLE C, WINANDY M.Property-Based TPM Virtualization[M]. Berlin Heidelberg: Springer, 2008 : 1-16. |
| [5] | ENGLAND P, LOESER J.Para-Virtualized TPM Sharing[M].Trusted Computing-Challenges and Applications. Springer Berlin Heidelberg,2008:119-132. |
| [6] | BERGER S, CACERES R, GOLDMAN K A, et al.vTPM: Virtualizing the Trusted Platform Module.[J]. Usenix Security, 2006(15) :305-320. |
| [7] | 李健航,张枚,刘锋,等. 可信密码模块(TCM)芯片的虚拟化设计[J]. 信息网络安全,2010,(1):60~65. |
| [8] | 何慧,江水,李立号,等. 基于TCM的国产化虚拟可信计算平台研究[J]. 计算机工程,2011(S1):63~66, 79. |
| [9] | GB/T 29829-2013.信息安全技术可信计算密码支撑平台功能与接口规范B/T 29829-2013.信息安全技术可信计算密码支撑平台功能与接口规范[S] .北京:国家密码管理局,2007. |
| [10] | 张换梅. 可信计算密钥管理机制的研究与实现[D].北京:北京工业大学, 2011. |
| [11] | 艾俊,吴秋新. 可信计算密码支撑平台中的密钥管理技术研究[J]. 北京信息科技大学学报(自然科学版),2009(4):92-96. |
| [12] | 李新明,张功萱,施超,等. 可信计算机平台密钥管理[J]. 南京理工大学学报(自然科学版),2010(4):431~435,447. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||