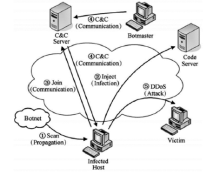
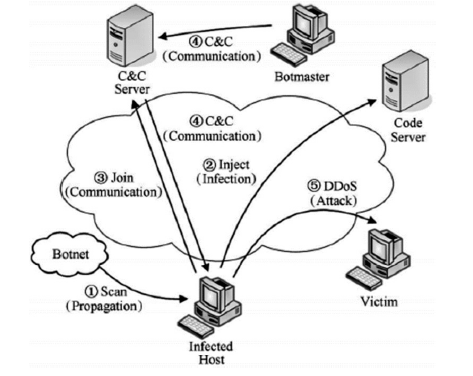
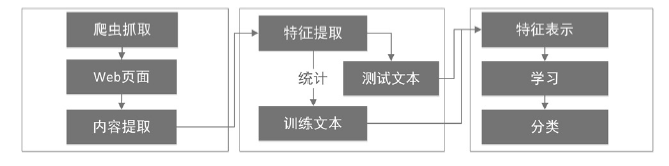
| [1] |
Abu R M, Zarfoss J, Monrose F, et al.A multifaceted approach to understanding the botnet phenomenon[C]//Proceedings of the 6th ACM SIGCOMM conference on Internet measurement. ACM, 2006: 41-52.
|
| [2] |
江健, 诸葛建伟, 段海新, 等. 僵尸网络机理与防御技术[J]. 软件学报, 2012, 23(1): 82-96.
|
| [3] |
Geer D.Malicious bots threaten network security[J]. Computer, 2005, 38(1): 18-20.
|
| [4] |
Han X, Guo J, Zhou Y, et al.Investigation on the botnets activities[J]. JOURNAL-CHINA INSTITUTE OF COMMUNICATIONS, 2007, 28(12): 167.
|
| [5] |
诸葛建伟, 韩心慧, 周勇林, 等. 僵尸网络研究[J] .软件学报, 2008, 19(3): 702-715.
|
| [6] |
Athanasopoulos E, Makridakis A, Antonatos S, et al.Antisocial networks: Turning a social network into a botnet[M].Heidelberg: Springer Berlin, 2008.
|
| [7] |
Govil J, Govil J .Criminology of botnets and their detection and defense methods[C] //Proc of 2007 IEEE Int Conf on Electro/Information Technology (EIT 2007).Washington, DC: IEEE Computer Society, 2007: 215-220.
|
| [8] |
Govil J.Examining the criminology of bot zoo[C]//Information, Communications & Signal Processing, 2007 6th International Conference on. IEEE, 2007: 1-6.
|
| [9] |
Gu G, Perdisci R, Zhang J, et al.BotMiner: Clustering Analysis of Network Traffic for Protocol-and Structure-Independent Botnet Detection[C]//USENIX Security Symposium. 2008, 5(2): 139-154.
|
| [10] |
Holz T, Steiner M, Dahl F, et al.Measurements and Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm[J]. LEET, 2008, 8(1): 1-9.
|
| [11] |
Arce I, Levy E.An analysis of the slapper worm[J]. Security & Privacy, IEEE, 2003, 1(1): 82-87.
|
| [12] |
Barford P, Yegneswaran V.An inside look at botnets[M].New York: Malware Detection. Springer US, 2007.
|
| [13] |
方滨兴, 崔翔, 王威. 僵尸网络综述[J]. 计算机研究与发展, 2011, 48(8):1315-1331.
|
| [14] |
Stover S, Dittrich D, Hernandez J, et al.Analysis of the Storm and Nugache Trojans: P2P is here[J]. USENIX; login, 2007, 32(6): 18-27.
|
| [15] |
Holz T, Steiner M, Dahl F, et al.Measurements and Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm[J]. LEET, 2008, 8(1): 1-9.
|
| [16] |
Kanich C, Kreibich C, Levchenko K, et al.Spamalytics: An empirical analysis of spam marketing conversion[C]//Proceedings of the 15th ACM conference on Computer and communications security. ACM, 2008: 3-14.
|
| [17] |
Turner D, Fossi M, Johnson E, et al. Symantec global internet security threat report-trends for 2008[EB/OL]..
|
| [18] |
Cooke E, Jahanian F, McPherson D. The zombie roundup: Understanding, detecting, and disrupting botnets[C]//Proceedings of the USENIX SRUTI Workshop. 2005, (39): 44.
|
| [19] |
Chiang K, Lloyd L.A case study of the rustock rootkit and spam bot[C]//The First Workshop in Understanding Botnets. 2007.
|
| [20] |
Daswani N, Stoppelman M.The anatomy of Clickbot. A[C]//Proceedings of the first conference on First Workshop on Hot Topics in Understanding Botnets. USENIX Association, 2007: 11.
|
| [21] |
Kartaltepe E J, Morales J A, Xu S, et al.Social network-based botnet command-and-control: emerging threats and countermeasures[C]//Applied Cryptography and Network Security. Springer Berlin Heidelberg, 2010: 511-528.
|
| [22] |
王海龙, 龚正虎, 侯婕.僵尸网络检测技术研究进展[J].计算机研究与发展, 2010, 47(12) : 2037-2048.
|
| [23] |
Binkley J R, Singh S.An algorithm for anomaly-based botnet detection[C]//Proceedings of USENIX Steps to Reducing Unwanted Traffic on the Internet Workshop (SRUTI), 2006: 43-48.
|
| [24] |
Strayer W T, Walsh R, Livadas C, et al.Detecting botnets with tight command and control[C]// Proceedings 2006 31st IEEE Conference on. IEEE, 2006: 195-202.
|
| [25] |
Livadas C, Walsh R, Lapsley D, et al.Usilng machine learning technliques to identify botnet traffic[C]// Proceedings 2006 31st IEEE Conference on. IEEE, 2006: 967-974.
|
| [26] |
Goebel J, Holz T.Rishi: Identify bot contaminated hosts by IRC nickname evaluation[C]// Proceedings of the first conference on First Workshop on Hot Topics in Understanding Botnets. 2007: 8.
|
| [27] |
Gu G, Porras P A, Yegneswaran V, et al.BotHunter: Detecting Malware Infection Through IDS-Driven Dialog Correlation[C]//Usenix Security. 2007,(7): 1-16.
|
| [28] |
Lee J S, Jeong H C, Park J H, et al.The activity analysis of malicious http-based botnets using degree of periodic repeatability[C]// International Conference on. IEEE, 2008: 83-86.
|
| [29] |
Gu G, Zhang J, Lee W.BotSniffer: Detecting botnet command and control channels in network traffic[C]//Proc of the 15th Annual Network and Distributed System Security Symp. Berkeley, CA: USENIX,2008:269-286.
|
| [30] |
张昊,陶然,李志勇,等. 判断矩阵法在网页恶意脚本检测中的应用[J].兵工学报,2008, 29(4): 469-473.
|
| [31] |
王松. 基于学习的恶意网页智能检测系统[D].南京:南京理工大学, 2011.
|
| [32] |
Salton G, Wong A, Yang C S.On the specification of term values in automatic indexing[J].Journal of Documentation,1973,29(4): 351-372.
|
| [33] |
Soucy P, Mineau G W.A simple KNN algorithm for text categorization[C]//Proceedings IEEE International Conference on. IEEE, 2001: 647-648.
|
| [34] |
Chang C C, Lin C J.LIBSVM: a library for support vector machines[J]. ACM Transcations on Intelligent Systems and Technology(TIST), 2011, 2(3): 27.
|
 ), JIAO Ying-nan2, YAN Han-bing2
), JIAO Ying-nan2, YAN Han-bing2