信息网络安全 ›› 2017, Vol. 17 ›› Issue (3): 27-32.doi: 10.3969/j.issn.1671-1122.2017.03.005
基于角色行为模式挖掘的内部威胁检测研究
- 1. 海军参谋部,北京 100841
2. 92529部队,浙江台州 317600
3. 海军工程大学信息安全系,湖北武汉 430033
-
收稿日期:2016-12-15出版日期:2017-03-20发布日期:2020-05-12 -
作者简介:作者简介:李殿伟(1965—),男,河南,高级工程师,硕士,主要研究方向为信息安全、维修保障;何明亮(1988—),男,湖北,硕士,主要研究方向为信息安全;袁方(1988—),男,湖北,硕士研究生,主要研究方向为信息安全。
-
基金资助:湖北省自然科学基金[2015CF867]
Research on Insider Threat Detection Based on Role Behavior Pattern Mining
Dianwei LI1, Mingliang HE2( ), Fang YUAN3
), Fang YUAN3
- 1. Naval Staff, Beijing 100841, China
2. No.92529 Troops of PLA, Taizhou Zhejiang 317600, China
3. Information Security Department, Naval University of Engineering, Wuhan Hubei 430033, China
-
Received:2016-12-15Online:2017-03-20Published:2020-05-12
摘要:
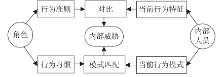
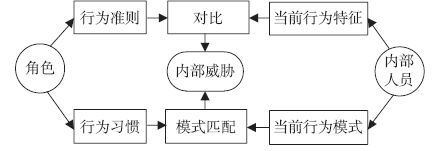
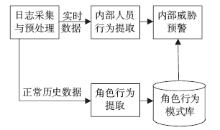
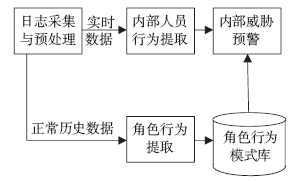
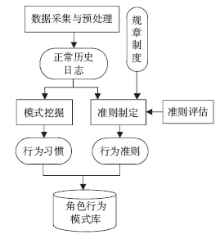
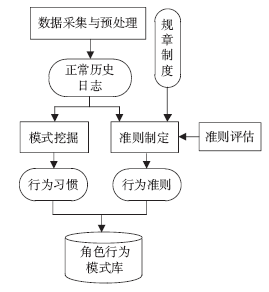
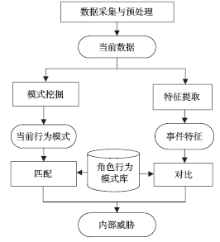
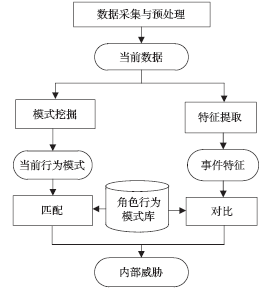
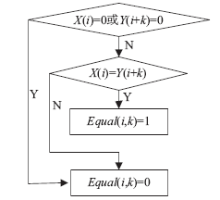
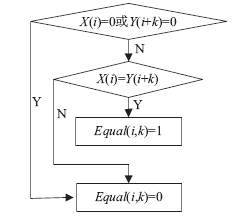
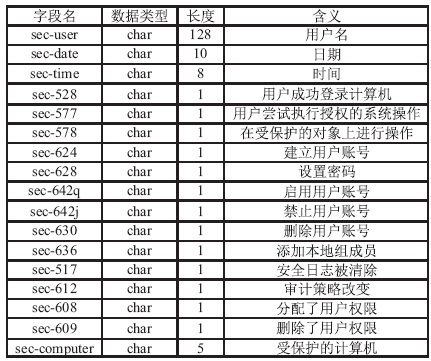
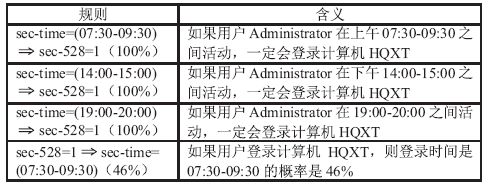
针对信息系统内部威胁难于检测的问题,文章将访问控制与数据挖掘相结合,设计了一种基于角色行为模式挖掘的内部威胁检测模型,提出了一种基于用户角色行为准则、行为习惯与实际操作行为匹配的内部威胁预警方法。信息系统中每一个操作使用人员和运维管理人员都有自己的职责,表现在系统使用上就是各个用户都有自己所扮演的角色,而每种角色都有自己的行为准则和行为习惯。文章根据系统规范抽取角色行为准则,同时采用数据挖掘技术从系统日志和应用软件日志中提取用户行为习惯和日常操作,通过检测用户实际行为与角色行为准则和行为习惯的背离程度,实现了内部威胁预警。
中图分类号:
引用本文
李殿伟, 何明亮, 袁方. 基于角色行为模式挖掘的内部威胁检测研究[J]. 信息网络安全, 2017, 17(3): 27-32.
Dianwei LI, Mingliang HE, Fang YUAN. Research on Insider Threat Detection Based on Role Behavior Pattern Mining[J]. Netinfo Security, 2017, 17(3): 27-32.
| [1] | PARKER D B.Fighting Computer Crime: A New Framework for Protecting Information[M]. New York: John Wiley & Sons, 1998. |
| [2] | WOOD B J. An Insider Threat Model for Adversary Simulation[EB/OL]. , 2016-11-12. |
| [3] | PARK J S, HO S M. Composite Role-based Monitoring (CRBM) for Countering Insider Threats[EB/OL]. , 2016-11-12. |
| [4] | RAY I, POOLSAPASSIT N.Using Attack Trees to Identify Malicious Attacks from Authorized Insiders[C]//Spring. 10th European Symposium on Research in Computer Security, September 12-14, 2005, Milan, Italy. Heidelberg: Spring, 2005: 231-246. |
| [5] | 叶伟伟,欧庆于,柏小武. 基于服务架构的密码服务系统认证方案研究[J]. 信息网络安全,2016(5):37-43. |
| [6] | SEO Y W, SYCARA K.Cost-sensitive Access Control for Illegitimate Confidential Access by Insiders[C]//2006 International Conference on Intelligence and Security Informatics, May 23-24, 2006, San Diego, CA, USA. Heidelberg: Spring, 2006, 3975: 117-128. |
| [7] | 邵剑雨,陈福臻,秦鹏宇,等. 移动互联网环境下基于动态信任值的访问控制方法研究[J]. 信息网络安全,2016(8):46-53. |
| [8] | BYUN J W, LI Ninghui.Purpose Based Access Control for Privacy Protection in Relational Database Systems[J]. VLDB International Journal on Very Large Data Bases, 2008, 17(4): 603-619. |
| [9] | BEIMEL D, PELEG M.The Context and the SitBAC Models for Privacy Preservation-An Experimental Comparison of Model Comprehension and Synthesis[J]. IEEE Transactions on Knowledge and Data Engineering, 2010, 22(10): 1475-1488. |
| [10] | 孙超. 基于用户行为和关系的内部风险分析[D]. 济南:山东大学,2015. |
| [11] | KAMRA A, TERZI E, BERTINO E.Detecting Anomalous Access Patterns in Relational Databases[J]. VLDB Journal- the International Journal on Very Large Data Bases, 2008, 17(5): 1063-1077. |
| [12] | KHOLIDY H A, BAIARDI F, Hariri S.DDSGA: A Data-driven Semi-global Alignment Approach for Detecting Masquerade Attacks[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 12(2): 164-178. |
| [13] | MALOOF M A, STEPHENS G D.ELICIT: A System for Detecting Insiders Who Violate Need-to-Know[C]//Spring. 10th International Conference on Recent Advances in Intrusion Detection (RAID) September 5-7, 2007, Gold Goast, Australia. Heidelberg: Springer, 2007: 146-166. |
| [14] | 文雨,王伟平,孟丹. 面向内部威胁检测的用户跨域行为模式挖掘[J]. 计算机学报,2016,39(8):1-15. |
| [15] | 张锐. 基于文件访问行为的内部威胁异常检测模型研究[D]. 北京:北京交通大学,2015. |
| [16] | 郭东峰. 基于分层特征云计算模型的电网内部威胁检测[J]. 计算机测量与控制,2013,21(2):340-343. |
| [17] | 章文明. 基于异常概率和隐马尔科夫模型的资源滥用行为[D]. 衡阳:南华大学,2012. |
| [18] | 闫超,南凯. 基于语义标签的协同信息系统内部隐私威胁检测模型[J]. 科研信息化技术与应用,2015,6(3):3-13. |
| [19] | 杨姗媛,朱建明. 基于内部威胁的信息安全风险管理模型及防范措施[J]. 管理现代化,2013,(2):47-49. |
| [20] | 矢敏,叶伟伟,欧庆于. 不需双线性对的基于身份的认证密钥协商协议[J]. 信息网络安全,2016(10):21-27. |
| [21] | 梁礼,杨君刚,朱广良,等. 基于实时告警的层次化网络安全风险评估方法[J]. 计算机工程与设计,2013,34(7):2316-2323. |
| [22] | 程思嘉,张昌宏,潘帅卿. 基于CP-ABE算法的云存储数据访问控制方案设计[J]. 信息网络安全,2016(2):1-6. |
| [23] | BARTH A, BONEH D, WATERS B.Privacy in Encrypted Content Distribution using Private Broadcast Encryption[C]//ACM. 10th International Conference on Financial Cryptography and Data Security, February 27-March 2, 2006, Anguilla, British West Indies. New York: ACM, 2006: 52-64. |
| [24] | 范运东,吴晓平,石雄. 基于信任值评估的云计算访问控制模型研究[J]. 信息网络安全,2016(7):71-77. |
| [25] | GUNTER C A, LIEBOVITZ D M, MALIN B.Experience-based Access Management: A Life-cycle Framework for Identity and Access Management Systems[J]. IEEE Security and Privacy Magazine, 2011, 9(5): 48-55. |
| [1] | 郑国刚. 重要信息系统安全检查实施方法与技术措施[J]. 信息网络安全, 2019, 19(9): 16-20. |
| [2] | 张蕾华, 牛红太, 王仲妮, 刘雪红. 基于大数据的前科人员犯罪预警模型构建研究[J]. 信息网络安全, 2019, 19(4): 82-89. |
| [3] | 蒋卓键, 伍淳华, 夏铭. 云系统中多层次用户分类方法研究与实现[J]. 信息网络安全, 2017, 17(8): 69-75. |
| [4] | 徐燕. 基于数据挖掘的网络链接预测研究[J]. 信息网络安全, 2017, 17(6): 30-34. |
| [5] | 董晓宁, 赵华容, 李殿伟, 王甲生. 基于模糊证据理论的信息系统安全风险评估研究[J]. 信息网络安全, 2017, 17(5): 69-73. |
| [6] | 顾春华, 高远, 田秀霞. 安全性优化的RBAC访问控制模型[J]. 信息网络安全, 2017, 17(5): 74-79. |
| [7] | 方跃坚, 朱锦钟, 周文, 李同亮. 数据挖掘隐私保护算法研究综述[J]. 信息网络安全, 2017, 17(2): 6-11. |
| [8] | 庄浩霖, 尚涛, 刘建伟. 基于角色的大数据认证授权一体化方案[J]. 信息网络安全, 2017, 17(11): 55-61. |
| [9] | 曾瑜, 郭金全. 工业控制系统信息安全现状分析[J]. 信息网络安全, 2016, 16(9): 169-172. |
| [10] | 杨旭东. 网络舆情监控系统关键技术研究[J]. 信息网络安全, 2016, 16(9): 251-256. |
| [11] | 高君丰, 崔玉华, 罗森林, 焦龙龙. 信息系统可控性评价研究[J]. 信息网络安全, 2015, 15(8): 67-75. |
| [12] | 滕希龙, 曲海鹏. 基于区间值直觉模糊集相似性的信息安全风险评估方法研究[J]. 信息网络安全, 2015, 15(5): 62-68. |
| [13] | 陈晓, 赵晶玲. 大数据处理中混合型聚类算法的研究与实现[J]. 信息网络安全, 2015, 15(4): 45-49. |
| [14] | 吉晨,李小强,柳倩. 地理信息系统中的结构化数据保护方法[J]. 信息网络安全, 2015, 15(11): 71-76. |
| [15] | 胡雪,封化民,李明伟,丁钊. 数据挖掘中一种增强的Apriori算法分析[J]. 信息网络安全, 2015, 15(11): 77-83. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||