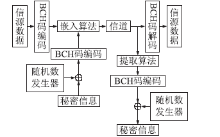
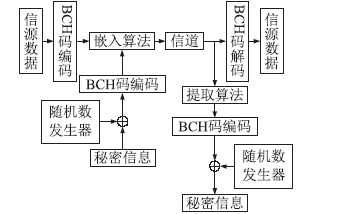
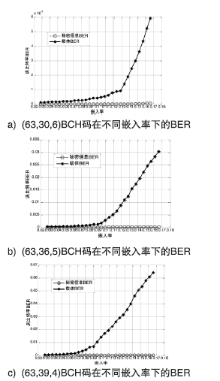
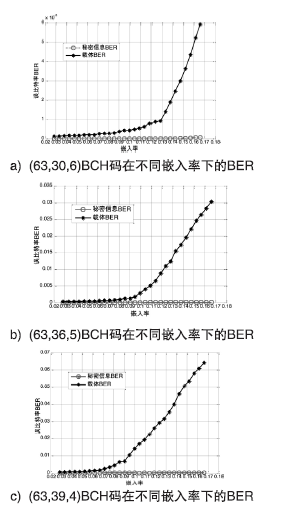
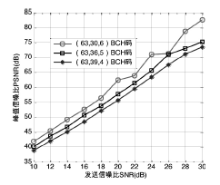
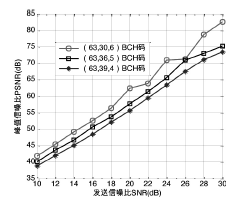
| [1] |
Moulin P, O'Sullivan JA. Information-theoretic analysis of information hiding[J]. IEEE Transactions on Information Theory, 2003; 49(3): 563-593.
|
| [2] |
Xiaolong Li, Bin Yang, Zeng T.General framework to histogram-shifting-based reversible data hiding[J]. IEEE Transactions on Image Processing 2013; 22(6): 2181-2191.
|
| [3] |
Khodaei M, Faez K.New adaptive steganographic method using least-significant-bit substitution and pixel-value differencing[J]. IET Image Processing, 2012, 6(6): 677-686.
|
| [4] |
Fangjun H, Jiwu H, Yun-Qing S.New Channel Selection Rule for JPEG Steganography[J]. IEEE Transactions on Information Forensics and Security, 2012; 7(4): 1181-1191.
|
| [5] |
Lalitha N V, Rao S, JayaSree P V Y. DWT—Arnold Transform based audio watermarking[C], 2013 IEEE Asia Pacific Conference on Postgraduate Research in Microelectronics and Electronics, 19-21 Dec, 2013: 196-199.
|
| [6] |
王天宇,刘玉君,唐冬明,等. 基于RS码的有扰信道信息隐藏技术的研究[J]. 信息工程大学学报, 2004,5(3):85-88.
|
| [7] |
王晓飞. 基于信道编码的信息隐藏技术研究 [D],哈尔滨:哈尔滨工业大学, 2009.
|
| [8] |
闫雪虎. 基于纠错码的信息隐藏容量模型[J]. 计算机工程, 2010, 36(3): 172-176.
|
| [9] |
陈立全,卢苗,胡爱群,等. 基于二级定位的编码信道信息隐藏算法[J]. 通信学报,2013,34(12):120-130.
|
| [10] |
Zhou Wang, Alan Conrad Bovik, Hamid Rahim Sheikh, P.Simoncelli E. Image quality assessment: From error visibility to structural similarity[J]. IEEE Transactions on Image Processing, 2004, 13(4): 600-612.
|
| [11] |
Pevny T, Bas P, Fridrich J.Steganalysis by Subtractive Pixel Adjacency Matrix[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 215-224.
|
| [12] |
张军, 熊枫, 张丹. 图像隐写分析技术综述[J]. 计算机工程, 2013, 39(4): 165-168.
|
| [13] |
佟雨兵,张其善,祁云平. 基于PSNR与SSIM联合的图像质量评价模型[J]. 中国图象图形学报,2006, 11(12):1758-1763.
|