信息网络安全 ›› 2018, Vol. 18 ›› Issue (2): 61-70.doi: 10.3969/j.issn.1671-1122.2018.02.009
基于SPIN的安全协议的攻击者建模方法研究
易辉凡1,2, 万良1,2( ), 黄娜娜1,2, 王鹍鹏1,2
), 黄娜娜1,2, 王鹍鹏1,2
- 1.贵州大学计算机科学与技术学院,贵州贵阳 550025
2.贵州大学计算机软件与理论研究所,贵州贵阳 550025
Research on Attacker Modeling Method of Security Protocol Based on SPIN
Huifan YI1,2, Liang WAN1,2( ), Nana HUANG1,2, Kunpeng WANG1,2
), Nana HUANG1,2, Kunpeng WANG1,2
- 1.College of Computer Science and Technology,Guizhou University, Guiyang Guizhou 550025, China
2. Computer Software and Theoretical Research Institute, Guizhou University, Guiyang Guizhou 550025, China
摘要:
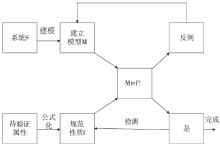
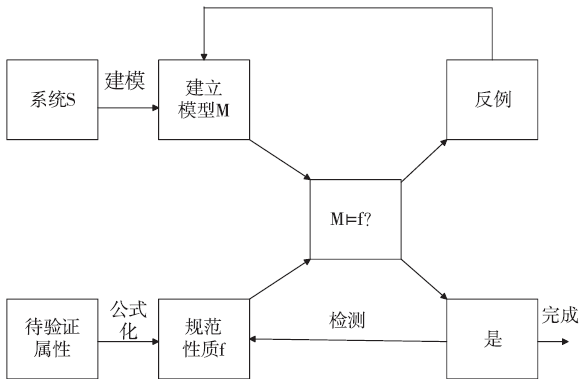
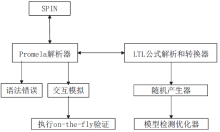
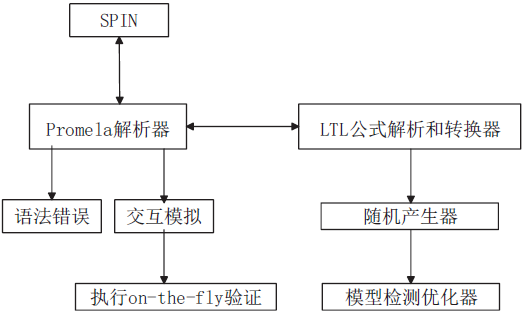
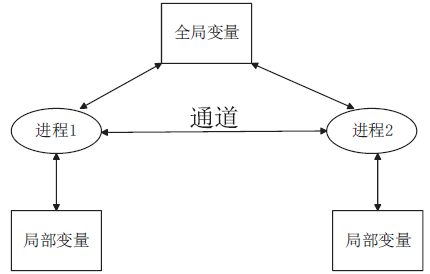
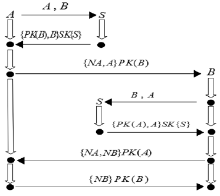
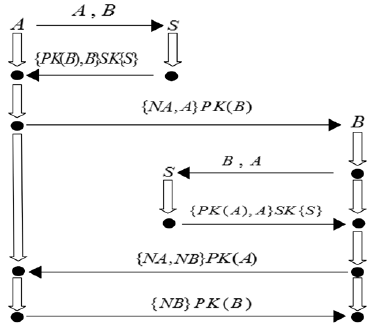
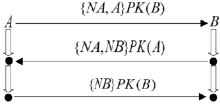
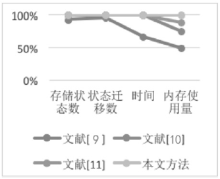
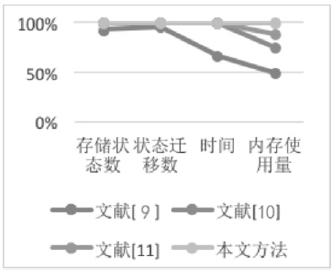
安全协议是确保网络安全的关键,在现有的技术条件下,已经有许多方法来分析协议的安全性,但是对攻击者建模的方法不够高效,导致协议的检测和分析效率较低。形式化方法是检验协议安全性的一种手段,它能高效地分析验证协议设计中存在的漏洞。模型检测作为形式化方法的一种,具有简洁、高效和自动化程度高的特性,模型检测器SPIN具有强大的检测能力。文章使用SPIN对安全协议进行研究,提出了一种更有效的方法来验证攻击者模型的安全协议,首先对攻击者行为进行分析,获取攻击者初始知识库,根据分解规则和合成规则不断地更新攻击者知识库;其次形式化分析各诚实主体,并建立各诚实主体和攻击者的Promela语义模型;最后使用模型检测器SPIN进行验证。实验结果表明,文章提出的方法能使模型复杂度降低,大幅度减少模型的状态数量,有效地避免状态空间爆炸,提升验证效率。
中图分类号: