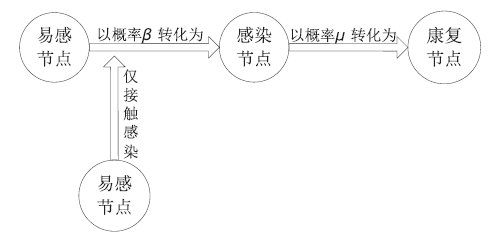
Netinfo Security ›› 2015, Vol. 15 ›› Issue (5): 47-55.doi: 10.3969/j.issn.1671-1122.2015.05.008
Previous Articles Next Articles
A Survey of Information Diffusion Prediction in Online Social Networks
WANG Le, WANG Yong( ), WANG Dong-an, XU Xiao-lin
), WANG Dong-an, XU Xiao-lin
- Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
-
Received:2015-04-09Online:2015-05-10Published:2018-07-16
CLC Number:
Cite this article
WANG Le, WANG Yong, WANG Dong-an, XU Xiao-lin. A Survey of Information Diffusion Prediction in Online Social Networks[J]. Netinfo Security, 2015, 15(5): 47-55.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.05.008
| [1] | WU S, Hofman J M, Mason W A, et al.Who says what to whom on twitter[C]//Proceedings of the 20th international conference on World wide web. ACM, 2011: 705-714. |
| [2] | KATZ E.The two-step flow of communication: An up-to-date report on an hypothesis[J]. Public Opinion Quarterly, 1957, 21(1): 61-78. |
| [3] | SUH B, HONG L, PIROLLI P, et al.Want to be retweeted? large scale analytics on factors impacting retweet in twitter network[C]//Social computing (socialcom), 2010 ieee second international conference on. IEEE, 2010: 177-184. |
| [4] | WENG J, LIM E P, JIANG J, et al.Twitterrank: finding topic-sensitive influential twitterers[C]//Proceedings of the third ACM international conference on Web search and data mining. ACM, 2010: 261-270. |
| [5] | CHA M, HADDADI H, BENEVENUTO F, et al.Measuring User Influence in Twitter: The Million Follower Fallacy[J]. ICWSM, 2010, 10(10-17): 30. |
| [6] | KWAK H, LEE C, PARK H, et al.What is Twitter, a social network or a news media?[C]//Proceedings of the 19th international conference on World wide web. ACM, 2010: 591-600. |
| [7] | BAKSHY E, HOFMANn J M, MASON W A, et al.Everyone's an influencer: quantifying influence on twitter[C]//Proceedings of the fourth ACM international conference on Web search and data mining. ACM, 2011: 65-74. |
| [8] | YU L, ASUR S, HUBERMAN B A. What trends in Chinese social media[C]//Proceedings of The fifth ACM workshop on Social Network Mining and Analysis.ACM, 2011: 978-1-4503-0225-8. |
| [9] | 曹玖新,吴江林,石伟,等. 新浪微博网信息传播分析与预测[J]. 计算机学报,2014,37(4):5. |
| [10] | CONOVER M D, GONCALVES B, RATKIEWICZ J, et al.Predicting the political alignment of twitter users[C]//Proceedings of 3rd IEEE Conference on Social Computing (SocialCom), 2011: 192-199. |
| [11] | BAKSHY E, ROSENN I, MARLOW C, et al.The role of social networks in information diffusion[C]//Proceedings of the 21st international conference on World Wide Web. ACM, 2012: 519-528. |
| [12] | CHENG J, ADAMIC L, DOW P A, et al.Can cascades be predicted?[C]//Proceedings of the 23rd international conference on World wide web. International World Wide Web Conferences Steering Committee, 2014: 925-936. |
| [13] | LESKOVEC J, MCGLOHON M, FALOUTSOS C, et al. Cascading Behavior in Large Blog Graphs[EB/OL]. . |
| [14] | XIONG F, LIU Y, ZHANG Z, et al.An information diffusion model based on retweeting mechanism for online social media[J]. Physics Letters A, 2012, 376(30): 2103-2108. |
| [15] | WANG H, LI Y P, FENG Z N, et al.ReTweeting analysis and prediction in microblogs: An epidemic inspired approach[J]. China Communications, 2013, 10(3): 13-24. |
| [16] | WANG F, WANG H, XU K.Diffusive logistic model towards predicting information diffusion in online social networks[C]//Distributed Computing Systems Workshops (ICDCSW), 2012 32nd International Conference on. IEEE, 2012: 133-139. |
| [17] | ZAMAN T R, HERBRICH R, VAN G J, et al.Predicting information spreading in twitter[C]//Workshop on computational social science and the wisdom of crowds, nips. 2010, 104(45): 17599-601. |
| [18] | PENG H K, ZHU J, PIAO D, et al.Retweet modeling using conditional random fields[C]//Data Mining Workshops (ICDMW), 2011 IEEE 11th International Conference on. IEEE, 2011: 336-343. |
| [19] | ZHU J, XIONG F, PIAO D Z, et al.Statistically modeling the effectiveness of disaster information in social media.[C]//IEEE Global Humanitarian Technology Conference, 2011:431-436. |
| [20] | PETROVIC S, OSBOME M, LAVRENKO V. RT to win! Predicting message propagation in twitter[EB/OL]. . |
| [21] | HONG L, DAN O, DAVISON B D.Predicting popular messages in twitter[C]//Proceedings of the 20th international conference companion on World wide web. ACM, 2011: 57-58. |
| [22] | TSUR O, RAPPOPORT A.What's in a hashtag?: content based prediction of the spread of ideas in microblogging communities[C]//Proceedings of the fifth ACM international conference on Web search and data mining. ACM, 2012: 643-652. |
| [23] | LAGNIER C, DENOYER L, GAUSSIER E, et al.Predicting information diffusion in social networks using content and user's profiles[C]//European Conference on Information Retrieval, Moscou, Russia. Mar 2013: 74-85. |
| [24] | MA Z, SUN A, CONG G.On predicting the popularity of newly emerging hashtags in twitter[J]. Journal of the American Society for Information Science and Technology, 2013, 64(7): 1399-1410. |
| [25] | YANG Z, GUO J, CAI K, et al.Understanding retweeting behaviors in social networks[C]//Proceedings of the 19th ACM international conference on Information and knowledge management. ACM, 2010: 1633-1636. |
| [26] | WANG J, Li W, Weili W.Predicting Information Popularity Degree in Microblogging Diffusion Networks[J]. International Journal of Multimedia & Ubiquitous Engineering, 2014, 9(2):21. |
| [27] | LU X, YU Z, GUO B, et al.Predicting the content dissemination trends by repost behavior modeling in mobile social networks[J]. Journal of Network and Computer Applications, 2014, 42: 197-207. |
| [28] | CUI P, JIN S, YU L, et al.Cascading outbreak prediction in networks: a data-driven approach[C]//Proceedings of the 19th ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2013: 901-909. |
| [29] | GUILLE A, HACID H, FAVRE C, et al.Information diffusion in online social networks: A survey[J]. ACM SIGMOD Record, 2013, 42(2): 17-28. |
| [30] | GOMEZ R M, LESKOVEC J, KRAUSE A.Inferring networks of diffusion and influence[C]//Proceedings of the 16th ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2010: 1019-1028. |
| [31] | MYERS S, LESKOVEC J.On the convexity of latent social network inference[C]//Advances in Neural Information Processing Systems. 2010: 1741-1749. |
| [32] | RODRIGUEZ M G, BALDUZZI D, SCHOLKOPF B. Uncovering the temporal dynamics of diffusion networks[J]. arXiv preprint arXiv:1105.0697, 2011. |
| [33] | RODRIGUEZ M G, SCHOLKOPF B. Submodular inference of diffusion networks from multiple trees[J]. arXiv preprint arXiv:1205.1671, 2012. |
| [34] | LESKOVEC J, SCHOLKOPF B.Structure and Dynamics of Information pathways in online media[C]//Proceedings of the sixth ACM international conference on Web search and data mining. ACM, 2013: 23-32. |
| [35] | KIMURA M, SAITO K, OHARA K, et al.Learning information diffusion model in a social network for predicting influence of nodes[J]. Intelligent Data Analysis, 2011, 15(4): 633-652. |
| [36] | WANG S, HU X, YU P S, et al.MMRate: inferring multi-aspect diffusion networks with multi-pattern cascades[C]//Proceedings of the 20th ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2014: 1246-1255. |
| [37] | KEMPE D, KLEINBERG J, TARDOS É.Maximizing the spread of influence through a social network[C]//Proceedings of the ninth ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2003: 137-146. |
| [38] | GALUBA W, ABERER K, CHAKRABORTY D, et al.Outtweeting the twitterers-predicting information cascades in microblogs[C]//Proceedings of the 3rd conference on Online social networks. 2010: 3. |
| [39] | SAITO K, KIMURA M, OHARA K, et al.Selecting information diffusion models over social networks for behavioral analysis[M]. Machine Learning and Knowledge Discovery in Databases. Springer Berlin Heidelberg, 2010: 180-195. |
| [40] | DICKENS L, MOLLOY I, LOBO J, et al.Learning stochastic models of information flow[C]//Data Engineering (ICDE), 2012 IEEE 28th International Conference on. IEEE, 2012: 570-581. |
| [41] | GUILLE A, HACID H.A predictive model for the temporal dynamics of information diffusion in online social networks[C]//Proceedings of the 21st international conference companion on World Wide Web. ACM, 2012: 1145-1152. |
| [42] | YANG J, LESKOVEC J.Modeling information diffusion in implicit networks[C]//Data Mining (ICDM), 2010 IEEE 10th International Conference on. IEEE, 2010: 599-608. |
| [43] | BIAN J, YANG Y, CHUA T S.Predicting trending messages and diffusion participants in microblogging network[C]//Proceedings of the 37th international ACM SIGIR conference on Research & development in information retrieval. ACM, 2014: 537-546. |
| [44] | 杨佳玉,叶昕昕,陈思聪,等. 社交网站安全问题分析与对策研究[J]. 信息网络安全,2014,(4):82-87. |
| [45] | 钟玲,林柏钢. 社交网Twitter平台的人物关系网社区发现[J]. 信息网络安全,2014,(5):32-36. |
| [46] | 薛一波,鲍媛媛,易成岐. SPNR:社交网络中的新型谣言传播模型[J]. 信息网络安全,2014,(1):5-9. |
| [47] | 刘东亮,马春光. 基于NS-3的机会网络路由协议仿真[J]. 信息网络安全,2014,(5):52-58. |
| [48] | KHALIL E B, DILKINA B, SONG L.Scalable diffusion-aware optimization of network topology[C]//Proceedings of the 20th ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2014: 1226-1235. |
| [49] | 周永进,马春光,苗俊峰,等. 基于社区层次的机会网络移动模型[J]. 信息网络安全,2014,(8):45-49. |
| [50] | 齐峰,马春光,周永进,等. 一种基于网络编码的机会社会网络路由算法[J]. 信息网络安全,2015,(2):51-56. |
| [51] | 王明元,贾焰,周斌,等. 一种基于主题相关性分类的微博话题立场研判方法[J]. 信息网络安全,2014,(9):17-21. |
| [52] | 严岭,李逸群. 网络舆情事件中的微博炒作账号发现方法研究[J]. 信息网络安全,2014,(9):26-29. |
| [53] | 柳俊,周斌,黄九鸣. 基于二部图投影的微博事件关联分析方法研究[J]. 信息网络安全,2014,(9):44-49. |
| [54] | 郑飞,张蕾. 基于分类的中文微博热点话题发现方法研究[J]. 信息网络安全,2014,(9):127-131. |
| [55] | MYERS S A, LESKOVEC J.Clash of the contagions: Cooperation and competition in information diffusion[C]//ICDM. 2012, 12: 539-548. |
| [56] | RONG X, MEI Q.Diffusion of innovations revisited: from social network to innovation network[C]//Proceedings of the 22nd ACM international conference on Conference on information & knowledge management. ACM, 2013: 499-508. |
| [57] | MYERS S A, ZHU C, LESKOVEC J.Information diffusion and external influence in networks[C]//Proceedings of the 18th ACM SIGKDD international conference on Knowledge discovery and data mining. ACM, 2012: 33-41. |
| [58] | 孙兴东,李爱平,李树栋. 一种基于聚类的微博关键词提取方法的研究与实现[J]. 信息网络安全,2014,(12):27-31. |
| [59] | 李凌云,敖吉,乔治,等. 基于微博的安全事件实时监测框架研究[J]. 信息网络安全,2015,(1):16-23. |
| [60] | 李迎涛,马春光,李增鹏. 基于域划分和接口分离的涉密信息系统边界防护技术[J]. 信息网络安全,2014.(1):25-29. |
| [61] | 刘楠,韩丽芳,夏坤峰,等. 一种改进的基于抽象语法树的软件源代码比对算法[J]. 信息网络安全,2014.(1):38-42. |
| [62] | 张涛,焦英楠,禄立杰,等. 一种基于Windows内核驱动的可疑样本采集系统的设计与实现[J]. 信息网络安全,2014,(2):41-47. |
| [63] | 张涛,牛伟颖,孟正,等. 基于Windows内核模式下进程监控的用户权限控制系统设计与实现[J]. 信息网络安全,2014,(4):13-19. |
| [64] | 孙哲,刘大光,武学礼,等. 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. 信息网络安全,2014,(6):23-30. |
| [1] | WU Wei, XU Shasha, GUO Sensen, LI Xiaoyu. Research on Hybrid Recommendation Algorithm for Points of Interest in Location-Based Social Network [J]. Netinfo Security, 2023, 23(9): 75-84. |
| [2] | MA Xiangjun, HE Jingsha, WU Tiejun, FAN Dunqiu. An Approach to Identifying Key Hackers in Social Networks [J]. Netinfo Security, 2023, 23(1): 57-65. |
| [3] | XIONG Jianying. Reputation Evaluation Model in Social Network Based on Information Behavior [J]. Netinfo Security, 2021, 21(12): 51-59. |
| [4] | XIA Tianyu, GU Yijun. A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model [J]. Netinfo Security, 2020, 20(9): 97-101. |
| [5] | Jingjie MO, Chenyang TU, Jia PENG, Jun YUAN. Social Network Mining Based on Multi-source Information Fusion [J]. Netinfo Security, 2017, 17(9): 73-76. |
| [6] | Guojun MA, Kai LI, Qingqi PEI, Yang ZHAN. A Fine-Grained Face Privacy Protection Scheme in Social Networks [J]. Netinfo Security, 2017, 17(8): 26-32. |
| [7] | Hao LIU, Zhigang CHEN, Lianming ZHANG. A Secure Routing Algorithm of Mobile Social Network Based on Community [J]. Netinfo Security, 2017, 17(7): 25-31. |
| [8] | Yanping YANG. The Algorithm of Social Network Users Reliability Based on Bidirectional Weighted Graph [J]. Netinfo Security, 2017, 17(7): 40-44. |
| [9] | Qing LI, A-yong YE, Li XU. Research on Privacy Attack Based on Location Cheating in Social Network [J]. Netinfo Security, 2017, 17(5): 51-56. |
| [10] | Jinbo XIONG, Rong MA, Yuanyuan ZHANG, Ruiyu DAI. Image Information Hiding Method and Implementation for Social Network [J]. Netinfo Security, 2017, 17(3): 6-8. |
| [11] | Liang LUO, Wenxian WANG, Jie ZHONG, Haizhou WANG. Research on Users Associated Technology across Social Network [J]. Netinfo Security, 2017, 17(2): 51-58. |
| [12] | Ye LOU. Research on Public Opinion Guide Control Strategy Based on Information Dissemination Model [J]. Netinfo Security, 2016, 16(9): 257-266. |
| [13] | Yang QU, Yongjian WANG, Ruxiang PENG, Guoqing JIANG. Construction and Data Mining of Social Network Based on Communication Log [J]. Netinfo Security, 2016, 16(6): 68-73. |
| [14] | Wei XU, Bo-gang LIN, Si-juan LIN, Yang YANG. Research on Community Detection Method for Social Networks Based on User Interaction and Similarity [J]. Netinfo Security, 2015, 15(7): 77-83. |
| [15] | LI Xun, XU Jian, JIAO Ying-nan, YAN Han-bing. Research on Detection of Social Web Page Based on Abnormal Characteristics [J]. Netinfo Security, 2015, 15(5): 41-46. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||