信息网络安全 ›› 2021, Vol. 21 ›› Issue (4): 39-48.doi: 10.3969/j.issn.1671-1122.2021.04.005
基于ARF的Tor网站指纹识别技术
- 中国人民公安大学信息网络安全学院,北京 100076
-
收稿日期:2020-11-03出版日期:2021-04-10发布日期:2021-05-14 -
通讯作者:王腾飞 E-mail:2018211264@stu.ppsuc.edu.cn -
作者简介:蔡满春(1975—),男,河北,副教授,博士,主要研究方向为密码学、网络安全|王腾飞(1996—),男,河南,硕士研究生,主要研究方向为网络安全、匿名网络|岳婷(1996—),女,四川,硕士研究生,主要研究方向为恶意代码、密码学|芦天亮(1985—),男,河北,副教授,博士,主要研究方向为恶意代码、网络安全。 -
基金资助:“十三五”国家密码发展基金(MMJJ20180108);中国人民公安大学2019年基本科研业务费重大项目(2019JKF108)
ARF-based Tor Website Fingerprint Recognition Technology
CAI Manchun, WANG Tengfei( ), YUE Ting, LU Tianliang
), YUE Ting, LU Tianliang
- Department of Information Cyber Security, People’s Public Security University of China, Beijing 100076, China
-
Received:2020-11-03Online:2021-04-10Published:2021-05-14 -
Contact:WANG Tengfei E-mail:2018211264@stu.ppsuc.edu.cn
摘要:
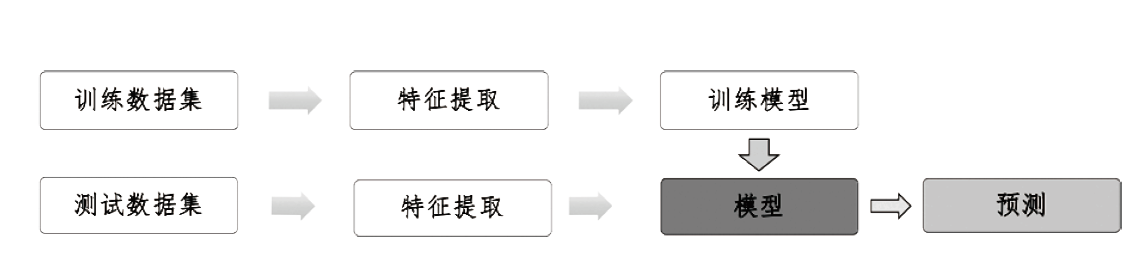
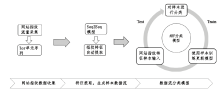
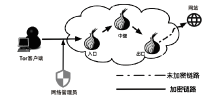
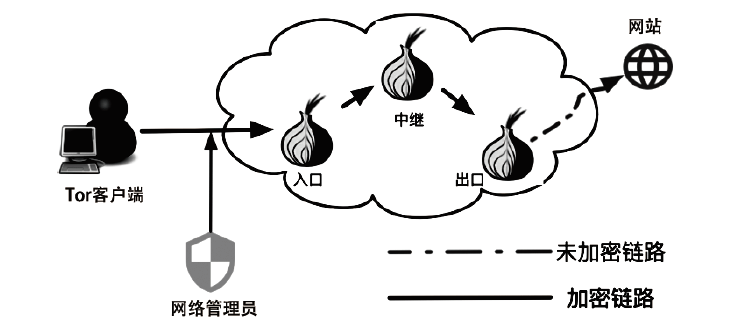
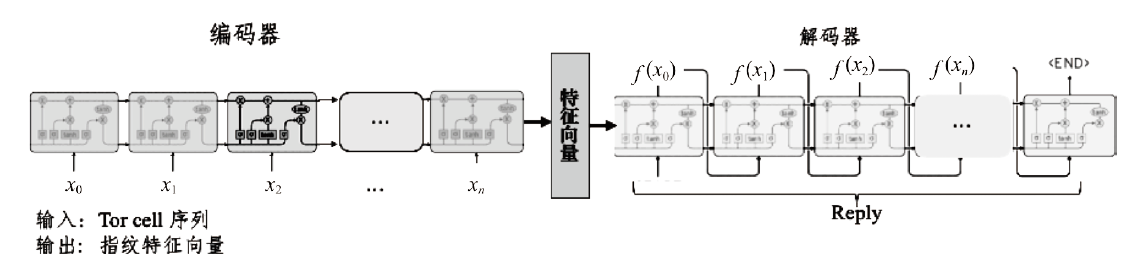
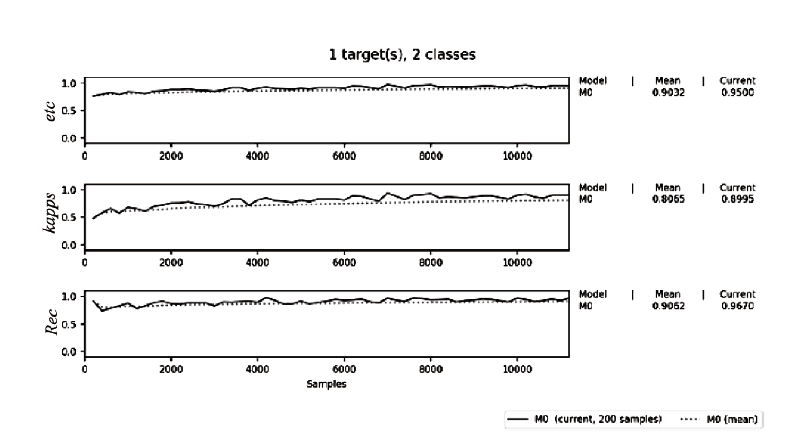
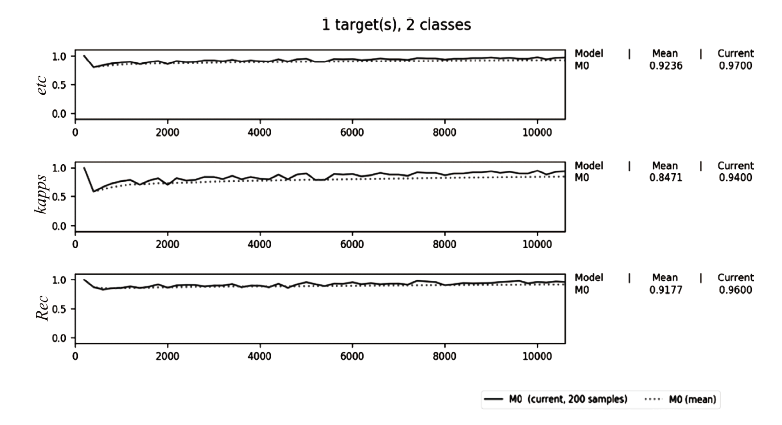
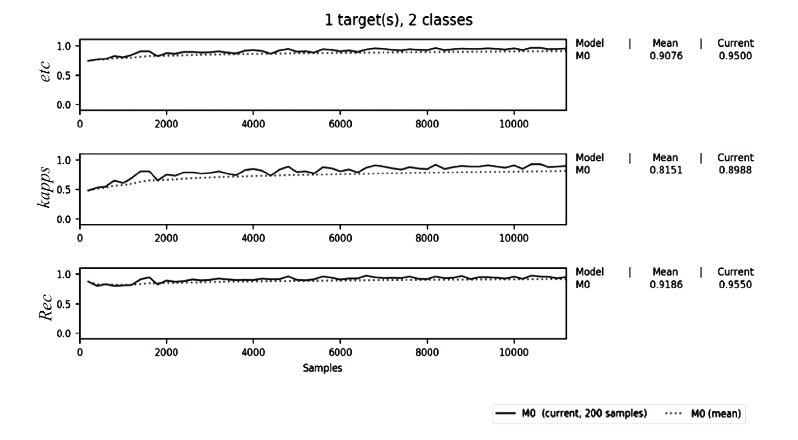
不法分子通过Tor等匿名通信系统构建暗网隐匿其不法行为,给网络监管带来了严峻挑战。网站指纹识别技术能根据加密流量来推测用户访问的站点,是一种有效的监管手段。已有的网站指纹识别技术采用的多为基于批处理的静态模型,无法有效解决概念漂移问题。针对Tor网站指纹,文章提出一种基于自适应随机森林(ARF)算法的动态网站指纹识别模型。模型使用自适应随机森林算法作为分类器,支持手工特征以及自动特征两种输入,能够根据特征流动态更新分类器模型,实现网站指纹的在线分类识别。实验结果表明,基于ARF的动态网站指纹识别模型检测能力优于已有的多种网站指纹识别方法,并能够有效解决已有模型存在的概念漂移问题。
中图分类号:
引用本文
蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48.
CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology[J]. Netinfo Security, 2021, 21(4): 39-48.
| [1] | SHI Y, MATSUURA K. Fingerprinting Attack on the Tor Anonymity System[C]// Springer. International Conference on Information and Communications Security(ICICS), December 14-17, 2009, Beijing, China. Heidelberg: Springer, 2009: 425-438. |
| [2] | JUAREZ M, AFROZ S, ACAR G, et al. A Critical Evaluation of Website Fingerprinting Attacks[C]// ACM. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale Arizona USA. New York: Association for Computing Machinery, 2014: 263-274. |
| [3] | DEY R, SALEM F M. Gate-variants of Gated Recurrent Unit (GRU) Neural Networks[C]// IEEE. 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), August 6, 2017, Medford, MA, United States. New York: IEEE, 2017: 1597-1600. |
| [4] | BHAT S, LU D, KWON A, et al. Var-cnn: A Data-efficient Website Fingerprinting Attack Based on Deep Learning[J]. Proceedings on Privacy Enhancing Technologies, 2019,19(4):292-310. |
| [5] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19, 2018, Toronto Canada. New York: Association for Computing Machiner, 2018: 1928-1943. |
| [6] | HINTZ A. Fingerprinting Websites Using Traffic Analysis[EB/OL]. https://link.springer.com/chapter/10.1007/3-540-36467-6_13, 2020-10-08. |
| [7] | LU Liming, CHANG E C, CHAN M C. Website Fingerprinting and Identification Using Ordered Feature Sequences[C]// Springer. European Symposium on Research in Computer Security. September 20-22, 2010, Athens, Greece. Heidelberg: Springer, 2010: 199-214. |
| [8] | HERRMANN D, WENDOLSKY R, FEDERRATH H. Website Fingerprinting: Attacking Popular Privacy Enhancing Technologies with the Multinomial Naïve-bayes Classifier[C]// ACM. Proceedings of the 2009 ACM Workshop on Cloud Computing Security, November 13-15, 2009, Chicago Illinois, USA. New York: Association for Computing Machinery, 2009: 31-42. |
| [9] | PANCHENKO A, NIESSEN L, ZINNEN A, et al. Website Fingerprinting in Onion Routing Based Anonymization Networks[C]// ACM. Proceedings of the 10th Annual ACM Workshop on Privacy in the Electronic Society. October 15-17, 2011, Chicago Illinois, USA. New York: Association for Computing Machinery, 2011: 103-114. |
| [10] | CAI Xiang, ZHANG Xincheng, JOSHI B, et al. Touching From a Distance: Website Fingerprinting Attacks and Defenses[C]// ACM. Proceedings of the 2012 ACM Conference on Computer and Communications Security. October 7-9, 2012, Raleigh North Carolina, USA. New York: Association for Computing Machinery, 2012: 605-616. |
| [11] | WANG Tao, CAI Xiang, NITHYANAND, et al. Effective Attacks and Provable Defenses against Website Fingerprinting[C]// USENIX. Usenix Conference on Security Symposium, August 16-18, 2014, San Diego, Berkeley. New York: USENIX Association, 2014: 143-157. |
| [12] | RIMMER V, PREUVENEERS D, JUAREZ M, et al. Automated Website Fingerprinting through Deep Learning[EB/OL]. https://arxiv.org/pdf/1708.06376.pdf, 2020-10-02. |
| [13] | RAHMAN M S, SIRINAM P, MATHEWS N, et al. Tik-Tok: The Utility of Packet Timing in Website Fingerprinting Attacks[J]. Proceedings on Privacy Enhancing Technologies, 2020,20(3):5-24. |
| [14] | HE Xiaomin, WANG Jin, HE Yueying, et al. A Deep Learning Approach for Website Fingerprinting Attack[C]// IEEE. 2018 IEEE 4th International Conference on Computer and Communications (ICCC), December 10, 2018, Chengdu, China. New York: IEEE, 2018: 1419-1423. |
| [15] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19 ,2018, Toronto, Canada. New York: Association for Computing Machiner, 2018: 1928-1943. |
| [16] | MA Chencheng, DU Xuehui, CAO Lifeng, et al. Burst-analysis Website Fingerprinting Attack Based on Deep Neural Network[J]. Journal of Computer Research and Development, 2020,57(4):746-766. |
| 马陈城, 杜学绘, 曹利峰, 等. 基于深度神经网络burst特征分析的网站指纹攻击方法[J]. 计算机研究与发展, 2020,57(4):746-766. | |
| [17] | WANG Xudong, YU Xiangzhan, ZHANG Hongli. Research on Traffic Identification Technology for Unknown Protocols[J]. Netinfo Security, 2019,19(10):74-83. |
| 王旭东, 余翔湛, 张宏莉. 面向未知协议的流量识别技术研究[J]. 信息网络安全, 2019,19(10):74-83. | |
| [18] | ATTARIAN R, ABDI L, HASHEMI S. AdaWFPA: Adaptive Online Website Fingerprinting Attack for Tor Anonymous Network: A Stream-wise Paradigm[J]. Computer Communications, 2019,19(148):74-85. |
| [19] | BIFET A, READ J, PFAHRINGER B, et al. CD-MOA: Change Detection Framework for Massive Online Analysis[C]// Springer. International Symposium on Intelligent Data Analysis, October 17-19, 2013, London, England. Heidelberg: Springer, 2013: 92-103. |
| [20] | WANG Tao, GOLDBERG I. Improved Website Fingerprinting on Tor[C]// ACM. Proceedings of the 12th ACM Workshop on Workshop on Privacy in the Electronic Society, November 5-7, 2013, Berlin, Germany. New York: Association for Computing Machiner, 2013: 201-212. |
| [21] |
GOMES H M, BIFET A, READ J, et al. Adaptive Random Forests for Evolving Data Stream Classification[J]. Machine Learning, 2017,106(9-10):1469-1495.
doi: 10.1007/s10994-017-5642-8 URL |
| [22] |
COHEN J. A Coefficient of Agreement for Nominal Scales[J]. Educational and Psychological Measurement, 1960,20(1):37-46.
doi: 10.1177/001316446002000104 URL |
| [23] | MONTIEL J, READ J, BIFET A, et al. Scikit-multiflow: A Multi-output Streaming Framework[J]. The Journal of Machine Learning Research, 2018,19(1):2915-2914. |
| [24] | ALEXA. Alexa-actionable Analytics for the Web[EB/OL]. http://www.alexa.com, 2020-10-02. |
| [25] | JUAREZ M. Tor Browser Crawler[EB/OL]. https://github.com/webfp/tor-browser-crawler, 2020-10-02. |
| [26] | HAYES J, DANEZIS G. K-fingerprinting: A Robust Scalable Website Fingerprinting Technique[EB/OL]. https://www.usenix.org/system/files/conference/usenixsecurity16/sec16_paper_hayes.pdf, 2020-10-02. |
| [1] | 金志刚, 王新建, 李根, 岳顺民. 融合攻击图和博弈模型的网络防御策略生成方法[J]. 信息网络安全, 2021, 21(1): 1-9. |
| [2] | 刘大恒, 李红灵. QR码网络钓鱼检测研究[J]. 信息网络安全, 2020, 20(9): 42-46. |
| [3] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [4] | 毕亲波, 赵呈东. 基于STRIDE-LM的5G网络安全威胁建模研究与应用[J]. 信息网络安全, 2020, 20(9): 72-76. |
| [5] | 来疆亮, 侯一凡, 卢旭明. 基于信息度量和损耗的网络安全系统综合效能分析研究[J]. 信息网络安全, 2020, 20(8): 81-88. |
| [6] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [7] | 孟相如, 徐江, 康巧燕, 韩晓阳. 基于熵权VIKOR的安全虚拟网络映射算法[J]. 信息网络安全, 2020, 20(5): 21-28. |
| [8] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [9] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [10] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [11] | 郭启全, 张海霞. 关键信息基础设施安全保护技术体系[J]. 信息网络安全, 2020, 20(11): 1-9. |
| [12] | 顾兆军, 郝锦涛, 周景贤. 基于改进双线性卷积神经网络的恶意网络流量分类算法[J]. 信息网络安全, 2020, 20(10): 67-74. |
| [13] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [14] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [15] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||