信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 91-101.doi: 10.3969/j.issn.1671-1122.2021.12.013
基于贝叶斯网络的视频专网安全风险分析方法
- 1.中国人民公安大学信息网络安全学院,北京 100026
2.公安部安全防范技术与风险评估重点实验室,北京 100026
3.中国信息通信研究院安全研究所,北京 100191
-
收稿日期:2021-09-17出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:李欣 E-mail:lixin@ppsuc.edu.cn -
作者简介:朱容辰(1996—),男,山东,硕士研究生,主要研究方向为网络安全、风险评估|李欣(1977—),男,江西,副教授,博士,主要研究方向为网络安全|林小暖(1996—),女,山东,硕士,主要研究方向为国际ICT产业与政策、网络安全 -
基金资助:国家自然科学基金项目(62076246);公安部科技强警基础工作专项项目(2020GABJC01);中国人民公安大学拔尖创新人才培养经费支持研究生科研创新项目(2021yjsky016)
The Security Risk Analysis Method for Video Private Network Based on Bayesian Network
ZHU Rongchen1, LI Xin1,2( ), LIN Xiaonuan3
), LIN Xiaonuan3
- 1. School of Information Network Security, People’s Public Security University of China, Beijing 100026, China
2. Security Prevention Technology and Risk Assessment Key Laboratory of Ministry of Public Security,Beijing 100026, China
3. Security Research Institute of China Academy of Information and Communications Technology, Beijing 100191
-
Received:2021-09-17Online:2021-12-10Published:2022-01-11 -
Contact:LI Xin E-mail:lixin@ppsuc.edu.cn
摘要:
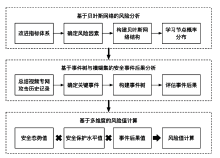
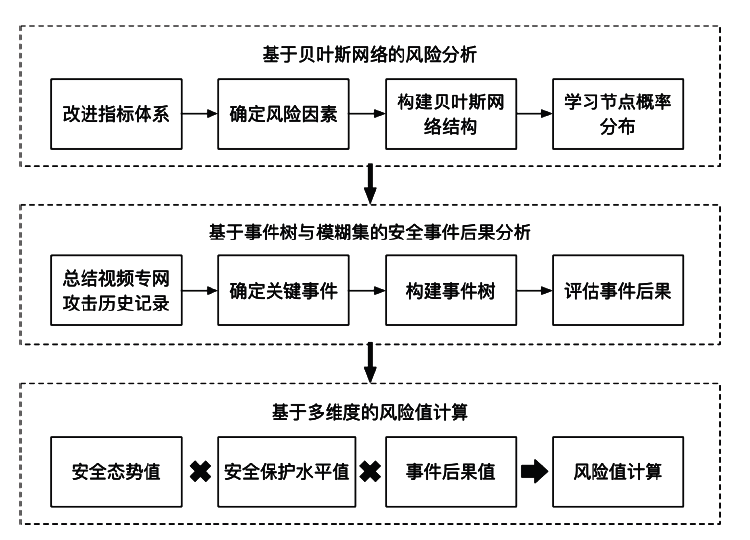
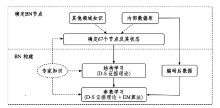
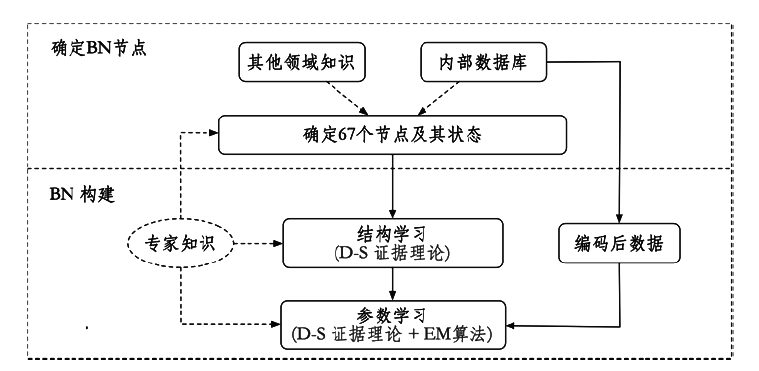
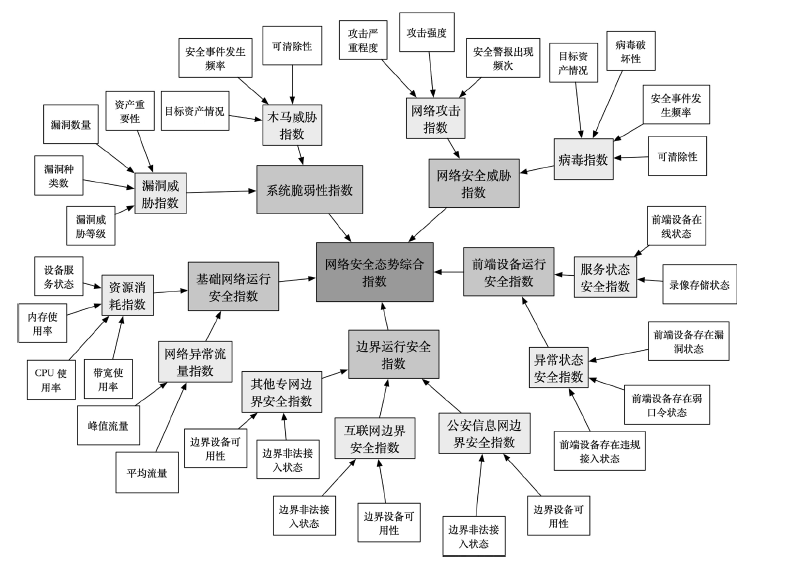
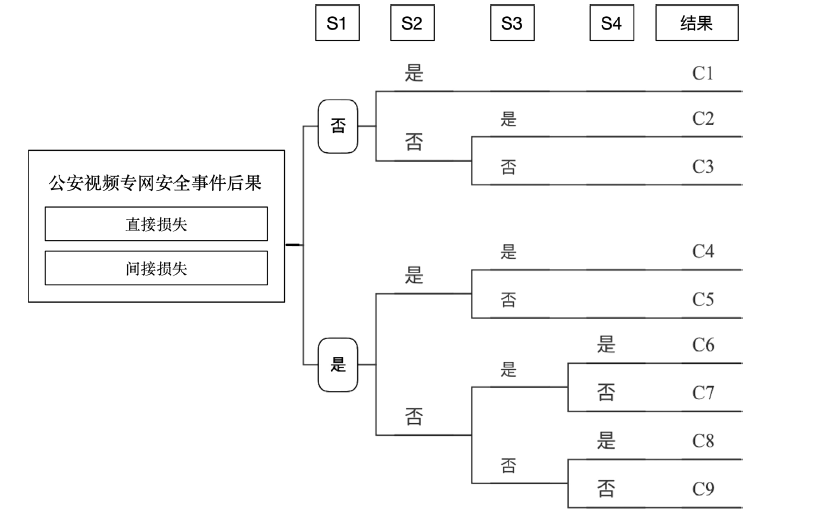
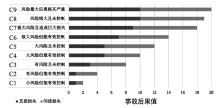
公安视频专网是为视频监控系统联网及应用而建立的专门网络,是提高公安工作效率、辅助侦破案件的利器,有效的安全风险评估可以指导配置安全保护资源并补齐短板。针对公安视频专网的安全风险评估研究不足。文章提出了一种视频专网安全风险评估方法,从视频专网安全态势、安全保护水平、运行安全风险因素、安全事件后果等多维度考虑专网安全风险。借助贝叶斯网络(Bayesian Network,BN)、事件树和模糊集理论细粒度总结风险因素,动态分析并量化风险值。通过情景分析、部分验证与案例研究的方法验证合理性与有效性,验证结果表明,该方法有助于提高公安部门对视频专网的安全风险感知、分析与评估能力。
中图分类号:
引用本文
朱容辰, 李欣, 林小暖. 基于贝叶斯网络的视频专网安全风险分析方法[J]. 信息网络安全, 2021, 21(12): 91-101.
ZHU Rongchen, LI Xin, LIN Xiaonuan. The Security Risk Analysis Method for Video Private Network Based on Bayesian Network[J]. Netinfo Security, 2021, 21(12): 91-101.
| [1] |
LUKO S N. Risk Management Principles and Guidelines[J]. Quality Engineering, 2013, 25(4):451-454.
doi: 10.1080/08982112.2013.814508 URL |
| [2] | DUAN Yongcheng. Extraction and Evaluation of Network Security Situation Elements for Video Private Network[D]. Beijing: People’s Public Security University of China, 2020. |
| 段詠程. 面向视频专网的网络安全态势要素提取与评估[D]. 北京:中国人民公安大学, 2020. | |
| [3] | LI Xin, DUAN Yongcheng, HUANG Shuhua, et al. Research on the Construction of Network Security Situation Index System for Video Private Network[J]. Journal of Beijing University of Aeronautics and Astronautics, 2020, 46(9):1625-1634. |
| 李欣, 段詠程, 黄淑华, 等. 面向视频专网的网络安全态势指标体系的构建研究[J]. 北京航空航天大学学报, 2020, 46(9):1625-1634. | |
| [4] | WU Jiansong, XU Shengdi, ZHOU Rui, et al. Scenario Analysis of Mine Water Inrush Hazard Using Bayesian Networks[J]. Safety Science, 2016, 26(89):231-239. |
| [5] | ZHANG Chao, WU Jiansong, HU Xiaofeng, et al. A Probabilistic Analysis Model of Oil Pipeline Accidents Based on an Integrated Event-Evolution-Bayesian (EEB) Model[J]. Process Safety and Environmental Protection, 2018, 28(117):694-703. |
| [6] |
ZHU Rongchen, LI Xin, HU Xiaofeng, et al. Risk Analysis of Chemical Plant Explosion Accidents Based on Bayesian Network[J]. Sustainability, 2019, 12(1):1-20.
doi: 10.3390/su12010001 URL |
| [7] |
ZHANG Yiyi, HU Xiaofeng, BAI Yuchen, et al. Risk Assessment of Gas Leakage from School Laboratories Based on the Bayesian Network[J]. International Journal of Environmental Research and Public Health, 2020, 17(2):426-436.
doi: 10.3390/ijerph17020426 URL |
| [8] | LANDUCCI G, ARGENTI F, COZZANI V, et al. Assessment of Attack Likelihood to Support Security Risk Assessment Studies for Chemical Facilities[J]. Process Safety and Environmental Protection, 2017, 27(110):102-114. |
| [9] |
PATE-CORNELL M E, GUIKEMA S D. Probabilistic Modeling or Terrorist Threats: A Systems Analysis Approach to Setting Priorities Among Countermeasures[J]. Military Operations Research, 2008, 13(3):89-93.
doi: 10.5711/morj.13.3.89 URL |
| [10] | HUSMEIER D. Introduction to Learning Bayesian Networks from Data[M]. Berlin: Springer, 2005. |
| [11] | ZHOU Deyu, XU Haiyang, HE Yulan. An Unsupervised Bayesian Modelling Approach for Storyline Detection on News Articles[C]// ACL. 2015 Conference on Empirical Methods in Natural Language Processing, September 17-21, 2015, Lisbon, Portugal. New York: Association for Computational Linguistics, 2015: 1943-1948. |
| [12] | WANG Litao, JIA Meisheng, SHI Yi, et al. A Knowledge-based Reasoning Model for Crime Reconstruction and Investigation[J]. Expert Systems with Applications, 2020, 30(159):113-119. |
| [13] | WU Jiansong, XU Shengdi, ZHOU Rui, et al. Scenario Analysis of Mine Water Inrush Hazard Using Bayesian Networks[J]. Safety Science, 2016, 26(89):231-239. |
| [14] |
ZERROUKI H, SMADI H. Bayesian Belief Network Used in the Chemical and Process Industry: A Review and Application[J]. Journal of Failure Analysis and Prevention, 2017, 17(1):159-165.
doi: 10.1007/s11668-016-0231-x URL |
| [15] | LASKEY K B, SUZANNE L, WRIGHT E, et al. Hypothesis Management in Situation-specific Network Construction[EB/OL]. https://arxiv.org/ftp/arxiv/papers/1301/1301.2287.pdf, 2002-07-10. |
| [16] |
DEMPSTER A P. Upper and Lower Probabilities Induced by a Multivalued Mapping[J]. Annals of Mathematical Statistics, 1967, 38(2):325-339.
doi: 10.1214/aoms/1177698950 URL |
| [17] | LIU Liping, YAGER R R. Classic Works of the Dempster-shafer Theory of Belief Functions[M]. Berlin: Springer, 2008. |
| [18] | KLEEMANN J, CELIO E, FÜRST C. Validation Approaches of an Expert-based Bayesian Belief Network in Northern Ghana, West Africa[J]. Ecological Modelling, 2017, 33(365):10-29. |
| [19] | KABIR G, BALEK N B C, TESFAMARIAM S. Consequence-based Framework for Buried Infrastructure Systems: A Bayesian Belief Network Model[J]. Reliability Engineering & System Safety, 2018, 17(180):290-301. |
| [20] |
KHAKZAD N, MARTINEZ I S, KWON H M, et al. Security Risk Assessment and Management in Chemical Plants: Challenges and New Trends[J]. Process Safety Progress, 2018, 37(2):211-230.
doi: 10.1002/prs.v37.2 URL |
| [21] | DUAN Yongcheng, WANG Yuqing, LI Xin, et al. Extraction of Random Forest Network Security Situation Elements Based on RSAR[J]. Netinfo Security, 2019, 19(7):75-81. |
| 段詠程, 王雨晴, 李欣, 等. 基于RSAR的随机森林网络安全态势要素提取[J]. 信息网络安全, 2019, 19(7):75-81. | |
| [22] |
JONES B, JENKINSON I, YANG Z, et al. The Use of Bayesian Network Modelling for Maintenance Planning in a Manufacturing Industry[J]. Reliability Engineering & System Safety, 2010, 95(3):267-277.
doi: 10.1016/j.ress.2009.10.007 URL |
| [1] | 罗文华, 张耀文. 基于贝叶斯网络的电信网络诈骗受害人特征分析[J]. 信息网络安全, 2021, 21(12): 25-30. |
| [2] | 赵小林, 赵斌, 赵晶晶, 薛静锋. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27. |
| [3] | 刘永磊, 金志刚, 郝琨, 张伟龙. 基于STRIDE和模糊综合评价法的移动支付系统风险评估[J]. 信息网络安全, 2020, 20(2): 49-56. |
| [4] | 肖彪, 闫宏强, 罗海宁, 李炬成. 基于差分隐私的贝叶斯网络隐私保护算法的改进研究[J]. 信息网络安全, 2020, 20(11): 75-86. |
| [5] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [6] | 王庆, 屠晨阳, shenjiahui@iie.ac.cn. 侧信道攻击通用框架设计及应用[J]. 信息网络安全, 2017, 17(5): 57-62. |
| [7] | 董晓宁, 赵华容, 李殿伟, 王甲生. 基于模糊证据理论的信息系统安全风险评估研究[J]. 信息网络安全, 2017, 17(5): 69-73. |
| [8] | 梁智强, 林丹生. 基于电力系统的信息安全风险评估机制研究[J]. 信息网络安全, 2017, 17(4): 86-90. |
| [9] | 李涛, 张驰. 基于信息安全等保标准的网络安全风险模型研究[J]. 信息网络安全, 2016, 16(9): 177-183. |
| [10] | 尹心明, 胡正梁, 陈国梁, 黄海晔. 基于设备指纹决策树分类的IP视频专网入网检测方案研究[J]. 信息网络安全, 2016, 16(12): 68-73. |
| [11] | 滕希龙, 曲海鹏. 基于区间值直觉模糊集相似性的信息安全风险评估方法研究[J]. 信息网络安全, 2015, 15(5): 62-68. |
| [12] | 文伟平, 郭荣华, 孟正, 柏皛. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全, 2015, 15(2): 7-8. |
| [13] | 何鹏程, 方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全, 2015, 15(1): 61-65. |
| [14] | 王星河, 余洋, 夏春和. 面向网络协同防御的动态风险评估模型[J]. 信息网络安全, 2014, 14(9): 39-43. |
| [15] | 章恒, 禄凯. 构建云计算环境的安全检查与评估指标体系[J]. 信息网络安全, 2014, 14(9): 115-119. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||