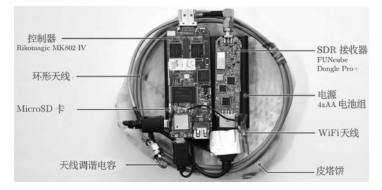
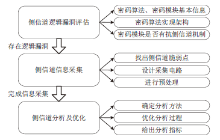
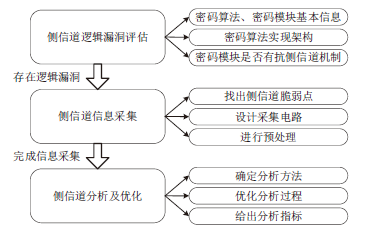
| [1] |
KOCHER P, JAFFE J, JUN B.Differential Power Analysis[C] // CRYPTO’99. Advances in Cryptology—CRYPTO’99, August 15-19, 1999,Santa Barbara, California, USA . Berlin, Heidelberg:Springer, 1999: 789-789.
|
| [2] |
KESLSEY J, SCHNEIER B, WAGNER D, et al.Side Channel Cryptanalysis of Product Ciphers[J]. European Symposium on Computer Security-esorics , 1998 , 8(23) :97-110.
|
| [3] |
AGRAWAL D, ARCHAMBEULT B, RAO J R, et al. The EM Side-Channel(s):Attacks and Assessment Methodologies[EB/OL].,2017-4-15.
|
| [4] |
LEMKE K, SCHRAMM K, PAAR C.DPA on n -Bit Sized Boolean and Arithmetic Operations and Its Application to IDEA, RC6, and the HMAC-Construction[J].Lecture Notes in Computer Science, 2004 , 3156(4) :205-219.
|
| [5] |
GANDOLFI K, MOURTEL C, OLIVIER F. Electromagnetic Analysis: Concrete Results[EB/OL]. .
|
| [6] |
HUTTER M, MANGARD S, FELDHOFER M.Power and EM Attacks on Passive 13.56MHz RFID Devices[C] // ACM. CHES ‘07 Proceedings of the 9th international workshop on Cryptographic Hardware and Embedded Systems ,September 10 - 13, 2007, Vienna, Austria. Berlin, Heidelberg:Springer, 2007: 320-333.
|
| [7] |
CORON J S. Resistance Against Differential Power Analysis For Elliptic Curve Cryptosystems[EB/OL]..
|
| [8] |
矢敏,叶伟伟,欧庆于.>不需双线性对的基于身份的认证密钥协商协议[J]. 信息网络安全,2016(10):21-27.
|
| [9] |
MANGARD S. A Simple Power-Analysis (SPA) Attack on Implementations of the AES Key Expansion[EB/OL]. .
|
| [10] |
FISCHER W, GAMMEL B M, KNIFFLER O, et al. Differential Power Analysis of Stream Ciphers[EB/OL]. .
|
| [11] |
YUAN K, GU D, GUO Z, et al.A Highly Efficient Correlation Power Analysis on PRINT Cipher[C] // CIS ‘12.2012 Eighth International Conference on Computational Intelligence and Security, November 17 - 18, 2012 ,Guangzhou, China.New York: IEEE, 2012: 442-446.
|
| [12] |
ZHANG J, GU D, GUO Z, et al.Differential Power Cryptanalysis Attacks Against PRESENT Implementation[C] // IEEE.Advanced Computer Theory and Engineering (ICACTE),August20-22,2010 ,Chengdu, China. New York:IEEE, 2010: 61-65.
|
| [13] |
EISENBARTH T, KASPER T, MORADI A, et al.On the Power of Power Analysis in the Real World: A Complete Break of the KeeLoq Code Hopping Scheme[C] //Springer .Advances in Cryptology - CRYPTO 2008, August 17-21, 2008, Santa Barbara, California, USA. Berlin, Heidelberg:Springer, 2008: 203-220.
|
| [14] |
ZHOU Y, YU Y, STANDAERT F X, et al.On the Need of Physical Security for Small Embedded Devices: A Case Study with COMP128-1 Implementations in SIM Cards[C] // Springer .International Conference on Financial Cryptography and Data Security 2013, April 1-5, 2013,Okinawa, Japan. Berlin, Heidelberg:Springer, 2013, 230-238.
|
| [15] |
GENKIN D, PIPMAN I, TROMER E.Get Your Hands off My Laptop: Physical Side-channel Key-extraction Attacks on PCs[J]. Journal of Cryptographic Engineering, 2015, 5(2): 95-112.
|
| [16] |
黑客与极客.中国教授在BlackHat 现场演示破解SIM 卡AES-128 加密[EB/OL]. , 2015-8-8.
|
| [17] |
BIHAM E,SHAMIR A.Power Analysis of the Key Scheduling of the AES Candidates[EB/OL] .,2017-4-15.
|
| [18] |
GIERLICHS B, BATINA L, CLAVIER C, et al. Susceptibility of eSTREAM Candidates Towards Side Channel analysis[EB/OL]. 2017-4-15.
|
| [19] |
FIPS PUB 140-2.Security Requirements for Cryptographic Modules[EB/OL]..
|
| [20] |
YAMADA A.A Generalization of ISO/IEC 24761 to Enhance Remote Authentication with Trusted Product at Claimant[C] // Springer . 30th IFIP TC 11 International Conference, SEC 2015, May 26-28, 2015,Hamburg, Germany. Berlin, Heidelberg:Springer, 2015: 145-158.
|
| [21] |
GM/T 0028-2014 密码模块安全技术要求[S]M/T 0028-2014 密码模块安全技术要求[S].北京:中国电力出版社,2015.
|
| [22] |
GENKIN D, SHAMIR A, TROMER E.RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis[C] // CRYPTO 2014. 34th Annual Cryptology Conference, August 17-21, 2014 ,Santa Barbara, CA, USA. Berlin, Heidelberg:Springer, 2014: 444-461.
|
| [23] |
GENKIN D, PACHMANOV L, PIPMAN I, et al.Stealing Keys from PCs Using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation[C] //CHES 2015. Cryptographic Hardware and Embedded Systems 7th International Workshop, September 13-16, 2015, Saint-Malo, France. Berlin, Heidelberg:Springer,2015: 207-228.
|
| [24] |
DPA Contest. DPA Contest V4.2竞赛结果 [EB/OL]..
|