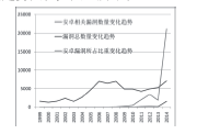
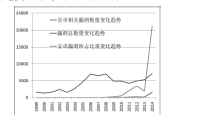
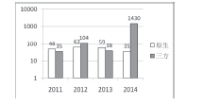
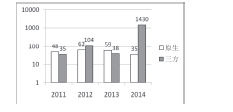
| [1] |
YAN L K, YIN Heng.DroidScope:seamlessly reconstructing the OS and Dalvik semantic views for dynamic Android malware analysis[C] //Proc of the 21st USENIX Security Symposium. Berkeley:USENIX Association, 2012:135-146.
|
| [2] |
The Open Source Vulnerability Database (OSVDB) [EB/OL]. .
|
| [3] |
张金鑫,杨晓辉. 基于权限分析的Android应用程序检测系统[J]. 信息网络安全,2014,(7):30-34.
|
| [4] |
National security vulnerability database[EB/OL]. .
|
| [5] |
高岳,胡爱群. 基于权限分析的Android隐私数据泄露动态检测方法[J]. 信息网络安全,2014,(2):27-31.
|
| [6] |
NSFocus [EB/OL]. .
|
| [7] |
张玉清,吴舒平,刘奇旭,等. 国家安全漏洞库的设计与实现[J]. 通信学报,2011,32(6): 93-100.
|
| [8] |
ZHAO D Y, FURNELL S M, AL-AYED A.The Research on a Patch Management System for Enterprise Vulnerability Update. Proc of Information Engineering, 2009. ICIE '09. WASE International Conference: 2[C]. Taiyuan, Chanxi: IEEE, 2009: 250-253.
|
| [9] |
王晓甜,张玉清. 安全漏洞自动收集系统的设计与实现[J]. 计算机工程. 2006(20):177-179
|
| [10] |
张玉清,王凯,杨欢,等. Android安全综述[J]. 计算机研究与发展. 2014,(07)
|
| [11] |
赵洋,胡龙,熊虎,等. 基于沙盒的Android恶意软件动态分析方案[J]. 信息网络安全,2014,(12):21-26.
|
| [12] |
CHEN Z Q, ZHANG Y, CHEN Z R.A Categorization Framework for Common Computer Vulnerabilities and Exposures[J]. The Computer Journal, 2010, 53(5): 551-580.
|
| [13] |
WU W, YIP F, YIU E, et al.Integrated Vulnerability Management System for Enterprise Networks. Proc of e-Technology, e-Commerce and e-Service, 2005. EEE '05. Proceedings. The 2005 IEEE International Conference[C]. IEEE, 2005: 698-703.
|
| [14] |
包佳敏,胡爱群. Android系统文件监听技术的研究[J]. 信息网络安全,2014,(3):46-51.
|
| [15] |
翟钰,张玉清,武维善,等. 系统安全漏洞研究及数据库实现[J]. 计算机工程, 2004, 30(8): 68-70.
|
| [16] |
徐剑,武爽,孙琦,等. 面向Android应用程序的代码保护方法研究[J]. 信息网络安全,2014,(10):11-17.
|
 ), Tao WEN2, Yu-qing ZHANG1,2
), Tao WEN2, Yu-qing ZHANG1,2