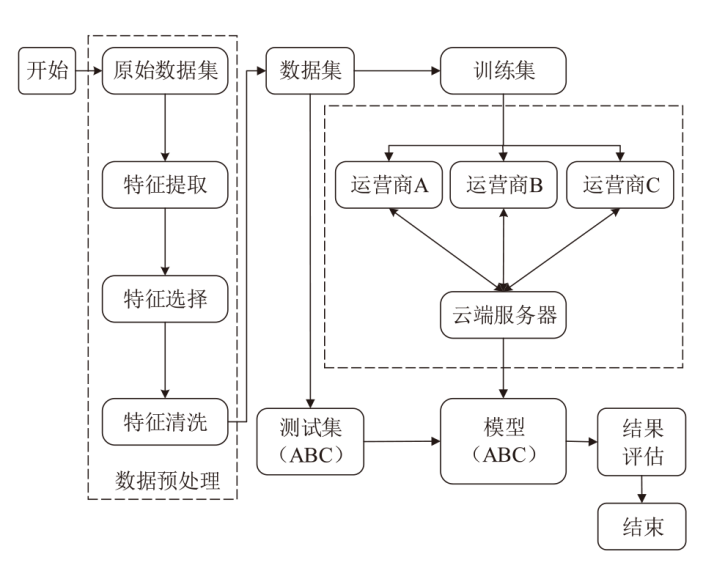
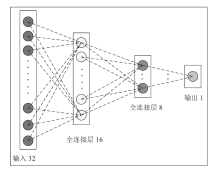
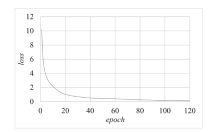
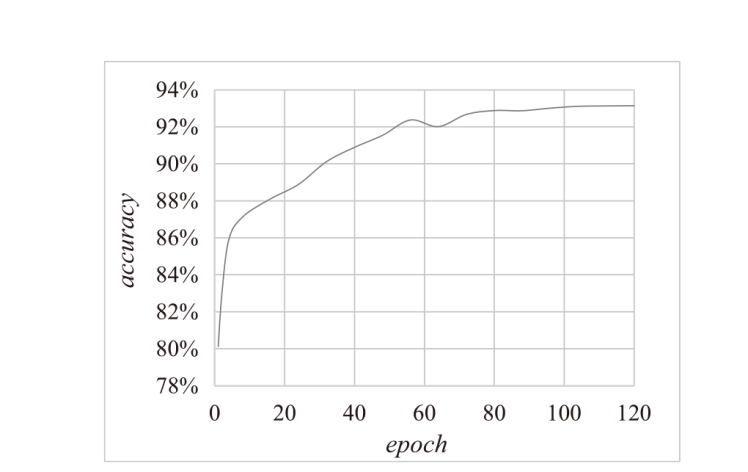
信息网络安全 ›› 2024, Vol. 24 ›› Issue (1): 60-68.doi: 10.3969/j.issn.1671-1122.2024.01.006
基于联邦学习的Tor流量检测算法设计与实现
赵佳1,2, 杨博凯1,2( ), 饶欣宇1,2, 郭雅婷1,2
), 饶欣宇1,2, 郭雅婷1,2
- 1.北京交通大学智能交通数据安全与隐私保护实验室,北京 100044
2.北京交通大学计算机与信息技术学院,北京 100044
-
收稿日期:2023-11-14出版日期:2024-01-10发布日期:2024-01-24 -
通讯作者:杨博凯 E-mail:23120488@bjtu.edu.cn -
作者简介:赵佳(1980—),女,内蒙古,副教授,博士,CCF会员,主要研究方向为密码学、隐私保护|杨博凯(2000—),男,黑龙江,硕士研究生,主要研究方向为联邦学习|饶欣宇(1999—),女,四川,硕士研究生,主要研究方向为联邦学习、密码学|郭雅婷(1998—),女,山东,硕士研究生,主要研究方向为联邦学习、密码学 -
基金资助:国家重点研发计划(2020YFB2103800)
Design and Implementation of Tor Traffic Detection Algorithm Based on Federated Learning
ZHAO Jia1,2, YANG Bokai1,2( ), RAO Xinyu1,2, GUO Yating1,2
), RAO Xinyu1,2, GUO Yating1,2
- 1. Intelligent Traffic Data Security and Privacy Protection Laboratory, Beijing Jiaotong University, Beijing 100044, China
2. School of Computer Science and Information Technology, Beijing Jiaotong University, Beijing 100044, China
-
Received:2023-11-14Online:2024-01-10Published:2024-01-24 -
Contact:YANG Bokai E-mail:23120488@bjtu.edu.cn
摘要:
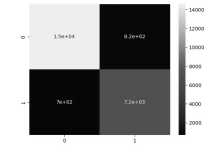
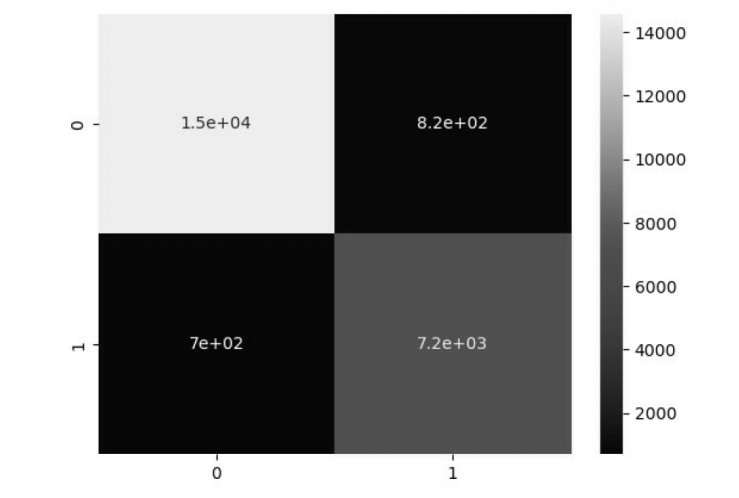
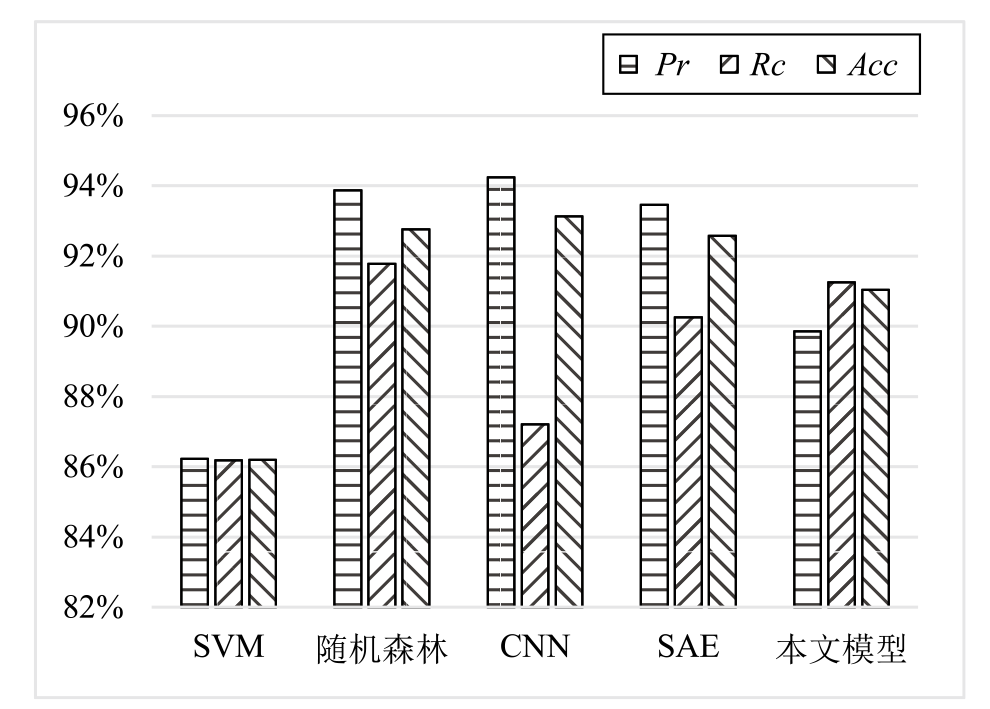
Tor网络作为第二代匿名互联网通信系统,常被网络罪犯用于进行网络攻击和欺诈等恶意活动,给网络安全带来了严重的威胁和挑战。为解决该问题,文章提出一种基于联邦学习的Tor流量检测方法。目前Tor流量检测以单主机检测为主,存在效率低和无法实现数据共享的问题,文章采用联邦学习技术和DP-SGD算法确保各参与方在保护用户隐私的前提下构建全局模型,解决数据孤岛问题。实验证明,该模型在保障用户数据隐私的同时,具有92%的整体准确率、90%的准确率和92%的召回率。文章通过对比实验进一步验证了模型在隐私保护和分类效果上的优越性。
中图分类号:
引用本文
赵佳, 杨博凯, 饶欣宇, 郭雅婷. 基于联邦学习的Tor流量检测算法设计与实现[J]. 信息网络安全, 2024, 24(1): 60-68.
ZHAO Jia, YANG Bokai, RAO Xinyu, GUO Yating. Design and Implementation of Tor Traffic Detection Algorithm Based on Federated Learning[J]. Netinfo Security, 2024, 24(1): 60-68.
| [1] |
CHEN Hexiong, LUO Yuwei, WEI Yunkai, et al. Collaborative Detection Technology of SDN Abnormal Traffic Based on Federated Learning[J]. Computer Engineering, 2023, 49(3): 168-176.
doi: 10.19678/j.issn.1000-3428.0064310 |
|
陈何雄, 罗宇薇, 韦云凯, 等. 基于联邦学习的SDN异常流量协同检测技术[J]. 计算机工程, 2023, 49(3):168-176.
doi: 10.19678/j.issn.1000-3428.0064310 |
|
| [2] | BASYONI L, FETAIS N, ERBAD A, et al. Traffic Analysis Attacks on Tor: A Survey[C]// IEEE. 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies(ICIoT). New York: IEEE, 2020: 183-188. |
| [3] |
LU Yunan, CAI Manchun, ZHAO Ce, et al. Tor Anonymous Traffic Identification Based on Parallelizing Dilated Convolutional Network[J]. Applied Sciences, 2023; 13(5): 3243.
doi: 10.3390/app13053243 URL |
| [4] | TAN Liuyan, RUAN Shuhua, YANG Min, et al. Educational Data Classification Based on Deep Learning[J]. Netinfo Security, 2023, 23(3): 96-102. |
| 谭柳燕, 阮树骅, 杨敏, 等. 基于深度学习的教育数据分类方法[J]. 信息网络安全, 2023, 23(3):96-102. | |
| [5] | MISHRA S. Network Traffic Analysis Using Machine Learning Techniques in IoT Networks[J]. International Journal of Software Innovation, 2022, 9(4): 1-17. |
| [6] |
REN Jiyuan, ZHANG Yunhou, WANG Zhe, et al. Artificial Intelligence-Based Network Traffic Analysis and Automatic Optimization Technology[J]. Mathematical Biosciences and Engineering: MBE, 2022, 19(2): 1775-1785.
doi: 10.3934/mbe.2022083 URL |
| [7] | JIA Lingyu, LIU Yang, WANG Bailing, et al. A Hierarchical Classification Approach for Tor Anonymous Traffic[C]// IEEE. 2017 IEEE 9th International Conference on Communication Software and Networks(ICCSN). New York: IEEE, 2017: 239-243. |
| [8] | LASHKARI A H, GIL G D, MAMUN M, et al. Characterization of Tor Traffic Using Time Based Features[EB/OL]. [2023-10-11]. https://www.researchgate.net/profile/Arash-Habibi-Lashkari/publication/314521450_Characterization_of_Tor_Traffic_using_Time_based_Features/links/59cd942da6fdcce3b34639cc/Characterization-of-Tor-Traffic-using-Time-based-Features.pdf. |
| [9] |
RAO Zhihong, NIU Weina, ZHANG Xiaosong, et al. Tor Anonymous Traffic Identification Based on Gravitational Clustering[J]. Peer-to-Peer Networking and Applications, 2018, 11: 592-601.
doi: 10.1007/s12083-017-0566-4 |
| [10] |
HE Gaofeng, YANG Ming, LUO Junzhou, et al. Online Identification of Tor Anonymous Communication Traffic[J]. Journal of Software, 2013, 24(3): 540-556.
doi: 10.3724/SP.J.1001.2013.04253 URL |
| 何高峰, 杨明, 罗军舟, 等. Tor匿名通信流量在线识别方法[J]. 软件学报, 2013, 4(3):540-556. | |
| [11] | WEI Songjie, LI Chenghao, SHEN Haotong, et al. Research and Application of Network Anonymous Traffic Detection Method Based on Deep Forest[J]. Netinfo Security, 2022, 22(8): 64-71. |
| 魏松杰, 李成豪, 沈浩桐, 等. 基于深度森林的网络匿名流量检测方法研究与应用[J]. 信息网络安全, 2022, 22(8):64-71. | |
| [12] | WANG Xirui, LU Tianliang, ZHANG Jianling, et al. Tor Anonymous Traffic Identification Method Based on Weighted Stacking Ensemble Learning[J]. Netinfo Security, 2021, 21(12): 118-125. |
| 王曦锐, 芦天亮, 张建岭, 等. 基于加权Stacking集成学习的Tor匿名流量识别方法[J]. 信息网络安全, 2021, 21(12):118-125. | |
| [13] | ZHANG Ling, WEI Chuanzheng, LIN Zhenbiao, et al. A Method for Identifying Tor Hosts Based on Machine Learning Techniques[J]. Application of Electronic Technique, 2021, 47(4): 54-58. |
| 张玲, 卫传征, 林臻彪, 等. 一种基于机器学习的Tor网络识别探测技术[J]. 电子技术应用, 2021, 47(4):54-58. | |
| [14] | PAN Yihan, ZHANG Aixin. Tor Traffic Identification Based on DeepLearning[J]. Communications Technology, 2019, 52(12): 2982-2986. |
| 潘逸涵, 张爱新. 基于深度学习的Tor流量识别方法[J]. 通信技术, 2019, 52(12):2982-2986. | |
| [15] |
VISHNUPRIYA A, SINGH H K, SIVACHAITANYAPRASAD M, et al. RNN-LSTM Based Deep Learning Model for Tor Traffic Classification[J]. Cyber-Physical Systems, 2021, 9: 25-42.
doi: 10.1080/23335777.2021.1924284 URL |
| [16] |
AL-NABKI M W, FIDALGO E, ALEGRE E, et al. ToRank: Identifying the Most Influential Suspicious Domains in the Tor Network[J]. Expert Systems with Applications, 2019, 123: 212-226.
doi: 10.1016/j.eswa.2019.01.029 URL |
| [17] | LI Xiaohua, WANG Suhang, LI Kai, et al. A Privacy-Preserving Analysis Model of Human-to-Human Transmission of Infectious Diseases[J]. Netinfo Security, 2023, 23(3): 35-44. |
| 李晓华, 王苏杭, 李凯, 等. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3):35-44. | |
| [18] |
HE Gaofeng, YANG Ming, LUO Junzhou, et al. A Novel Application Classification Attack Against Tor[J]. Concurrency and Computation: Practice and Experience, 2015, 27(18): 5640-5661.
doi: 10.1002/cpe.v27.18 URL |
| [19] |
SAMI Z. Tor Traffic Analysis Using Hidden Markov Models[J]. Security and Communication Networks, 2013, 6(9): 1075-1086.
doi: 10.1002/sec.v6.9 URL |
| [20] |
CHEN Yijin, SU Ye, ZHANG Mingyue, et al. FedTor: An Anonymous Framework of Federated Learning in Internet of Things[J]. IEEE Internet of Things Journal, 2022, 9: 18620-18631.
doi: 10.1109/JIOT.2022.3162826 URL |
| [21] | ABADI M, CHU A, GOODFELLOW I, et al. Deep Learning with Differential Privacy[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 308-318. |
| [22] | REZAEI S, LIU Xin. An Efficient Subpopulation-Based Membership Inference Attack[EB/OL]. [2023-10-15]. https://arxiv.org/pdf/2203.02080.pdf. |
| [23] | WANG Tengfei. Research on Tor Anonymous Traffic Recognition Technology[D]. Beijing: People’s Public Security University of China, 2022. |
| 王腾飞. Tor匿名流量识别技术研究[D]. 北京: 中国人民公安大学, 2022. | |
| [24] |
LOTFOLLAHI M, ZADE R S H, SIAVOSHANI M J, et al. Deep Packet: A Novel Approach For Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012.
doi: 10.1007/s00500-019-04030-2 |
| [1] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [2] | 徐茹枝, 戴理朋, 夏迪娅, 杨鑫. 基于联邦学习的中心化差分隐私保护算法研究[J]. 信息网络安全, 2024, 24(1): 69-79. |
| [3] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [4] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [5] | 陈晶, 彭长根, 谭伟杰, 许德权. 基于差分隐私和秘密共享的多服务器联邦学习方案[J]. 信息网络安全, 2023, 23(7): 98-110. |
| [6] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [7] | 刘吉强, 王雪微, 梁梦晴, 王健. 基于共享数据集和梯度补偿的分层联邦学习框架[J]. 信息网络安全, 2023, 23(12): 10-20. |
| [8] | 杨丽, 朱凌波, 于越明, 苗银宾. 联邦学习与攻防对抗综述[J]. 信息网络安全, 2023, 23(12): 69-90. |
| [9] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [10] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [11] | 吕国华, 胡学先, 杨明, 徐敏. 基于联邦随机森林的船舶AIS轨迹分类算法[J]. 信息网络安全, 2022, 22(4): 67-76. |
| [12] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [13] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [14] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [15] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||