信息网络安全 ›› 2017, Vol. 17 ›› Issue (5): 69-73.doi: 10.3969/j.issn.1671-1122.2017.05.011
基于模糊证据理论的信息系统安全风险评估研究
- 1. 海军参谋部,北京 100841
2. 海军工程大学信息安全系,湖北武汉 430033
Research on Information Systems Security Risk Assessment Based on Fuzzy Theory of Evidence
Xiaoning DONG1, Huarong ZHAO1( ), Dianwei LI1, Jiasheng WANG2
), Dianwei LI1, Jiasheng WANG2
- 1. Naval Staff, Beijing 100841, China
2. Department of Information Security, Naval University of Engineering, Wuhan Hubei 430033, China
摘要:
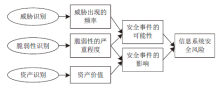
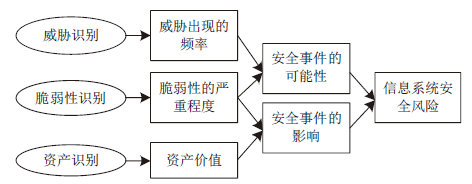
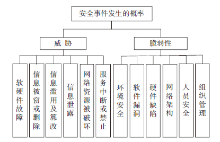
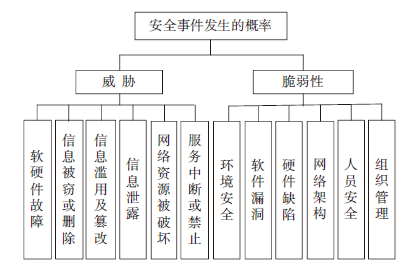
针对系统风险评估过程中存在的如评估数据缺乏、知识不完备、系统建模不完整及风险识别不充分等不确定性因素,文章提出了一种将模糊数学理论与证据理论相结合的风险评估方法。首先,给出了信息系统风险评估的定义,讨论了信息系统的风险分析与预测模型;然后,将传统证据理论向模糊集推广,利用模糊集的隶属函数构造证据理论中的基本概率赋值函数,评估指标的基本支持度的确定即为各项指标对于评语集的隶属程度,从而建立起一个从指标集到评估标准的模糊关系,有效解决了证据理论中基本概率赋值函数不易确定的问题;最后,给出了某办公自动化信息系统的风险评估实例,验证了文中所提方法的合理性。实例表明,该方法可行有效,能够为信息系统风险控制和安全防御提供有力的数据支撑。
中图分类号: