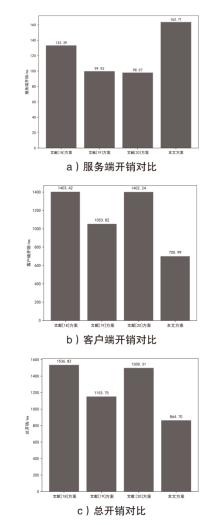
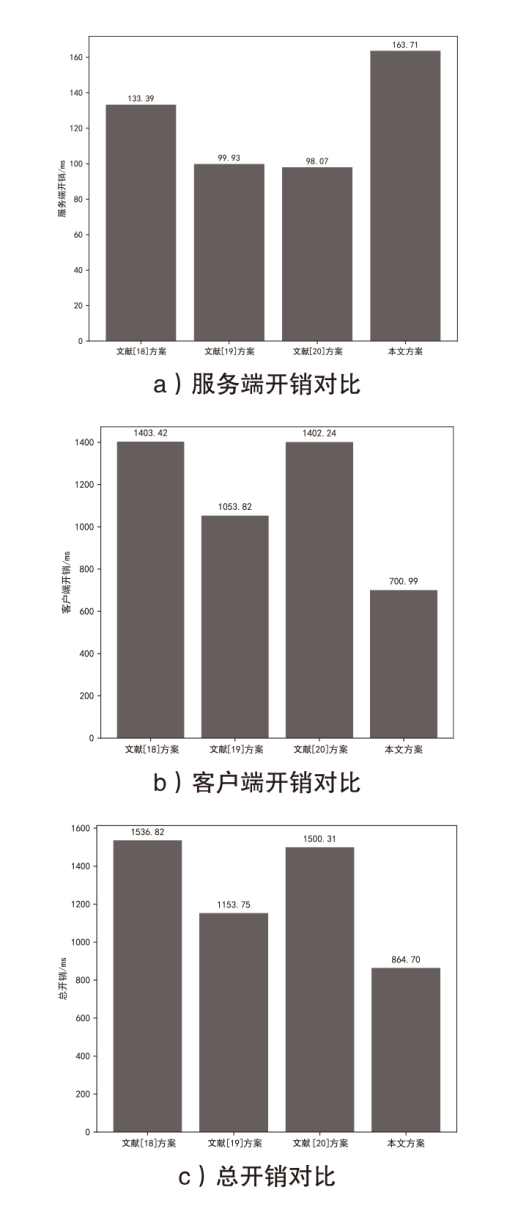
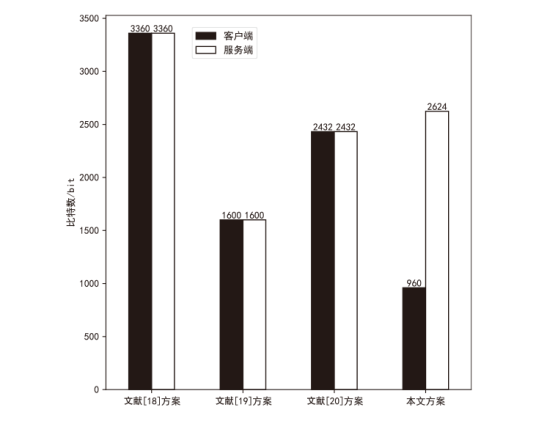
信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 817-827.doi: 10.3969/j.issn.1671-1122.2025.05.013
基于可信数字身份的轻量级分布式认证方案
- 1.北京交通大学网络空间安全学院,北京 100044
2.北京交通大学软件学院,北京 100044
-
收稿日期:2025-03-06出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:朱晓强xqzhu@bjtu.edu.cn -
作者简介:朱晓强(1992—),男,黑龙江,助理教授,博士,主要研究方向为物联网、机器学习、隐私保护|张皓文(1998—),男,山西,硕士研究生,主要研究方向为区块链及安全技术|林彦孜(2005—),女,广西,本科,主要研究方向为区块链|刘吉强(1973—),男,山东,教授,博士,主要研究方向为可信计算、隐私保护、云计算 -
基金资助:国家自然科学基金(62401037);国家重点研发计划(2023YFB2703702);北京交通大学人才基金(2023XKRC016);中国博士后科学基金(GZC20230224);中国博士后科学基金(2024M750166)
Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity
ZHU Xiaoqiang1( ), ZHANG Haowen2, LIN Yanzi2, LIU Jiqiang1
), ZHANG Haowen2, LIN Yanzi2, LIU Jiqiang1
- 1. School of Cyberspace Science and Technology, Beijing Jiaotong University, Beijing 100044, China
2. School of Software, Beijing Jiaotong University, Beijing 100044, China
-
Received:2025-03-06Online:2025-05-10Published:2025-06-10
摘要:
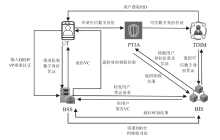
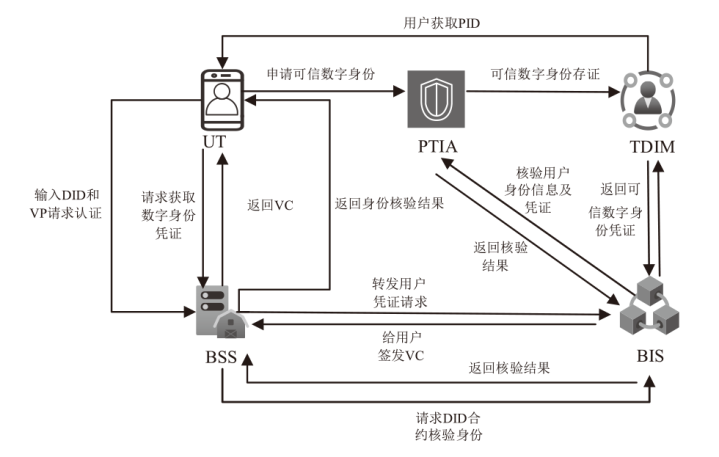
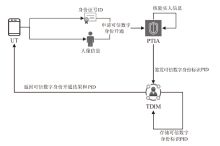
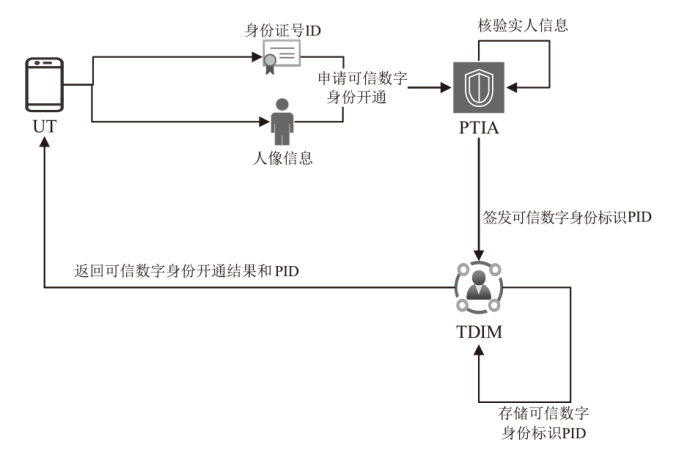
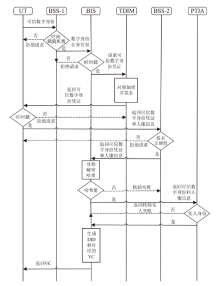
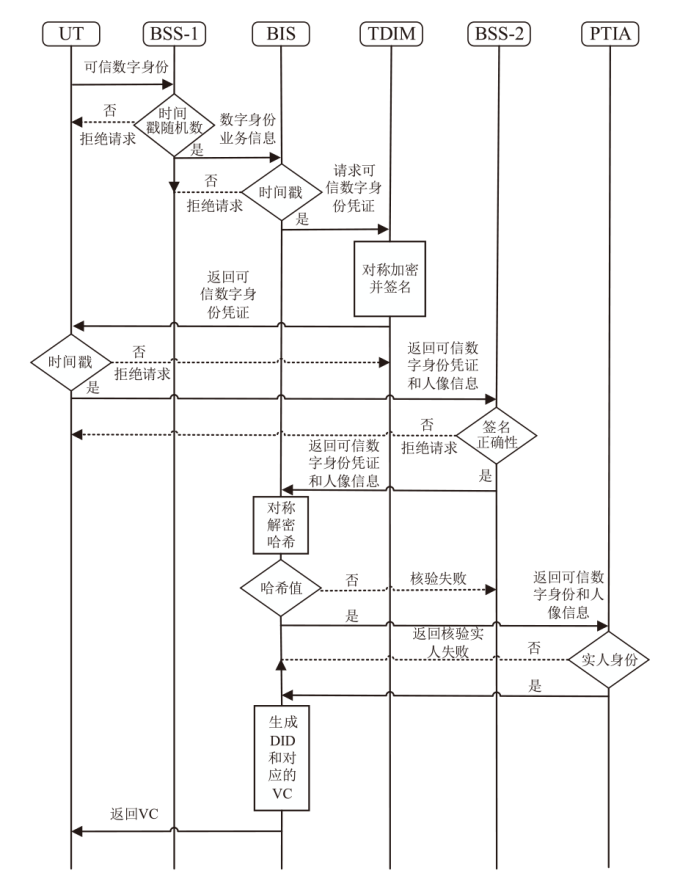
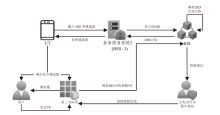
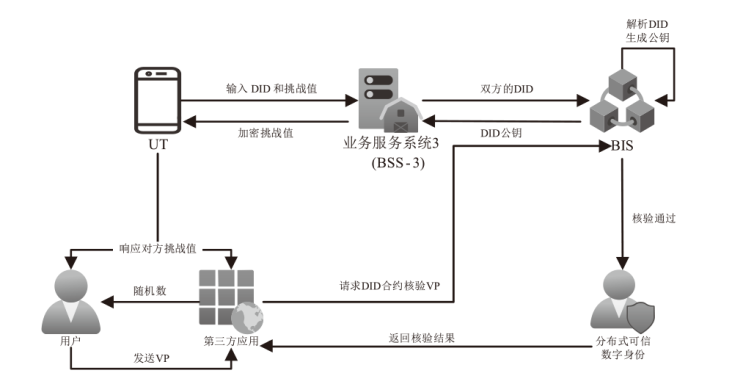
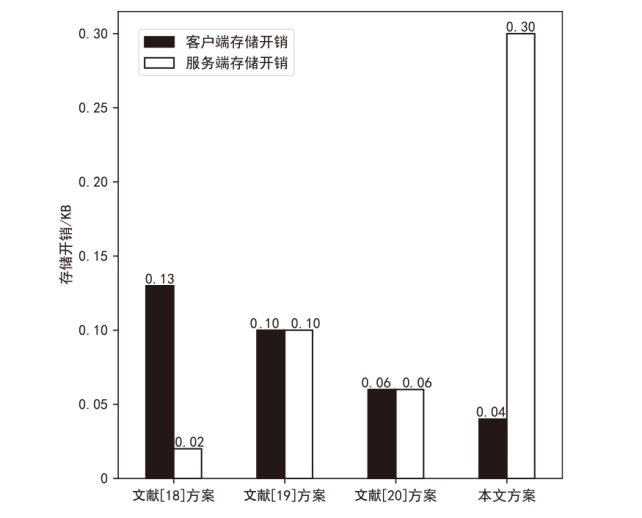
可信数字身份是现实生活和网络行为的通用凭证。随着分布式系统的普及应用,传统的数字身份管理系统存在单点故障、缺乏互操作性、侵犯隐私等安全挑战。因此,如何在可信数字身份认证过程中保护用户个人隐私,同时减少系统资源开销,提高认证效率至关重要。文章针对身份认证的典型应用场景,提出一种基于可信数字身份的轻量级分布式认证方案。该方案以可信数字身份为基础,映射成去中心化标识符,并结合可验证凭证用于可信数字身份的验证。用户可以基于实人认证控制自己的身份,实现以用户为中心的身份验证。安全性分析和性能分析表明,该方案具有较高的安全性和较好的性能。
中图分类号:
引用本文
朱晓强, 张皓文, 林彦孜, 刘吉强. 基于可信数字身份的轻量级分布式认证方案[J]. 信息网络安全, 2025, 25(5): 817-827.
ZHU Xiaoqiang, ZHANG Haowen, LIN Yanzi, LIU Jiqiang. Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity[J]. Netinfo Security, 2025, 25(5): 817-827.
| [1] | PODGORELEC B, ALBER L, ZEFFERER T. What is A (Digital) Identity Wallet?A Systematic Literature Review[C]// IEEE. 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC). New York: IEEE, 2022: 809-818. |
| [2] | WANG Miaomiao, RUI Lanlan, YANG Yang, et al. A Blockchain-Based Multi-CA Cross-Domain Authentication Scheme in Decentralized Autonomous Network[J]. IEEE Transactions on Network and Service Management, 2022, 19(3): 2664-2676. |
| [3] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, et al. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain[J]. Netinfo Security, 2022, 22(6): 61-72. |
| 王姝爽, 马兆丰, 刘嘉微, 等. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. | |
| [4] | MA Zhaofeng, WANG Xiaochang, JAIN D K, et al. A Blockchain-Based Trusted Data Management Scheme in Edge Computing[J]. IEEE Transactions on Industrial Informatics, 2019, 16(3): 2013-2021. |
| [5] | JAROUCHEH Z, ÁLVAREZ I A. Secretation: Toward a Decentralised Identity and Verifiable Credentials Based Scalable and Decentralised Secret Management Solution[C]// IEEE. 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC). New York: IEEE, 2021: 1-9. |
| [6] | JÄRPEHULT O, ÅGREN F J, BÄCKSTRÖM M, et al. A Longitudinal Characterization of The Third-Party Authentication Landscape[C]// IEEE. 2022 IFIP Networking Conference (IFIP Networking). New York: IEEE, 2022: 1-9. |
| [7] | ALOM I, ESHITA R M, HARUN A I, et al. Dynamic Management of Identity Federations Using Blockchain[C]// IEEE. 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC). New York: IEEE, 2021: 1-9. |
| [8] | MANU S, DAVE L, DAVID C. Verifiable Credentials Data Model 1.0- Expressing Verifiable Information on the Web[EB/OL]. (2022-03-03)[2025-02-25]. https://www.w3.org/TR/vc-data-model/. |
| [9] | KORTESNIEMI Y, LAGUTIN D, ELO T, et al. Improving the Privacy of IoT with Decentralised Identifiers (DIDs)[EB/OL]. (2019-03-20)[2025-02-25]. https://onlinelibrary.wiley.com/doi/10.1155/2019/8706760. |
| [10] | FAN Xinxin, CHAI Qi, XU Lei, et al. Diam-Iot: A Decentralized Identity and Access Management Framework for Internet of Things[C]// ACM. Proceedings of the 2nd ACM International Symposium on Blockchain and Secure Critical Infrastructure. New York: ACM, 2020: 186-191. |
| [11] | ZHOU Tong, ZHAO He, LI Xiaofeng. EverSSDI: Blockchain-Based Framework for Verification, Authorisation and Recovery of Self-Sovereign Identity Using Smart Contracts[J]. International Journal of Computer Applications in Technology, 2019, 60(3): 281-295. |
| [12] | WANG Fennie, FILIPPI P D. Self-Sovereign Identity in a Globalized World: Credentials-Based Identity Systems as a Driver for Economic Inclusion[EB/OL]. (2020-01-23)[2025-02-25]. https://www.mendeley.com/catalogue/ead94f80-fd2a-3138-a848-9c4a2dd29aa9/. |
| [13] | LI Qinan, XUE Zhihao. A Privacy-Protecting Authorization System Based on Blockchain and Zk-SNARK[C]// ACM. The 2020 International Conference on Cyberspace Innovation of Advanced Technologies. New York: ACM, 2020: 439-444. |
| [14] | SI Bingru, XIAO Jiang, LIU Cunyang, et al. Survey on Blockchain Network[J]. Journal of Software, 2024, 35(2): 773-799. |
| 司冰茹, 肖江, 刘存扬, 等. 区块链网络综述[J]. 软件学报, 2024, 35(2):773-799. | |
| [15] | WANG Ze, LIN Jingqiang, CAI Quanwei, et al. Blockchain-Based Certificate Transparency and Revocation Transparency[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 681-697. |
| [16] | LUNDKVIST C, HECK R, TORSTENSSON J, et al. Uport: A Platform for Self-Sovereign Identity[EB/OL]. (2016-10-20)[2025-02-25]. https://www.blockchainlab.com/pdf/uPort_whitepaper_DRAFT20161020.pdf. |
| [17] | ZHU Xiaoqiang, LIU Jiqiang, LU Lingyun, et al. Enabling Intelligent Connectivity:A Survey of Secure ISAC in 6G Networks[EB/OL]. (2024-07-24)[2025-02-25]. https://resources.hutubox.com/user-file/cab15ae4255a1d7982bf5cc2b785e4ee.pdf. |
| [18] | HE Debiao, ZEADALLY S, KUMAR N, et al. Anonymous Authentication for Wireless Body Area Networks with Provable Security[J]. IEEE Systems Journal, 2016, 11(4): 2590-2601. |
| [19] | REN Jie, LI Meihong, DU Ye, et al. Identity-Based Authentication Key Agreement Protocol for Horizontal Federated Learning Environment[J]. Journal of Beijing University of Aeronautics and Astronautics, 2023, 49(2): 397-405. |
| 任杰, 黎妹红, 杜晔, 等. 横向联邦学习环境基于身份认证及密钥协商协议[J]. 北京航空航天大学学报, 2023, 49(2):397-405. | |
| [20] | KULJEET K, GARG S, GEORGES K, et al. A Lightweight and Privacy-Preserving Authentication Protocol for Mobile Edge Computing[C]// IEEE. Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [21] | TSOBDJOU L D, PIERRE S, QUINTERO A. A New Mutual Authentication and Key Agreement Protocol for Mobile Client-Server Environment[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1275-1286. |
| [22] | LIU Xin, YANG Haorui, GUO Zhenbin, et al. An Authentication Protocol Achieving Online Registrationand Privilege Separation for Industrial Internet of Things[J]. Netinfo Security, 2021, 21(7): 1-9. |
| 刘忻, 杨浩睿, 郭振斌, 等. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7):1-9. |
| [1] | 叶佳骏, 高翠凤, 薛吟兴. 基于静态分析的价格预言机操纵源代码检测方法研究[J]. 信息网络安全, 2025, 25(5): 732-746. |
| [2] | 秦金磊, 康毅敏, 李整. 智能电网中轻量级细粒度的多维多子集隐私保护数据聚合[J]. 信息网络安全, 2025, 25(5): 747-757. |
| [3] | 杨亚涛, 丁渝诚, 刘培鹤, 桑鹏. 基于区块链的隐私保护和数字认证研究[J]. 信息网络安全, 2025, 25(4): 640-653. |
| [4] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [5] | 李强, 沈援海, 王锦泽, 黄晏瑜, 孙建国. 一种面向工业物联网环境的离线—在线签名方案[J]. 信息网络安全, 2025, 25(3): 392-402. |
| [6] | 袁征, 张跃飞, 冯笑, 乔雅馨. 基于PUF的电力物联网智能终端认证协议[J]. 信息网络安全, 2025, 25(1): 13-26. |
| [7] | 王勇, 武一帆, 万前程. 基于中国剩余定理的可编辑区块链方案研究[J]. 信息网络安全, 2025, 25(1): 36-47. |
| [8] | 夏喆, 夏学志, 吕文杰, 张明武. 车联网中基于证书的局部可验证聚合签名方案[J]. 信息网络安全, 2025, 25(1): 48-62. |
| [9] | 段昊哲, 李志慧, 韦性佳, 胡珂欣. d维量子系统中无需纠缠的量子身份认证协议[J]. 信息网络安全, 2024, 24(9): 1364-1374. |
| [10] | 余礼苏, 李彪, 姚元志, 温家进, 黎子鹏, 王振. 区块链辅助无人机移动边缘计算系统的性能优化[J]. 信息网络安全, 2024, 24(9): 1432-1443. |
| [11] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [12] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [13] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [14] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [15] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||