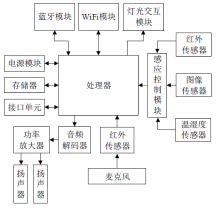
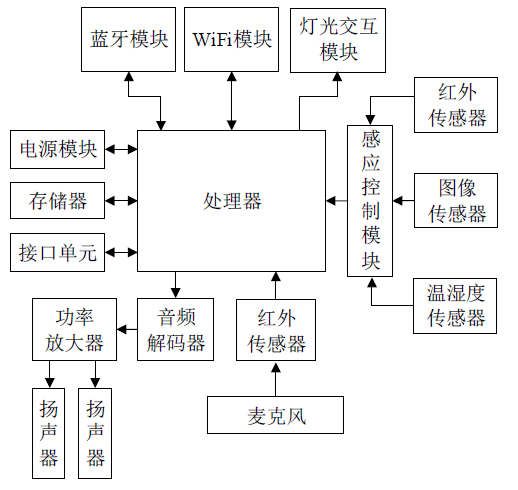
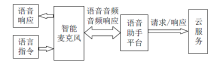
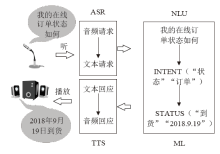
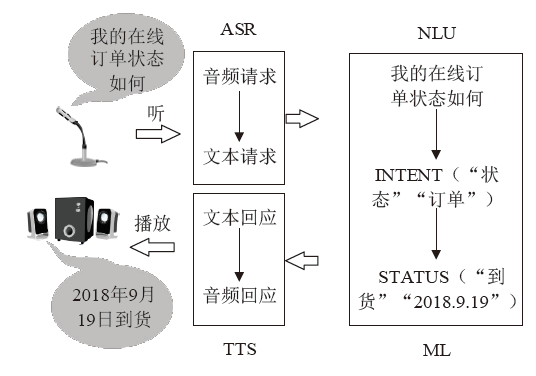
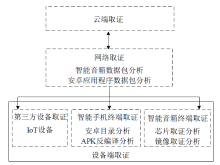
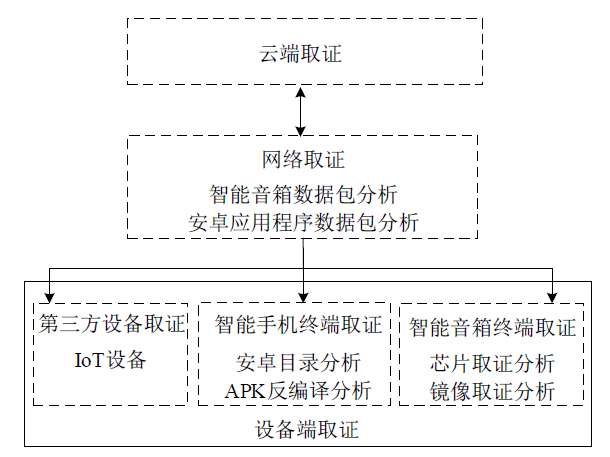
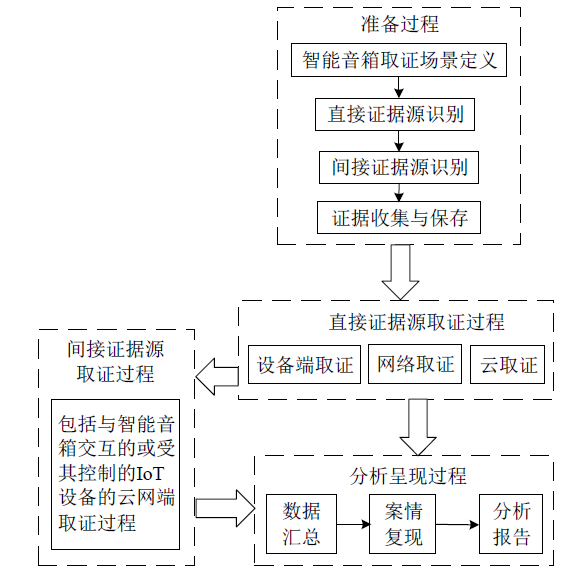
| [1] |
NOVAKOVIC J. Speaker Identification in Smart Environments with Multilayer Perceptron[C]// IEEE. The 19thTelecommunications Forum Proceedings of Papers(TELFOR). New York: IEEE, 2011: 1418-1421.
|
| [2] |
TSAI W, LIN J, MA C, et al. Speaker Identification for Personalized Smart TVs[C]// IEEE. International Conference on Consumer Electronics. New York: IEEE, 2016: 1-2.
|
| [3] |
BISIO I, GARIBOTTO C, SCIARRONE A, et al. Performance Analysis of Smart Audio Pre-Processing for Noise-Robust Text-Independent Speaker Recognition[C]// IEEE. Global Conference on Signal and Information Processing(GlobalSIP). New York: IEEE, 2017: 848-852.
|
| [4] |
BISIO I, GARIBOTTO C, GRATTAROLA A, et al. Smart and Robust Speaker Recognition for Context-Aware in-Vehicle Applications[J]. IEEE Transactions on Vehicular Technology, 2018, 67(9): 8808-8821.
|
| [5] |
CHO K, ROH J, HAN Y, et al. Real-Time Speaker Recognition System Using Multi-Stream I-Vectors for AI Assistant[C]// IEEE. International Conference on Consumer Electronics(ICCE). New York: IEEE, 2018: 1-4.
|
| [6] |
OUAMOUR S, SAYOUD H. Automatic Speaker Localization Based on Speaker Identification-a Smart Room Application[C]// IEEE. International Conference on Information and Communication Technology and Accessibility(ICTA). New York: IEEE, 2013: 1-5.
|
| [7] |
DAI Ximing, LOU Wenzhong, LIU Peng, et al. Speaker Tracking Based on Microphone Cross Arry in the Smart Conference System[C]// IEEE. International Conference on Consumer Electronics. New York: IEEE, 2014: 1-4.
|
| [8] |
MUN S, SHON S, KIM W, et al. Robust Speaker Direction Estimation with Microphone Array Using NMF for Smart TV Interaction[C]// IEEE. International Conference on Consumer Electronics(ICCE). New York: IEEE, 2015: 112-113.
|
| [9] |
RAHAMAN A, KIM B. AI Speaker: A Scope of Utilizing Sub-Wavelength Directional Sensing of Bio-Inspired MEMS Directional Microphone[C]// IEEE. 2020 IEEE SENSORS. New York: IEEE, 2020: 1-4.
|
| [10] |
WANG Mingshan, SIRLAPU A, KWASNIEWWSKA A, et al. Speaker Recognition Using Convolutional Neural Network with Minimal Training Data for Smart Home Solutions[C]// IEEE. The 11th International Conference on Human System Interaction(HSI). New York: IEEE, 2018: 139-145.
|
| [11] |
PARK C, CHOI J, SUNG E, et al. Are You Hearing or Listening? The Effect of Task Performance in Verbal Behavior with Smart Speaker[C]// IEEE. International Conference on Intelligent Robots and Systems(IROS). New York: IEEE, 2019: 319-324.
|
| [12] |
KALMAR G. Smart Speaker: Suspicious Event Detection with Reverse Mode Speakers[C]// IEEE. The 42nd International Conference on Telecommunications and Signal Processing(TSP). New York: IEEE, 2019: 509-512.
|
| [13] |
FURUTA R, OCHIAI H, ESAKI H. Mitigating Privacy Leak by Injecting Unique Noise into the Traffic of Smart Speakers[C]// IEEE. International Conference on Smart Computing(SMARTCOMP). New York: IEEE, 2020: 452-457.
|
| [14] |
MADDALI V, LOONEY D, PATIL K. Detection of Calls From Smart Speaker Devices[C]// IEEE. The 25th International Conference on Pattern Recognition(ICPR). New York: IEEE, 2020: 10616-10621.
|
| [15] |
MUN H, LEE Y. Accelerating Smart Speaker Service with Content Prefetching and Local Control[C]// IEEE. The 17th Annual Consumer Communications & Networking Conference(CCNC). New York: IEEE, 2020: 1-6.
|
 ), NI Xueli1,4, MA Zhuo1,4
), NI Xueli1,4, MA Zhuo1,4