Netinfo Security ›› 2016, Vol. 16 ›› Issue (4): 23-30.doi: 10.3969/j.issn.1671-1122.2016.04.004
• Orginal Article • Previous Articles Next Articles
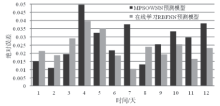
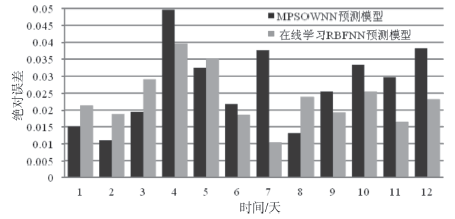
Research on Network Security Situation Prediction Technique Based on Online Learning RBFNN
Limin XUE( ), Zhong LI, Wanwan LAN
), Zhong LI, Wanwan LAN
- Information Institute, Naval Command College, Nanjing Jingsu 211800, China
-
Received:2016-03-02Online:2016-04-20Published:2020-05-13
CLC Number:
Cite this article
Limin XUE, Zhong LI, Wanwan LAN. Research on Network Security Situation Prediction Technique Based on Online Learning RBFNN[J]. Netinfo Security, 2016, 16(4): 23-30.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.04.004
| [1] | NANDA S, DEO N.A Highly Scalable Model for Network Attack Identification and Path Prediction[C]//IEEE. IEEE SoutheastCon 2007, March 22-25, 2007, Riehmond, VA. New Jersey: IEEE, 2007: 663-668. |
| [2] | PALETTA M, HERRERO P.Foreseeing Cooperation Behaviors in Collaborative Grid Environments[C]//Springer. 7th International Conference on Practical Applications of Agents and Multi-Agent Systems (PAAMS 2009), March 25-27, 2009, Spain. Heidelberg: Springer, 2009: 120-129. |
| [3] | LI Juan, LI Tao, LIANG Gang.A Network Security Dynamic Situation Forecasting Method[C]//IEEE. 2009 International Forum on Information Technology and Applications, May 15-17, 2009, Chengdu, China. New Jersey: IEEE, 2009: 115-118. |
| [4] | MAN Dapeng, WANG Yan, YANG Wu, et al.A Combined Prediction Method for Network Security Situation[C]//IEEE. 2010 International Conference on Computational Intelligence and Software Engineering (CiSE), December 10-12, 2010, Wuhan, China. New Jersey: IEEE, 2010: 1-4. |
| [5] | 吴拥民,李冬银. 基于IPSO和BPNN的网络安全态势预测[J]. 岷江学院学报,2013,34(5):78-83. |
| [6] | 曾斌,钟萍. 网络安全态势预测方法的仿真研究[J]. 计算机仿真,2012,29(5):170-173. |
| [7] | 孟锦,马驰,何加浪,等. 基于HHGA-RBF神经网络的网络安全态势预测模型[J]. 计算机科学,2011,38(7):70-75. |
| [8] | 李凯,曹阳. 基于ARIMA模型的网络安全威胁态势预测方法[J]. 计算机应用研究,2012,29(8):3042-3045. |
| [9] | 陈善学,杨政,朱江,等. 一种基于累加PSO-SVM的网络安全态势预测模型[J]. 计算机应用研究,2014,32(6):135-139. |
| [10] | 张安楠,苏旸. 基于小波变换的网络安全态势复合预测方法[J]. 计算机仿真,2014,31(6):282-286. |
| [11] | HUANG Guangbin, CHEN Lei, SIEW C K.Universal Approximation Using Incremental Constructive Feedforward Networks with Random Hidden Nodes[J]. IEEE Transactions on Neural Networks, 2006, 17(4): 879-892. |
| [12] | LAURET P, FOCK E, MARA T A.A Node Pruning Algorithm Based on a Fourier Amplitude Sensitivity Test Method[J]. IEEE Transactions on Neural Networks, 2006, 17(2): 273-293. |
| [13] | 张米娜,韩红桂,乔俊飞. 前馈神经网络结构动态增长—修剪方法[J]. 智能系统学报,2011,6(2):101-106. |
| [14] | 张昭昭,乔俊飞,杨刚. 自适应前馈神经网络结构优化设计[J]. 智能系统学报,2011,6(4):312-317. |
| [15] | 张伟,乔俊飞,李凡军. 溶解氧浓度的直接自适应动态神经网络控制方法[J]. 控制理论与应用,2015,32(1):115-121. |
| [16] | ISLAM M M, SATTAR M A, AMIN M F, et al.A New Adaptive Merging and Growing Algorithm for Designing Artificial Neural Networks[J]. IEEE Transactions on Systems, Man, and Cybernetics, Part B (Cybernetics), 2009, 39(3): 705-722. |
| [17] | BAO Jian, CHEN Yu, YU Jinshou.A Regeneratable Dynamaic Differential Evolution Algorithm for Neural Networks with Integer Weights[J]. Journal of Zhejiang University SICENCE C (Computers & Electornics), 2010, 11(12): 939-947. |
| [18] | DING Shifei, SU Chunyang, YU Junzhao.An Optimizing BP Neural Network Algorithm Based on Genetic Algorithm[J]. Artificial Intelligence Review, 2011, 36(2): 153-162. |
| [19] | 涂涓涓. PSO优化神经网络算法的研究及其应用[D]. 镇江:江苏大学,2013. |
| [20] | 张小鸣,王研顺. 改进型RBF神经网络在线的学习算法[J]. 常州大学学报(自然科学版),2014,26(6):52-56. |
| [21] | YIN H, ALLINSON N M.Self-organizing Mixture Networks for Probability Density Estimation[J]. IEEE Transactions on Neural Networks, 2001, 12(2): 405-411. |
| [22] | BORS A G, PITAS I.Median Radial Basis Function Neural Network[J]. IEEE Transactions on Neural Networks, 1996, 7(6): 1351-1364. |
| [23] | 王景中,徐友强. 基于RBF神经网络的HTTP异常行为自动识别方法[J]. 信息网络安全,2014(12):16-20. |
| [24] | 乔俊飞,韩红桂. 神经网络结构动态优化设计的分析与展望[J]. 控制理论与应用,2010,27(3):350-357. |
| [25] | 黄红梅,胡寿松. 基于在线学习RBF神经网络的故障预报[J]. 南京航空航天大学学报,2007,39(2):249-252. |
| [26] | CANO-IZQUIERDO J M, IBARROLA J, PINZOLAS M, et al. DNSP: A Biologically Inspired Dynamic Neural Network Approach to Signal Processing[J]. Neural Networks, 2008, 21(7): 1006-1019. |
| [27] | CHENG W S. Automatic Control Theory, Method and Application[M]. Beijing: Tsinghua University Press, 2009. |
| [28] | 姚洪磊,张彦. 基于BP神经网络的铁路互联网售票系统信息安全评估方法[J]. 信息网络安全,2014(7):81-86. |
| [29] | 蓝湾湾,薛丽敏. 基于改进粒子群小波神经网络的网络安全态势预测模型[J]. 大连舰艇学院学报,2015,38(5):72-76. |
| [30] | 任伟,蒋兴浩,孙锬锋. 基于RBF神经网络的网络安全态势预测方法[J]. 计算机工程与应用,2006,31(40):136-138. |
| [31] | 伍海波. 基于神经网络的检测器生成算法研究与应用[J]. 信息网络安全,2015(9):249-252. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||