Netinfo Security ›› 2015, Vol. 15 ›› Issue (9): 97-100.doi: 10.3969/j.issn.1671-1122.2015.09.023
• Orginal Article • Previous Articles Next Articles
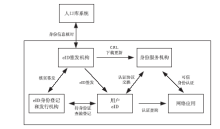
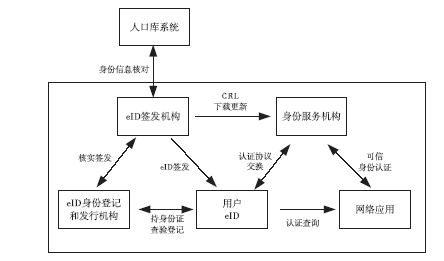
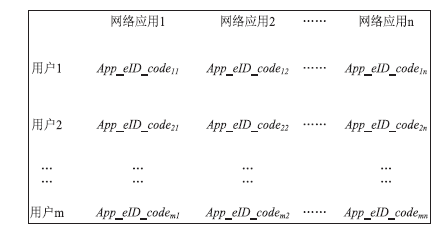
Research on Trusted Identity Architecture in Cyberspace Based on eID
Zhi-peng WANG, Ming-hui YANG, Liang LV( )
)
- Third Research Institute of Ministry of Public Security, Shanghai 201204, China