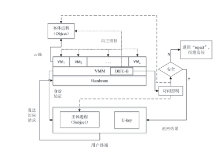
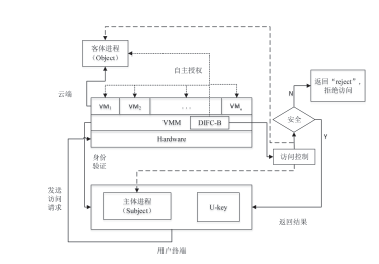
| [1] |
LIN Guoyuan, BIE Yuyu, LEI Min, et al.ACO-BTM A Behavior Trust Model in Cloud Computing Environment[J]. International Journal of Computational Intelligence Systems, 2014, 7(4):785-795
|
| [2] |
郑周,张大军,李运发. 云计算中面向数据存储的安全访问控制机制[J]. 信息网络安全,2015(9):221-226.
|
| [3] |
LIN Guoyuan, WANG Danru, BIE Yuyu, et al.A Mutual Trust Besed Access Control Model in Cloud Computing[J]. China Communications ,2014, 11(4):154-162.
|
| [4] |
张如辉,郭春梅,毕学尧. 美国政府云计算安全策略分析与思考[J]. 信息网络安全,2015(9):257-261.
|
| [5] |
BELL D E, PADULA L J L. Unified Exposition and Multics Interpretation[R]. USA: Secure Computer System. MTR2997 Rev 1, 1976.
|
| [6] |
Biba K J.Integrity Considerations for Secure Computer Systems[R]. USA: US Air Force Electronic System Division, Technical Report. MTR 3153, 1977.
|
| [7] |
MYERS A C, LISKOV B.Protecting Privacy Using the Decentralized Label Model[J]. ACM Transactions on Computer Systems, 2000, 9(4):410-442.
|
| [8] |
武少杰. 云计算下虚拟环境安全的关键技术研究[D].郑州:解放军信息工程大学,2012.
|
| [9] |
姜路,鹤荣育.云计算中动态完整性传递模型研究[J].计算机应用研究,2014,31(5):1503-1510.
|
| [10] |
邵婧,陈性元,杜学绘,等.基于无干扰理论的分布式多级安全核心架构[J].计算机应用,2013,33(3):712-716.
|
| [11] |
SHI Q, ZHANG N.An effective model for composition of secure systems[J]. The Journal of Systems and Software, 1998, 43(3) :233-244.
|
| [12] |
LU W P, SUNDARESHAN M K.A model for multilevel security in computer networks[J]. IEEE Transactions on Software Engineering, 1990, 16(6): 647-659.
|
| [13] |
LEVIN TE,IRVINE CE, NGUYEN TD.Least Privilege in Separation Kernels [C]//IEEE. Proceedings of the IEEE International Conference on Security and Cryptography. Piscataway, NJ: IEEE Press, 2006: 355-362.
|
| [14] |
RUSHBY J. Noninterference, Transitivity,Channel-control Security Policies[R]. Menlo Park: Stanford Research Institute, CSL-92-02, 1992.
|
| [15] |
DIJKSTRA E W.Hierarchical Ordering of Sequential Processes. Operating System Techniques, 1972.
|
| [16] |
GOGUEN J A, MESEGUER J.Security policies and security models[C] //IEEE. Proc of the 1982 IEEE Symp on Security and Privacy. Los Alamitos, CA: IEEE Computer Society, 1982: 11-20.
|
| [17] |
HAIGH J T, YONG W D.Extending the Noninterference Model of MLS for SAT[C]//IEEE. Proceeding of the Symposium on Security and Privacy. CA: IEEE Software Engineering, 1987:141-150.
|
| [18] |
Saydjari O S.Multilevel Security: Reprise[J]. Security & Privacy, 2004, 2(5):64-67.
|
 ), LI Zhengkui1
), LI Zhengkui1