信息网络安全 ›› 2022, Vol. 22 ›› Issue (7): 37-45.doi: 10.3969/j.issn.1671-1122.2022.07.005
一种基于机密计算的联邦学习节点轻量级身份认证协议
- 兰州大学信息科学与工程学院,兰州 730000
-
收稿日期:2022-04-10出版日期:2022-07-10发布日期:2022-08-17 -
通讯作者:刘忻 E-mail:xinl@lzu.edu.cn -
作者简介:刘忻(1988—),男,甘肃,讲师,博士,主要研究方向为认证协议、零信任体系架构、机密计算等|李韵宜(2001—),女,安徽,本科,主要研究方向为联邦学习、工业物联网身份认证协议、机密计算等|王淼(1997—),男,甘肃,硕士研究生,主要研究方向为车联网安全、区块链等 -
基金资助:国家自然科学基金重点项目(62132007);中央高校基本科研业务费专项资金(lzujbky-2020-6);甘肃省科技计划项目(20YF3FA024);兰州市科技计划项目(2019-4-47)
A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes
LIU Xin( ), LI Yunyi, WANG Miao
), LI Yunyi, WANG Miao
- School of Information Science & Engineering, Lanzhou University, Lanzhou 730000, China
-
Received:2022-04-10Online:2022-07-10Published:2022-08-17 -
Contact:LIU Xin E-mail:xinl@lzu.edu.cn
摘要:
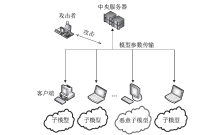
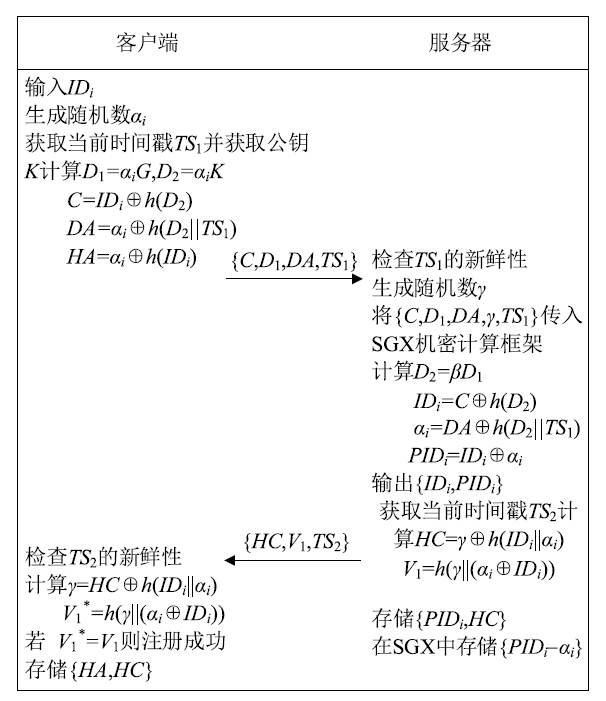
联邦学习框架在保护用户隐私数据安全的同时,满足模型对海量训练数据的需求,被广泛应用于车联网、智慧医疗、金融等领域。然而,参与联邦学习框架的客户端身份复杂,客户端与中央服务器在开放的信道上传递模型参数,给联邦学习框架带来了安全隐患。因此,如何高效准确地识别各参与节点的身份合法性对联邦学习框架十分重要。文章首先结合联邦学习实际需求提出一种基于机密计算的联邦学习节点轻量级身份认证协议,实现了客户端在线注册及数字签名功能。然后在服务器端采用SGX机密计算环境对密钥等关键参数进行保护。最后,文章通过AVISPA仿真工具和非形式化证明方法证明了协议的安全性,并将该协议与近年提出的其他身份认证协议在计算开销、通信开销和存储开销方面进行对比分析,结果表明,该协议具有更好的实用性与先进性。
中图分类号:
引用本文
刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45.
LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes[J]. Netinfo Security, 2022, 22(7): 37-45.
表4
计算开销对比
| 协议 | 客户端开销 | 服务器端开销 | 总开销/ms |
|---|---|---|---|
| 文献[ | | | 1153.75 |
| 文献[ | | | 1500.31 |
| 文献[ | | | 1247.18 |
| 本文协议 | | | |
| [1] | HE Wei. Overview of China’s Digital Economy Development[J]. Information and Communications Technology and Policy, 2021(2): 1-7. |
| 何伟. 我国数字经济发展综述[J]. 信息通信技术与政策, 2021(2):1-7. | |
| [2] | LI Li, FAN Yuxi, TSE M, et al. A Review of Applications in Federated Learning[EB/OL]. (2020-12-07)[2022-03-04]. http://dx.doi.org/10.1016/j.cie.2020.106854. |
| [3] | LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60. |
| [4] | ZHU Jianming, ZHANG Qinnan, GAO Sheng, et al. Privacy Preserving and Trustworthy Federated Learning Model Based on Blockchain[J]. Chinese Journal of Computers, 2021, 44(12): 2464-2484. |
| 朱建明, 张沁楠, 高胜, 等. 基于区块链的隐私保护可信联邦学习模型[J]. 计算机学报, 2021, 44(12):2464-2484. | |
| [5] | WANG Kunqing, LIU Jing, LI Chen, et al. A Survey on Threats to Federated Learning[J]. Journal of Information Security Research, 2022, 8(3): 223-234. |
| [6] | WU Jianhan, SI Shijing, WANG Jianzong, et al. Threats and Defenses of Federated Learning: A Survey[EB/OL]. (2022-02-17)[2022-03-04]. http://kns.cnki.net/kcms/detail/10.1321.G2.20220216.1702.010.html. |
| 吴建汉, 司世景, 王健宗, 等. 联邦学习攻击与防御综述[EB/OL]. (2022-02-17)[2022-03-04]. http://kns.cnki.net/kcms/detail/10.1321.G2.20220216.1702.010.html. | |
| [7] | SYVERSON P, CERVESATO I. The Logic of Authentication Protocols[C]// Springer. International School on Foundations of Security Analysis and Design. Heidelberg: Springer, 2000: 63-137. |
| [8] | LARA E, AGUILAR L, SANCHEZ M A, et al. Lightweight Authentication Protocol for M2M Communications of Resource-Constrained Devices in Industrial Internet of Things[EB/OL]. (2020-03-27)[2022-03-04]. https://doi.org/10.3390/s20020501. |
| [9] |
YU S, LEE J, PARK K, et al. IoV-SMAP: Secure and Efficient Message Authentication Protocol for IoV in Smart City Environment[J]. IEEE Access, 2020, 8: 167875-167886.
doi: 10.1109/ACCESS.2020.3022778 URL |
| [10] |
AGHILI S F, MALA H, KALIYAR P, et al. SecLAP: Secure and Lightweight RFID Authentication Protocol for Medical IoT[J]. Future Generation Computer Systems, 2019, 101: 621-634.
doi: 10.1016/j.future.2019.07.004 URL |
| [11] | DEEP G, MOHANA R, NAYYAR A, et al. Authentication Protocol for Cloud Databases Using Blockchain Mechanism[EB/OL]. (2019-12-06)[2022-03-04]. https://doi.org/10.3390/s19204444. |
| [12] | REN Jie, LI Meihong, DU Ye, et al. Lightweight Identity-Based Authentication Key Agreement Protocol for Horizontal Federated Learning Environment[EB/OL]. (2021-07-30)[2022-03-04]. https://kns.cnki.net/kcms/detail/detail.aspx?FileName=BJHK20210729006&DbName=CAPJ2021. |
| 任杰, 黎妹红, 杜晔, 等. 横向联邦学习环境基于身份轻量级认证密钥协商协议[EB/OL]. (2021-07-30)[2022-03-04]. https://kns.cnki.net/kcms/detail/detail.aspx?FileName=BJHK20210729006&DbName=CAPJ2021. | |
| [13] |
ZHAO Pengcheng, HUANG Yuanhao, GAO Jianping, et al. Federated Learning-Based Collaborative Authentication Protocol for Shared Data in Social IoV[J]. IEEE Sensors Journal, 2022, 22(7): 7385-7398.
doi: 10.1109/JSEN.2022.3153338 URL |
| [14] | DRUCKER N, GUERON S. Combining Homomorphic Encryption with Trusted Execution Environment: A Demonstration with Paillier Encryption and SGX[C]// ACM. 9th ACM CCS International Workshop on Managing Insider Security Threats(MIST). New York:ACM, 2017: 85-88. |
| [15] | SUN Haiyou, XIAO Sheng. DNA-X: Dynamic Network Authentication Using SGX[C]// ACM. 2nd International Conference on Cryptography, Security and Privacy(ICCSP). New York:ACM, 2018: 110-115. |
| [16] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology(TIST), 2019, 10(2): 1-19. |
| [17] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21)[2022-03-04]. https://eprint.iacr.org/2016/086. |
| [18] |
VIGANO L. Automated Security Protocol Analysis with the AVISPA Tool[J]. Electronic Notes in Theoretical Computer Science, 2006, 155: 61-86.
doi: 10.1016/j.entcs.2005.11.052 URL |
| [19] | KAUR K, GARG S, KADDOUM G, et al. A Lightweight and Privacy-Preserving Authentication Protocol for Mobile Edge Computing[C]// IEEE. 2019 IEEE Global Communications Conference(GLOBECOM). New York: IEEE, 2019: 1-6. |
| [20] |
SOWJANYA K, DASGUPTA M, RAY S. An Elliptic Curve Cryptography Based Enhanced Anonymous Authentication Protocol for Wearable Health Monitoring Systems[J]. International Journal of Information Security, 2020, 19(1): 129-146.
doi: 10.1007/s10207-019-00464-9 URL |
| [21] |
TSOBDJOU L D, PIERRE S, QUINTERO A. A New Mutual Authentication and Key Agreement Protocol for Mobile Client-Server Environment[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1275-1286.
doi: 10.1109/TNSM.2021.3071087 URL |
| [22] | LIU Xin, YANG Haorui, GUO Zhenbin, et al. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things[J]. Netinfo Security, 2021, 21(7): 1-9. |
| 刘忻, 杨浩睿, 郭振斌, 等. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7):1-9. |
| [1] | 吕国华, 胡学先, 杨明, 徐敏. 基于联邦随机森林的船舶AIS轨迹分类算法[J]. 信息网络安全, 2022, 22(4): 67-76. |
| [2] | 于俊清, 李自尊, 吴驰, 赵贻竹. 面向软件定义网络的两级DDoS攻击检测与防御[J]. 信息网络安全, 2022, 22(1): 1-8. |
| [3] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [4] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [5] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [6] | 王跃东, 熊焰, 黄文超, 武建双. 一种面向5G专网鉴权协议的形式化分析方案[J]. 信息网络安全, 2021, 21(9): 1-7. |
| [7] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [8] | 刘忻, 杨浩睿, 郭振斌, 王家寅. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7): 1-9. |
| [9] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [10] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| [11] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [12] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [13] | 孙子文, 张向阳. 大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议[J]. 信息网络安全, 2020, 20(6): 26-35. |
| [14] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [15] | 徐国天, 沈耀童. 基于XGBoost和LightGBM双层模型的恶意软件检测方法[J]. 信息网络安全, 2020, 20(12): 54-63. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||