信息网络安全 ›› 2022, Vol. 22 ›› Issue (7): 27-36.doi: 10.3969/j.issn.1671-1122.2022.07.004
基于智能合约的日志安全存储与公平访问方法
- 北京交通大学智能交通数据安全与隐私保护技术北京市重点实验室,北京 100044
-
收稿日期:2022-03-21出版日期:2022-07-10发布日期:2022-08-17 -
通讯作者:黄俊 E-mail:junhuang1996@bjtu.edu.cn -
作者简介:王健(1976—),男,山东,副教授,博士,主要研究方向为网络与信息安全|黄俊(1996—),男,安徽,硕士研究生,主要研究方向为区块链与智能合约 -
基金资助:国家重点研发计划(2020YFB2103800);山东省重大科技创新工程(2019JZZY020128)
Smart Contract-Based Log Secure Storage and Fair Access Method
- Beijing Key Laboratory of Security and Privacy in Intelligent Transportation, Beijing Jiaotong University, Beijing 100044, China
-
Received:2022-03-21Online:2022-07-10Published:2022-08-17 -
Contact:HUANG Jun E-mail:junhuang1996@bjtu.edu.cn
摘要:
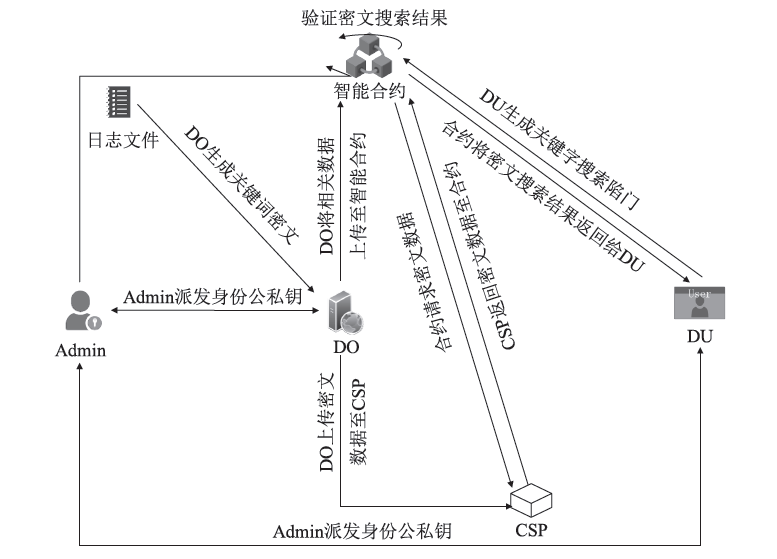
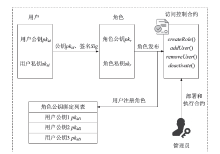
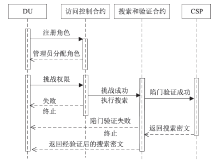
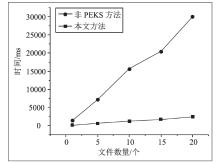
当前信息系统存在日志数据易被篡改、伪造和删除的安全风险及未授权访问等问题。现有日志存储与访问研究方法大多利用可搜索加密技术实现,虽然实现了敏感日志数据的加密存储,但缺乏对密文搜索过程的公平性和密文数据访问权限控制等问题的研究。针对以上问题,文章设计了一种基于智能合约的日志安全存储与公平访问方法。智能合约作为可搜索加密过程的参与方,执行搜索陷门的对比和密文搜索结果的验证,从而无需第三方实体即可验证密文搜索过程的正确性,同时利用押金机制保障搜索过程中数据使用者与云服务器之间的公平支付。该方法将基于角色的访问控制策略嵌入可搜索加密过程,通过角色公钥与实体身份公钥的一对多映射,将可搜索加密扩展至多对多模式,同时实现了日志密文数据的授权访问。安全性分析和实验表明,该方法可以满足日志数据存储的完整性和机密性要求,通过智能合约和押金机制保证密文搜索过程的公平性与正确性,通过基于角色的访问控制避免数据的未授权访问。
中图分类号:
引用本文
王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36.
WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method[J]. Netinfo Security, 2022, 22(7): 27-36.
表1
符号说明表
| 符号 | 含义 |
|---|---|
| | 日志明文数据 |
| | 解密后的日志明文数据 |
| | 公共密钥参数 |
| | DOs的角色公私密钥对 |
| | DUs的角色公私密钥对 |
| | DO的身份公私密钥对 |
| | DU的身份公私密钥对 |
| | 加密文件的对称密钥 |
| | 对日志数据file加密后的密文 |
| | 查询到的密文数据 |
| | CSP中密文存储的索引位置 |
| | 密文文件索引 |
| | 关键词集合 |
| | 感兴趣的关键词集合 |
| | 关键词密文 |
| | 日志文件签名 |
| [1] | LIAO Xiangke, LI Shanshan, DONG Wei, et al. Survey on Log Research of Large Scale Software System[J]. Journal of Software, 2016, 27(8): 1934-1947. |
| 廖湘科, 李姗姗, 董威, 等. 大规模软件系统日志研究综述[J]. 软件学报, 2016, 27(8):1934-1947. | |
| [2] |
WANG Cong, REN Kui, LOU Wenjing, et al. Toward Publicly Auditable Secure Cloud Data Storage Services[J]. IEEE Network, 2010, 24(4): 19-24.
doi: 10.1109/MNET.2010.5510914 URL |
| [3] | DO H G, NG W K. Blockchain-Based System for Secure Data Storage with Private Keyword Search[C]// IEEE. 2017 IEEE World Congress on Services(SERVICES). New York: IEEE, 2017: 90-93. |
| [4] | POURMAJIDI W, MIRANSKYY A. Logchain: Blockchain-Assisted Log Storage[C]// IEEE. IEEE 11th International Conference on Cloud Computing(CLOUD). New York: IEEE, 2018: 978-982. |
| [5] | LV Jianfu, LAI Yingxu, LIU Jing. Log Security Storage and Retrieval Based on Combination of on-Chain and off-Chain[J]. Computer Science, 2020, 47(3): 298-303. |
| 吕建富, 赖英旭, 刘静. 基于链上链下相结合的日志安全存储与检索[J]. 计算机科学, 2020, 47(3):298-303. | |
| [6] | BONEH D, CRESCENZO G D, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2004: 506-522. |
| [7] | LI Huige, TIAN Haibo, ZHANG Fangguo, et al. Blockchain-Based Searchable Symmetric Encryption Scheme[J]. Computers & Electrical Engineering, 2019, 73: 32-45. |
| [8] | DU Ruizhong, TAN Ailun, TIAN Junfeng. Public Key Searchable Encryption Scheme Based on Blockchain[J]. Journal on Communications, 2020, 41(4): 114-122. |
| 杜瑞忠, 谭艾伦, 田俊峰. 基于区块链的公钥可搜索加密方案[J]. 通信学报, 2020, 41(4): 114-122. | |
| [9] |
CHEN Lanxiang, LEE W K, CHANG C C, et al. Blockchain Based Searchable Encryption for Electronic Health Record Sharing[J]. Future Generation Computer Systems, 2019, 95: 420-429.
doi: 10.1016/j.future.2019.01.018 URL |
| [10] | AZARIA A, EKBLAW A, VIEIRA T, et al. Medrec: Using Blockchain for Medical Data Access and Permission Management[C]// IEEE. 2nd International Conference on Open and Big Data(OBD). New York:IEEE, 2016: 25-30. |
| [11] | FERRAIOLO D, CUGINI J, KUHN D R. Role-Based Access Control(RBAC): Features and Motivations[EB/OL]. [2021-12-11]. https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=916537. |
| [12] | DING Yi, JIN Jun, ZHANG Jinglun, et al. SC-RBAC: A Smart Contract Based RBAC Model for DApps[C]// Springer. International Conference on Human Centered Computing. Heidelberg: Springer, 2019: 75-85. |
| [13] |
ZHANG Liang, ZHANG Hanlin, YU Jia, et al. Blockchain-Based Two-Party Fair Contract Signing Scheme[J]. Information Sciences, 2020, 535(11): 142-155.
doi: 10.1016/j.ins.2020.05.054 URL |
| [14] |
YANG Yang, LIN Hongrui, LIU Ximeng, et al. Blockchain-Based Verifiable Multi-Keyword Ranked Search on Encrypted Cloud with Fair Payment[J]. IEEE Access, 2019, 7: 140818-140832.
doi: 10.1109/ACCESS.2019.2943356 |
| [15] | YAN Xixi, YUAN Xiaohan, TANG Yongli, et al. Verifiable Attribute-Based Searchable Encryption Scheme Based on Blockchain[J]. Journal on Communications, 2020, 41(2): 187-198. |
| 闫玺玺, 原笑含, 汤永利, 等. 基于区块链且支持验证的属性基搜索加密方案[J]. 通信学报, 2020, 41(2):187-198. |
| [1] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [2] | 郭宝霞, 王佳慧, 马利民, 张伟. 基于零信任的敏感数据动态访问控制模型研究[J]. 信息网络安全, 2022, 22(6): 86-93. |
| [3] | 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. |
| [4] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [5] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [6] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [7] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [8] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| [9] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| [10] | 涂国庆, 杨延浩, 刘树波. Geohash编码抗k近邻攻击的脆弱性分析[J]. 信息网络安全, 2021, 21(2): 10-15. |
| [11] | 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2): 34-44. |
| [12] | 张淑清, 蔡志文. 云数据下基于可问责属性即可撤销的加密方案[J]. 信息网络安全, 2021, 21(12): 70-77. |
| [13] | 王健, 于航, 韩臻, 韩磊. 基于智能合约的云存储共享数据访问控制方法[J]. 信息网络安全, 2021, 21(11): 40-47. |
| [14] | 于克辰, 郭莉, 姚萌萌. 基于区块链的高价值数据共享系统设计[J]. 信息网络安全, 2021, 21(11): 75-84. |
| [15] | 魏占祯, 彭星源, 赵洪. SDN中基于用户信任度的资源访问控制方案[J]. 信息网络安全, 2021, 21(10): 33-40. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||