信息网络安全 ›› 2019, Vol. 19 ›› Issue (12): 22-28.doi: 10.3969/j.issn.1671-1122.2019.12.003
一种抗御SYN Flood攻击的采样信息路由评价选择方法
- 1.天津大学电气自动化与信息工程学院,天津 300072
2.天津市应急管理局消防救援总队,天津 300090
-
收稿日期:2019-07-15出版日期:2019-12-10发布日期:2020-05-11 -
作者简介:作者简介:金杉(1982—),男,天津,工程师,博士,主要研究方向为信息安全、无线传感器网络、信息系统、人工智能;金志刚(1972—),男,上海,教授,博士,主要研究方向为水下传感器网络、网络系统性能评价、下一代宽带无线通信系统、网络管理与安全;李根(1984—),男,天津,工程师,博士,主要研究方向为车联网、网络安全与区块链。
-
基金资助:国家自然科学基金[61571318];海南省重点研发计划[ZDYF2018006];博士后科学基金面上资助项目[2016M621076]
A Routing Evaluation and Selection Method with Sampling Information for Resisting SYN Flood Attack
Shan JIN1,2, Zhigang JIN1, Gen LI1( )
)
- 1. School of Electronic and Information Engineering, Tianjin University, Tianjin 300072, China
2. Fire and Rescue Crops, Bureau of Emergency Management of Tianjin, Tianjin 300090, China
-
Received:2019-07-15Online:2019-12-10Published:2020-05-11
摘要:
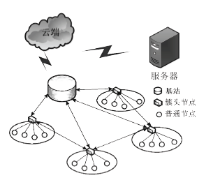
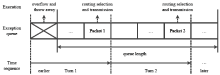
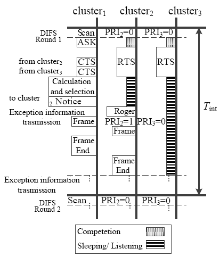
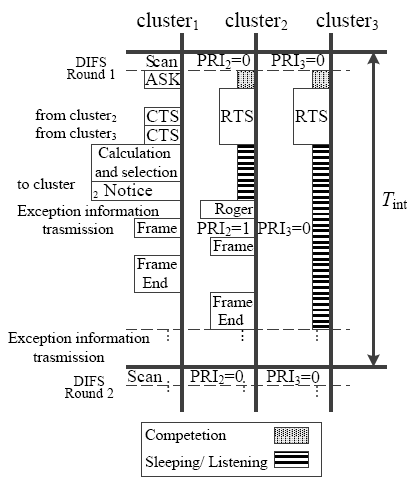
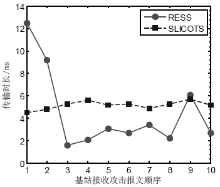
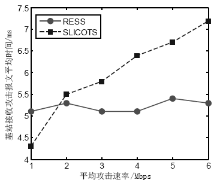
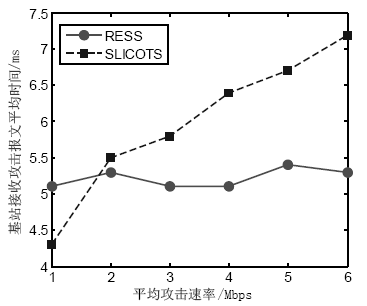
针对SYN Flood攻击出现在无线传感器网络中,易造成相对固定路由上的簇头节点过快耗尽死亡的问题,文章提出了抗御SYN Flood攻击的采样信息路由评价选择方法。该方法针对SYN Flood攻击利用某一底层感知节点频繁向其所在簇头发送大量SYN请求报文经过相对固定的链路上各簇头传输至云端服务器的情况,在网络部署时即建立节点ID与密钥配对关系,当ID被伪装时可以快速识别攻击节点。在攻击节点所在簇的簇头设立异常缓存,定期采样传输SYN请求报文,并设计了多维度评价的路由逐跳选择机制,选取最优相邻簇头作为下一跳的对象,从而逐跳选定了临时路由。实验证明,该方法在抗御SYN Flood攻击、稳定网络传输压力等方面效果显著。
中图分类号:
引用本文
金杉, 金志刚, 李根. 一种抗御SYN Flood攻击的采样信息路由评价选择方法[J]. 信息网络安全, 2019, 19(12): 22-28.
Shan JIN, Zhigang JIN, Gen LI. A Routing Evaluation and Selection Method with Sampling Information for Resisting SYN Flood Attack[J]. Netinfo Security, 2019, 19(12): 22-28.
| [1] | XIAO Ya, FAN Zhijie, LAN Julong, et al.Discovery Method for Distributed Denial-of-Service Attack Behavior in SDNs Using a Feature-Pattern Graph Model[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 38(2): 1195-1208. |
| [2] | LIU Yifan, ZHAO Bo, ZHAO Pengyuan, et al.A Survey: Typical Security Issues of Software-Defined Networking[J]. China Communications, 2019, 16(7): 13-31. |
| [3] | LIU Zhengpeng, HE Yupeng, WANG Wensheng, et al.DDoS Attack Detection Scheme Based on Entropy and PSO-BP Neural Network in SDN[J]. China Communications, 2019, 16(7): 144-155. |
| [4] | LI Saifei, CUI Yunhe, NI Yongfeng, et al.An Effective SDN Controller Scheduling Method to Defence DDoS Attacks[J]. Chinese Journal of Electronics, 2019, 28(2): 404-407. |
| [5] | CHEN Xingshu, HUA Qiang, WANG Yitong, et al.Research on Low-rate DDoS Attack of SDN Network in Cloud Environment[J]. Journal on Communications, 2019, 40(6): 210-222. |
| 陈兴蜀,滑强,王毅桐,等.云环境下SDN网络低速率DDoS攻击的研究[J].通信学报,2019,40(6):210-222. | |
| [6] | GUPTA B B, BADVE O P.Taxonomy of DoS and DDoS Attacks and Desirable Defense Mechanism in a Cloud Computing Environment[J]. Neural Computing and Applications, 2017, 28(12): 3655-3682. |
| [7] | AMJAD M,MITHUN M,SYED H A, et al.NBC-MAIDS: Naïve Bayesian Classification Technique in Multi-agent System-enriched IDS for Securing IoT against DDoS Attacks[J]. The Journal of Supercomputing, 2018, 74(10): 5156-5170. |
| [8] | SEMERCI M, CEMGIL A T, SANKUR B.An Intelligent Cyber Security System Against DDoS Attacks in SIP Networks[J]. Computer Networks, 2018, 136(5): 137-154. |
| [9] | BEHAL S, KUMAR K.Detection of DDoS Attacks and Flash Events Using Novel Information Theory Metrics[J]. Computer Networks, 2017, 116(4): 96-110. |
| [10] | ZHANG Long, WANG Jinsong.DDoS Attack Detection Model Based on Information Entropy and DNN in SDN[J]. Journal of Computer Research and Development, 2019, 56(5): 909-918. |
| 张龙,王劲松. SDN中基于信息熵与DNN的DDoS攻击检测模型[J].计算机研究与发展,2019,56(5):909-918. | |
| [11] | QIAN Hongyan, XUE Hao, CHEN Ming.UDM: NFV-based Prevention Mechanism against DDoS Attack on SDN Controller[J]. Journal on Communications, 2019, 40(3): 116-124. |
| 钱红燕,薛昊,陈鸣. UDM:基于NFV的防止DDoS攻击SDN控制器的机制[J].通信学报,2019,40(3):116-124. | |
| [12] | BERTINO E, ISLAM N.Botnets and Internet of Things Security[J]. Computer, 2017, 50(2): 76-79. |
| [13] | WANG K, DU M, MAHARJAN S, et al.Strategic Honeypot Game Model for Distributed Denial of Service Attacks in the Smart Grid[J]. IEEE Transactions on Smart Grid, 2017, 8(5): 2474-2482. |
| [14] | LI Chuanhuang, WU Yan, QIAN Zhengzhe, et al.DDoS Attack Detection and Defense Based on Hybrid Deep Learning Model in SDN[J]. Journal on Communications, 2018, 39(7): 176-187. |
| 李传煌,吴艳,钱正哲,等. SDN 下基于深度学习混合模型的DDoS 攻击检测与防御[J].通信学报,2018,39(7):176-187. | |
| [15] | TIAN Junfeng, QI Liuling.DDoS Attack Detection Method Based on Conditional Entropy and GHSOM in SDN[J]. Journal on Communications, 2019, 39(8): 140-149. |
| 田俊峰,齐鎏岭. SDN中基于条件熵和GHSOM的DDoS攻击检测方法[J].通信学报,2018,39(8):140-149. | |
| [16] | BAO Nan, ZUO Jiakuo, HU Han, et al.SDN Based Network Resource Selection Multi-objective Optimization Algorithm[J]. Journal on Communications, 2019, 40(2): 51-59. |
| 鲍楠,左加阔,胡晗,等.基于SDN的网络资源选择多目标优化算法[J].通信学报,2019,40(2):51-59. | |
| [17] | LIU Zhouzhou, LI Shining.Multi mobile Agent Itinerary Planning Based on Network Coverage and Multi-objective Discrete Social Spider Optimization Algorithm[J]. Journal on Communications, 2017, 38(6): 1-9. |
| 刘洲洲,李士宁.基于网络覆盖和多目标离散群集蜘蛛算法的多移动agent规划[J].通信学报,2017,38(6):1-9. | |
| [18] | HE Heng, HU Yan, ZHENG Lianghan, et al.Efficient DDoS Attack Detection and Prevention Scheme Based on SDN in Cloud Environment[J]. Journal on Communications, 2018, 39(4): 139-151. |
| 何亨,胡艳,郑良汉,等.云环境中基于SDN的高效DDoS攻击检测与防御方案[J].通信学报,2018,39(4):139-151. | |
| [19] | MA Ding, ZHUANG Lei, LAN Julong.Discrete Particle Swarm Optimization Based Multi-objective Service Path Constructing Algorithm[J]. Journal on Communications, 2017, 38(2): 94-105. |
| 马丁,庄雷,兰巨龙.基于离散粒子群优化的多目标服务路径构建算法[J].通信学报,2017,38(2):94-105. | |
| [20] | MOHAMMADI R, JAVIDAN R, CONTI M.SLICOTS: An SDN-Based Lightweight Countermeasure for TCP SYN Flooding Attacks[J]. IEEE Transactions on Network and Service Management, 2017, 14(6): 487-497. |
| [1] | 刘永磊, 金志刚, 郝琨, 张伟龙. 基于STRIDE和模糊综合评价法的移动支付系统风险评估[J]. 信息网络安全, 2020, 20(2): 49-56. |
| [2] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| [3] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [4] | 李辉, 倪时策, 肖佳, 赵天忠. 面向互联网在线视频评论的情感分类技术[J]. 信息网络安全, 2019, 19(5): 61-68. |
| [5] | 邓海莲, 刘宇靖, 葛一漩, 苏金树. 域间路由异常检测技术研究[J]. 信息网络安全, 2019, 19(11): 63-70. |
| [6] | 李本霞, 夏辉, 张三顺. 一种基于信任的组播路由协议[J]. 信息网络安全, 2019, 19(1): 59-67. |
| [7] | 李毅, 顾健, 顾铁军. 复杂网络安全产品质量评价体系的知识建模及其应用[J]. 信息网络安全, 2018, 18(9): 55-59. |
| [8] | 赵健, 王瑞, 李思其. 基于污点分析的智能家居漏洞挖掘技术研究[J]. 信息网络安全, 2018, 18(6): 36-44. |
| [9] | 朱毅, 陈兴蜀, 陈敬涵, 邵国林. 基于模糊综合评价模型的DNS健康度评估[J]. 信息网络安全, 2018, 18(4): 65-71. |
| [10] | 张三顺, 夏辉, 张公敬. 基于波动识别的可信组播路由协议[J]. 信息网络安全, 2018, 18(12): 72-81. |
| [11] | 赵旭, 黄光球, 崔艳鹏, 王明明. 基于改进选择算子的NIDS多媒体包多线程择危处理模型[J]. 信息网络安全, 2018, 18(10): 45-50. |
| [12] | 李剑锋, 刘渊, 张浩, 王晓锋. 面向IaaS云平台的路由转发优化研究与实现[J]. 信息网络安全, 2017, 17(9): 10-15. |
| [13] | 田庆宜, 郭弘. 毁损移动智能终端取证技术分级模型研究[J]. 信息网络安全, 2017, 17(2): 29-34. |
| [14] | 韩马剑. 路由器取证研究[J]. 信息网络安全, 2016, 16(9): 51-55. |
| [15] | 廖子渊, 陈明志, 邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全, 2016, 16(2): 33-39. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||