信息网络安全 ›› 2023, Vol. 23 ›› Issue (9): 1-11.doi: 10.3969/j.issn.1671-1122.2023.09.001
• 等级保护 • 下一篇
基于双重图神经网络和自编码器的网络异常检测
- 东南大学网络空间安全学院,南京 211189
-
收稿日期:2023-06-05出版日期:2023-09-10发布日期:2023-09-18 -
通讯作者:秦中元 E-mail:zyqin@seu.edu.cn -
作者简介:秦中元(1974—),男,河南,副教授,博士,CCF会员,主要研究方向为智能终端安全、人工智能安全和无线网络安全|马楠(2000—),女,江苏,硕士研究生,主要研究方向为网络安全|余亚聪(1997—),男,浙江,硕士研究生,主要研究方向为可信计算、密码学|陈立全(1976—),男,广西,教授,博士,CCF会员,主要研究方向为移动信息安全、物联网系统与安全、云计算和大数据安全 -
基金资助:国家重点研发计划(2020YFE0200600)
Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders
QIN Zhongyuan( ), MA Nan, YU Yacong, CHEN Liquan
), MA Nan, YU Yacong, CHEN Liquan
- School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
-
Received:2023-06-05Online:2023-09-10Published:2023-09-18 -
Contact:QIN Zhongyuan E-mail:zyqin@seu.edu.cn
摘要:
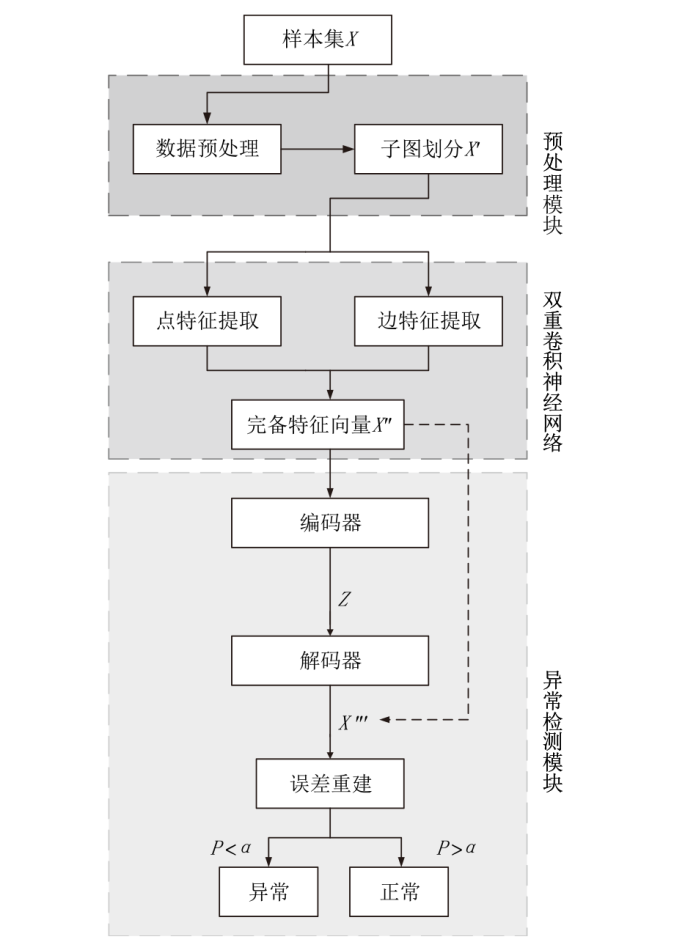
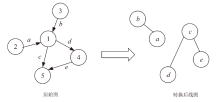
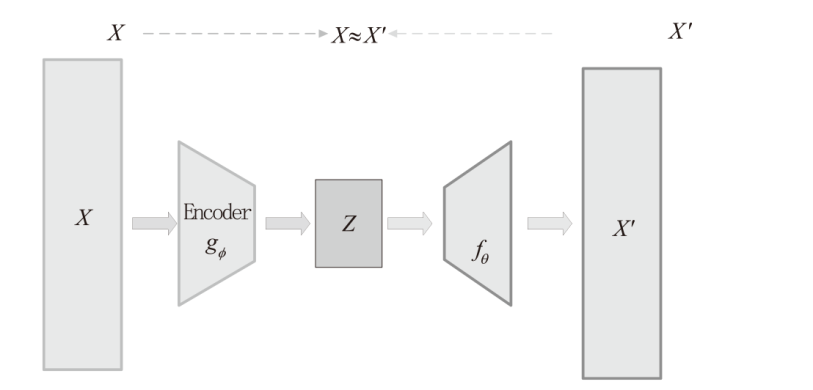
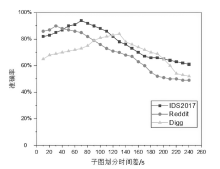
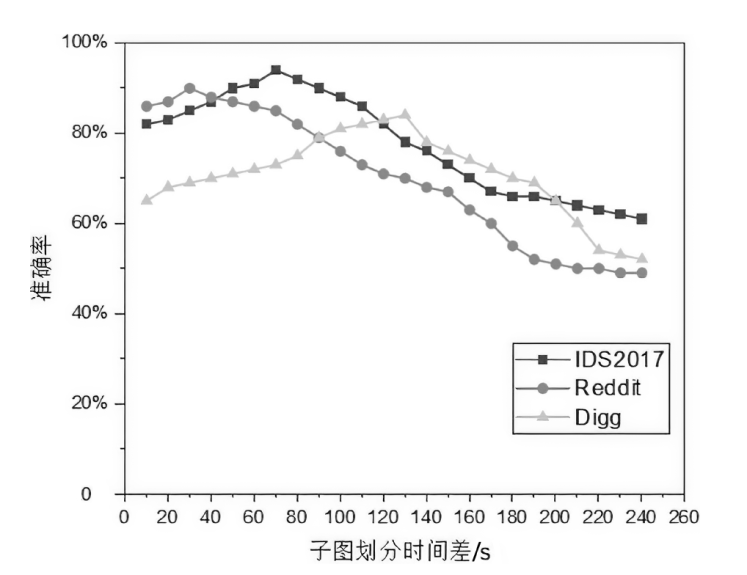
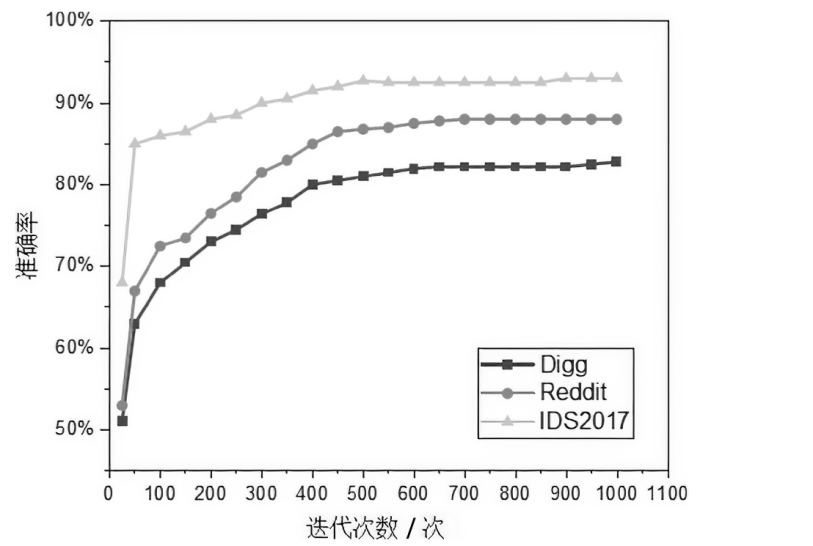
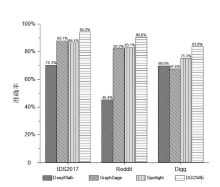
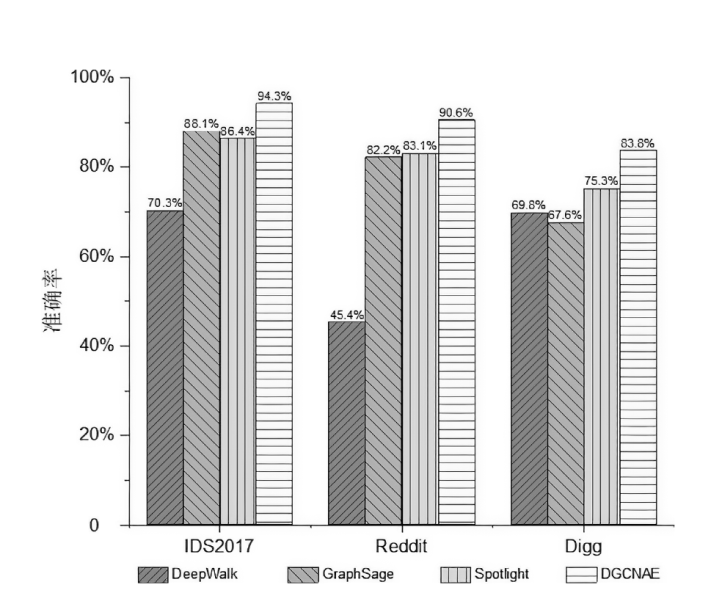
图神经网络在网络异常检测领域中的应用大多集中于单点特征的提取,忽略了连续流量之间的关联性的特点,文章提出了一种基于双重图神经网络和自编码器的网络异常检测方法DGCNAE。该方法首先对通信数据进行图构建和子图划分,然后将子图送入两层图卷积神经网络,分别对点和边进行特征提取,最后采用无监督学习方法对划分出的子图进行训练。通过对子图划分时间间隔和迭代次数进行迭代实验,得出效果最佳的子图划分时间间隔和迭代次数,并在3个典型数据集上与已有算法进行对比实验,实验结果表明,该方法具有更高的准确率和泛化能力。
中图分类号:
引用本文
秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11.
QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders[J]. Netinfo Security, 2023, 23(9): 1-11.
| [1] | YOST J R. The March of IDES: Early History of Intrusion-Detection Expert Systems[J]. IEEE Annals of the History of Computing, 2016, 38(4): 42-54. |
| [2] | JAMES G, WITTEN D, HASTIE T, et al. An Introduction to Statistical Learning: With Applications in R[M]. New York: Springer, 2021. |
| [3] |
THAKKAR A, LOHIYA R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges[J]. Archives of Computational Methods in Engineering, 2021, 28(4): 3211-3243.
doi: 10.1007/s11831-020-09496-0 |
| [4] |
VINAYAKUMAR R, ALAZAB M, SOMAN K P, et al. Deep Learning Approach for Intelligent Intrusion Detection System[J]. IEEE Access, 2019, 7: 41525-41550.
doi: 10.1109/ACCESS.2019.2895334 |
| [5] | ESWARAN D, FALOUTSOS C. SedanSpot: Detecting Anomalies in Edge Streams[C]// IEEE. 2018 IEEE International Conference on Data Mining (ICDM). New York: IEEE, 2018: 953-958. |
| [6] | ZHU Huidi, LU Jialiang. Graph-Based Intrusion Detection System Using General Behavior Learning[C]// IEEE. GLOBECOM 2022-2022 IEEE Global Communications Conference. New York: IEEE, 2022: 2621-2626. |
| [7] | YAO Yepeng, SU Liya, LU Zhigang. DeepGFL: Deep Feature Learning via Graph for Attack Detection on Flow-Based Network Traffic[C]// IEEE. MILCOM 2018-2018 IEEE Military Communications Conference (MILCOM). New York: IEEE, 2018: 579-584. |
| [8] |
FANG Yong, WANG Congshuang, FANG Zhiyang, et al. LMTracker: Lateral Movement Path Detection Based on Heterogeneous Graph Embedding[J]. Neurocomputing, 2022, 474: 37-47.
doi: 10.1016/j.neucom.2021.12.026 URL |
| [9] |
WU Zonghua, PAN Shirui, CHEN Fengwen, et al. A Comprehensive Survey on Graph Neural Networks[J]. IEEE Transactions on Neural Networks and Learning Systems, 2020, 32(1): 4-24.
doi: 10.1109/TNNLS.5962385 URL |
| [10] | CAVILLE E, LO W W, LAYEGHY S, et al. Anomal-E: A Self-Supervised Network Intrusion Detection System Based on Graph Neural Networks[J]. Knowledge-Based Systems, 2022, 258: 1-12. |
| [11] | KIPF T N, WELLING M. Semi-Supervised Classification with Graph Convolutional Networks[EB/OL]. (2016-09-09)[2023-05-13]. https://arxiv.org/abs/1609.02907. |
| [12] | LIU Jie, LI Xiwang. Anomaly Detection Algorithm in Industrial Control Network Based on Graph Neural Network[J]. Computer Systems & Applications, 2020, 29(12): 234-238. |
| 刘杰, 李喜旺. 基于图神经网络的工控网络异常检测算法[J]. 计算机系统应用, 2020, 29(12): 234-238. | |
| [13] |
TANG Qiuhang, CHEN Huadong, GE Binbin, et al. AIGCN: Attack Intention Detection for Power System Using Graph Convolutional Networks[J]. Journal of Signal Processing Systems, 2022, 94(11): 1119-1127.
doi: 10.1007/s11265-021-01724-5 |
| [14] | POURHABIBI T, ONG K L, KAM B, et al. Fraud Detection: A Systematic Literature Review of Graph-Based Anomaly Detection Approaches[J]. Decision Support Systems, 2020, 133: 1-15. |
| [15] |
KIM H, LEE B S, SHIN W Y, et al. Graph Anomaly Detection with Graph Neural Networks: Current Status and Challenges[J]. IEEE Access, 2022, 10: 111820-111829.
doi: 10.1109/ACCESS.2022.3211306 URL |
| [16] |
DING Qingfeng, LI Jinguo. A Distributed Abnormal Traffic Detection Scheme in the Internet of Things Environment[J]. Computer Engineering, 2022, 48(8): 152-159.
doi: 10.19678/j.issn.1000-3428.0063284 |
|
丁庆丰, 李晋国. 一种物联网环境下的分布式异常流量检测方案[J]. 计算机工程, 2022, 48(8): 152-159.
doi: 10.19678/j.issn.1000-3428.0063284 |
|
| [17] | ZOLA F, SEGUROLA-GIL L, BRUSE J L, et al. Network Traffic Analysis through Node Behaviour Classification: A Graph-Based Approach with Temporal Dissection and Data-Level Preprocessing[J]. Computers & Security, 2022, 115: 1-17. |
| [18] | LO W W, LAYEGHY S, SARHAN M. E-GraphSAGE: A Graph Neural Network Based Intrusion Detection System for IoT[C]// IEEE/IFIP. 2022 IEEE/IFIP Network Operations and Management Symposium (NOMS 2022). New York: IEEE, 2022: 1-9. |
| [19] | LIU Jinpeng. Network Security Protection Based on Machine Learning Technology[J]. Cybersecurity, 2018, 9(9): 96-102. |
| 刘金鹏. 基于机器学习技术的网络安全防护[J]. 网络空间安全, 2018, 9(9): 96-102. | |
| [20] |
EDDAHMANI I, PHAM C H, NAPOLEON T, et al. Unsupervised Learning of Disentangled Representation via Auto-Encoding: A Survey[J]. Sensors, 2023, 23(4): 1-19.
doi: 10.3390/s23010001 URL |
| [21] | SAKURADA M, YAIRI T. Anomaly Detection Using Autoencoders with Nonlinear Dimensionality Reduction[C]// MLSDA. Proceedings of the MLSDA 2014 2nd Workshop on Machine Learning for Sensory Data Analysis. New York: ACM, 2014: 4-11. |
| [22] | NOBLE C C, COOK D J. Graph-Based Anomaly Detection[C]// ACM SIGKDD. The Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2003: 631-636. |
| [23] | PEROZZI B, AL-RFOU R, SKIENA S. DeepWalk: Online Learning of Social Representations[C]// ACM SIGKDD. The 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2014: 701-710. |
| [24] | HAMILTON W, YING R, LESKOVEC J, et al. Inductive Representation Learning on Large Graphs[J]. Neural Information Processing Systems, 2017, 1(2): 1024-1034. |
| [25] | ESWARAN D, FALOUTSIS C, GUHA S, et al. SpotLight: Detecting Anomalies in Streaming Graphs[C]// ACM SIGKDD. KDD '18: Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining. New York: ACM, 2018: 1378-1386. |
| [1] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [2] | 施园, 李杨, 詹孟奇. 一种面向微服务的多维度根因定位算法[J]. 信息网络安全, 2023, 23(3): 73-83. |
| [3] | 顾兆军, 刘婷婷, 高冰, 隋翯. 基于GAN-Cross的工控系统类不平衡数据异常检测[J]. 信息网络安全, 2022, 22(8): 81-89. |
| [4] | 周婧怡, 李红娇. 针对PMU测量的虚假数据注入攻击检测方法[J]. 信息网络安全, 2022, 22(5): 75-83. |
| [5] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [6] | 徐茹枝, 吕畅冉, 龙燕, 刘远彬. 工业控制系统高隐蔽性数据攻击防御方法研究[J]. 信息网络安全, 2022, 22(12): 34-46. |
| [7] | 郭森森, 王同力, 慕德俊. 基于生成对抗网络与自编码器的网络流量异常检测模型[J]. 信息网络安全, 2022, 22(12): 7-15. |
| [8] | 牛艺诺, 张逸飞, 高能, 马存庆. 融合时序和逻辑关系的日志异常检测系统设计[J]. 信息网络安全, 2022, 22(11): 1-6. |
| [9] | 仝鑫, 金波, 王靖亚, 杨莹. 一种面向Android恶意软件的多视角多任务学习检测方法[J]. 信息网络安全, 2022, 22(10): 1-7. |
| [10] | 朱丽娜, 马铭芮, 朱东昭. 基于图神经网络和通用漏洞分析框架的C类语言漏洞检测方法[J]. 信息网络安全, 2022, 22(10): 59-68. |
| [11] | 蒋首志, 曹金璇, 殷浩展, 芦天亮. 基于MHA与SDAE的Tor网站指纹识别模型[J]. 信息网络安全, 2022, 22(10): 8-14. |
| [12] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [13] | 秦中元, 胡宁, 方兰婷. 基于免疫仿生机理和图神经网络的网络异常检测方法[J]. 信息网络安全, 2021, 21(8): 10-16. |
| [14] | 徐洪平, 马泽文, 易航, 张龙飞. 基于卷积循环神经网络的网络流量异常检测技术[J]. 信息网络安全, 2021, 21(7): 54-62. |
| [15] | 吴驰, 帅俊岚, 龙涛, 于俊清. 基于Linux Shell命令的用户异常操作检测方法研究[J]. 信息网络安全, 2021, 21(5): 31-38. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||