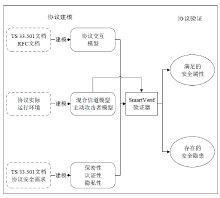
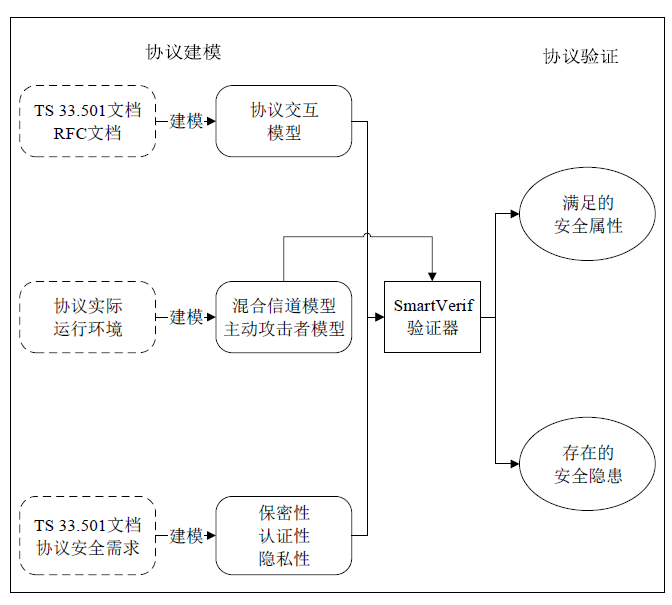
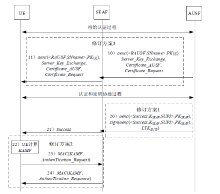
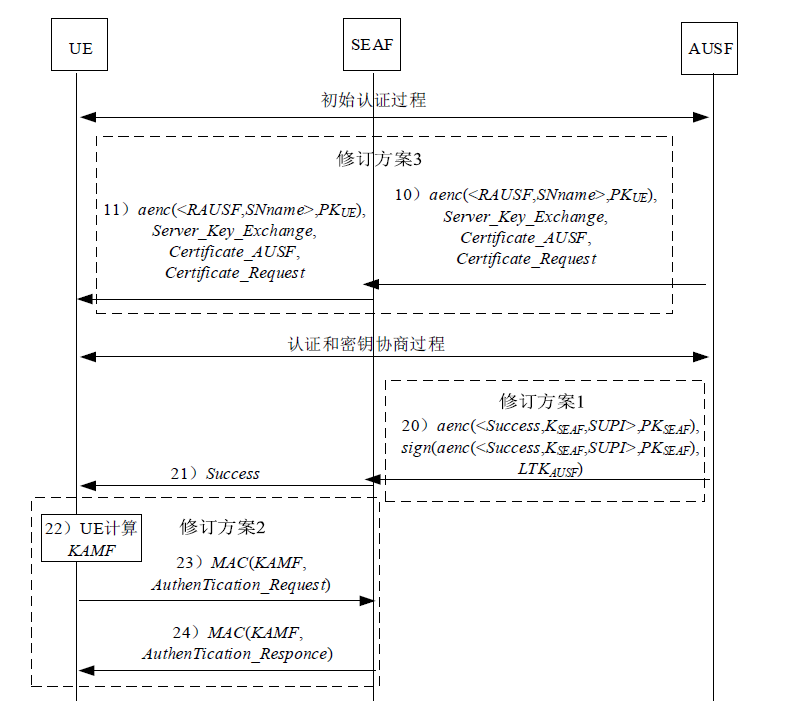
| [1] |
BROEK F V D, VERDULT R, DE RUITER J. Defeating IMSI Catchers [C]//ACM. 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, CO, USA. New York: ACM, 2015: 340-351.
|
| [2] |
BLANCHET B. An Efficient Cryptographic Protocol Verifier Based on Prolog Rules [C]//IEEE. 2001 IEEE Computer Security Foundations Symposium, June 11-13, 2001, Cape Breton, Nova Scotia, Canada. New Jersey: IEEE, 2001: 82-96.
|
| [3] |
CHEVAL V, KREMER S, RAKOTONIRINA I. DEEPSEC: Deciding Equivalence Properties in Security Protocols Theory and Practice [C]//IEEE. 2018 IEEE Symposium on Security and Privacy(SP), May 21-23, 2018, San Francisco, California, USA. New Jersey: IEEE, 2018: 529-546.
|
| [4] |
BASIN D, DREIER J, HIRSCHI L, et al. A Formal Analysis of 5G [C]//ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19, 2018, Toronto, ON, Canada. New York: ACM, 2018: 1383-1396.
|
| [5] |
MEIER S, SCHMIDT B, CREMERS C, et al. The TAMARIN Prover for the Symbolic Analysis of Security Protocols [C]//Springer. International Conference on Computer Aided Verification, July 13-19, 2013, Saint Petersburg, Russia. Heidelberg: Springer, 2013: 696-701.
|
| [6] |
CREMERS C, DEHNEL-WILD M. Component-based Formal Analysis of 5G-AKA: Channel Assumptions and Session Confusion [C]//ISOC. Network and Distributed Systems Security(NDSS) Symposium, February 24-27, 2019, San Diego, California, USA. Rosten: ISOC, 2019: 1245-1260.
|
| [7] |
ZHANG Jiajing, WANG Qiang, YANG Lin, et al. Formal Verification of 5G-EAP-TLS Authentication Protocol [C]//IEEE. IEEE 4th International Conference on Data Science in Cyberspace(DSC), June 23-25, 2019, Hangzhou, China. New Jersey: IEEE, 2019: 503-509.
|
| [8] |
ZHANG Jiajing, WANG Qiang, YANG Lin, et al. Formal Analysis of 5G EAP-TLS Authentication Protocol Using ProVerif[EB/OL]. https://www.researchgate.net/publication/338985300_Formal_Analysis_of_5G_EAP-TLS_Authentication_Protocol_Using_Proverif, 2020-12-22.
|
| [9] |
CREMERS C. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols [C]//Springer. International Conference on Computer Aided Verification, July 7-14, 2008, Princeton, NJ, USA. Heidelberg: Springer, 2008: 414-418.
|
| [10] |
XIONG Yan, SU Cheng, HUANG Wenchao, et al. Smartverif: Push the Limit of Automation Capability of Verifying Security Protocols by Dynamic Strategies[EB/OL]. https://www.usenix.org/conference/usenixsecurity20/presentation/xiong, 2020-08-12.
|
| [11] |
DOLEV D, YAO Qizhi. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208.
doi: 10.1109/TIT.1983.1056650
URL
|
| [12] |
LOWE G. A Hierarchy of Authentication Specifications [C]//IEEE. 10th Computer Security Foundations Workshop, June 10-12, 1997, Rockport, MA, USA. New Jersey: IEEE, 1997: 31-43.
|
| [13] |
ARAPINIS M, MANCINI L, RITTER E, et al. New Privacy Issues in Mobile Telephony: Fix and Verification [C]//ACM. 2012 ACM Conference on Computer and Communications Security, October 16-18, 2012, Raleigh, NC, USA. New York: ACM, 2012: 205-216.
|
 ), XIONG Yan1, HUANG Wenchao1, WU Jianshuang2
), XIONG Yan1, HUANG Wenchao1, WU Jianshuang2