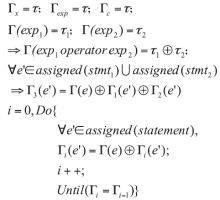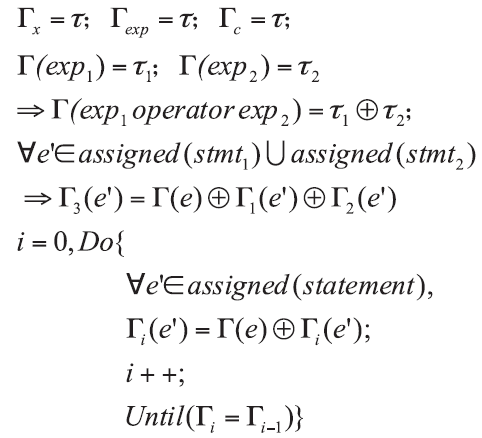信息网络安全 ›› 2018, Vol. 18 ›› Issue (6): 36-44.doi: 10.3969/j.issn.1671-1122.2018.06.005
基于污点分析的智能家居漏洞挖掘技术研究
- 1.西北大学信息科学与技术学院,陕西西安 710127
2.云南警察学院,云南昆明650223
-
收稿日期:2018-02-18出版日期:2018-06-15发布日期:2020-05-11 -
作者简介:作者简介:赵健(1973—),男,陕西,教授,博士,主要研究方向为信息安全、信号处理等;王瑞(1992—),男,山西,硕士研究生,主要研究方向为物联网安全、路由器安全;李思其(1974—),云南,女,讲师,硕士,主要研究方向为经济犯罪案件侦查、网络犯罪。
-
基金资助:国家自然科学基金[61572400]
Research on Smart Home Vulnerability Mining Technology Based on Taint Analysis
Jian ZHAO1, Rui WANG1( ), Siqi LI2
), Siqi LI2
- 1. School of Information Science and Technology, Northwest University, Xi’an Shannxi 710127, China;
2. Yunnan Police College, Kunming Yunnan 650223, China
-
Received:2018-02-18Online:2018-06-15Published:2020-05-11
摘要:
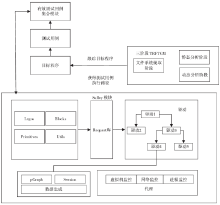
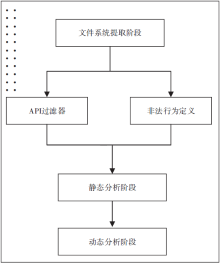
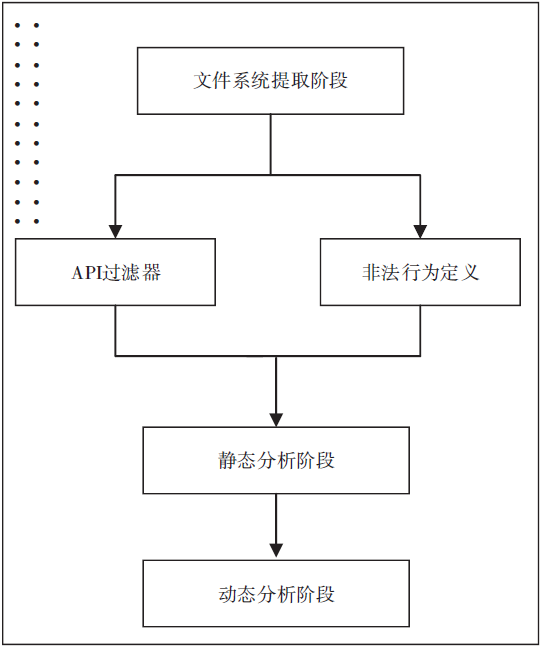
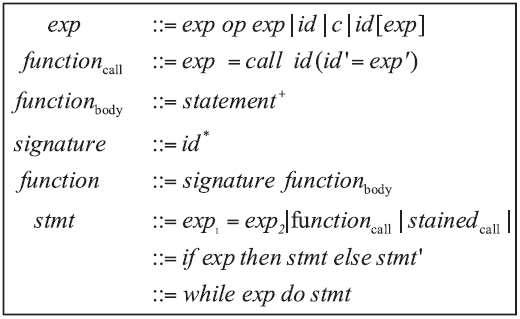
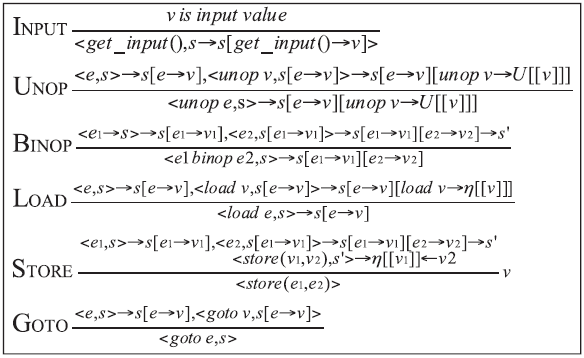
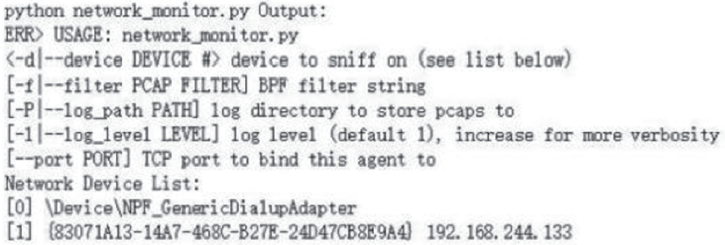
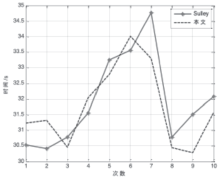
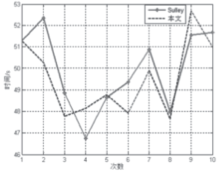
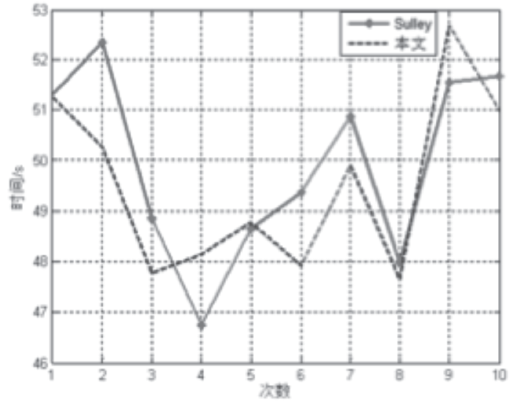
控制中心是整个智能家居的核心,可通过手机、平板等终端进行远程控制,一旦控制中心被攻击,攻击者便可获得绝大多数的家居控制权限,造成巨大破坏。目前,在智能家居系统中,控制中心多通过路由器采用无线通信技术与远程终端设备连接,实现对系统中的各种智能家居的操作和控制,路由器的安全性直接关系到整个智能家居系统和用户隐私生活的安全。文章提出了一种新颖的路由器漏洞挖掘方法,并基于Sulley将该方法实现为一种路由器漏洞检测框架,着重分析了路由器安全。结合污点分析技术,文章设计了一种针对路由器的三阶段模糊测试用例生成模块TPFTGM,指导Fuzzing过程中特定测试用例的生成,并将该框架运用于Dlink系列的路由器漏洞的挖掘。实验结果表明,利用该框架解决了Fuzzing中测试用例效率低下以及低代码路径覆盖率的问题。
中图分类号:
引用本文
赵健, 王瑞, 李思其. 基于污点分析的智能家居漏洞挖掘技术研究[J]. 信息网络安全, 2018, 18(6): 36-44.
Jian ZHAO, Rui WANG, Siqi LI. Research on Smart Home Vulnerability Mining Technology Based on Taint Analysis[J]. Netinfo Security, 2018, 18(6): 36-44.
| [1] | GUO Liang.The Present Situation and Future Tendency of the Development of Smart Home[J].Intelligent Building & Smart City, 2018(3):52-54. |
| 呙靓. 智能家居的发展现状及未来趋势[J].智能建筑与智慧城市, 2018(3):52-54. | |
| [2] | WANG Xuejiao.Brief Discussion on Security Issues of Smart Home System[J].Science Mosaic,2015(7):132-136. |
| 王雪娇. 浅谈智能家居系统的安全问题[J]. 科技广场, 2015(7):132-136. | |
| [3] | JIANG Fan,WEI Yixiang,ZHUANG Yan,et al.Research of Private Cloud Security’s Response to BlackMail Virus.Netinfo Security[J]. 2017, 17(8):83-88. |
| 蒋凡, 魏弋翔, 庄严,等. 安全私有云有效应对勒索病毒的原理分析[J]. 信息网络安全, 2017,17(8):83-88. | |
| [4] | MIZRAK A T, CHENG Y C, MARXULLO K, et al.Detecting and Isolating Malicious Routers[J]. IEEE Transactions on Dependable & Secure Computing, 2006, 3(3):230-244. |
| [5] | JUWAINI M, ALSAQOUR R,ABDELHAQ M,et al.A Review on WEP Wireless Security Protocol[J].Journal of Theoretical and Applied Information Technology, 2012,40(6):39-43. |
| [6] | LASHKARI A H, DANESH M M S, SAMADI B. A Survey on Wireless Security Protocols (WEP, WPA and WPA2/802.11i)[C]//IEEE. Computer Science and Information Technology,August 8-11,2009,Beijing, China. New York:IEEE, 2009:48-52. |
| [7] | ZHOU Jie.Research on Decoding WPA/WPA2-PSK with High Speed Based on GPU[D].Xi'an:Xidian University,2010. |
| 周洁. 基于GPU的WPA/WPA2-PSK高速破译方法研究[D]. 西安:西安电子科技大学, 2010. | |
| [8] | LI Liheng,ZHU Lingzhong,JU Ti.A Study on the Wireless Security of WPA in 802.11 Nwtwork[J].Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition),2004, 24(1):78-81. |
| 李立恒, 朱凌众, 居悌. 802.11无线网络WPA安全体系的研究[J]. 南京邮电大学学报(自然科学版), 2004, 24(1):78-81. | |
| [9] | ZISIADIS D, KOPSIDAS S, VARALIS A, et al.Enhancing WPS Security[C]//IEEE. Wireless Days,November 21-23,2012, Dublin, Ireland. New York:IEEE, 2013:1-3. |
| [10] | COSTIN A,ZARRAS A.Automated Dynamic Firmware Analysis at Scale: A Case Study on Embedded Web Interfaces[C]//ACM. Asia Conference on Computer and Communications Security,May 30-June 3, 2016, Xi'an, China. New York:ACM, 2016:437-448. |
| [11] | TAN Quanfu, JI Guozhen.Security Analysis of Access Router Firmware[J].Communications Technology,2018(1):200-204. |
| 谭全福,姬国珍. 接入路由器固件安全分析[J]. 通信技术,2018(1):200-204. | |
| [12] | DA Xiaowen,MAO Liwen,WU Mingjie,et al.Research on a Vulnerability Location Technology Based on Patch Matching and Static Taint Analysis[J].Netinfo Security,2017, 17(9):5-9. |
| 达小文,毛俐旻,吴明杰,等.一种基于补丁对比和静态污点分析的漏洞定位技术研究[J].信息网络安全,2017,17(9):5-9. | |
| [13] | XU Weiyang, LI Yao, TANG Yong, WANG Baosheng.Research on Cross-architecture Vulnerabilities Searching in Binary Executables[J].Netinfo Security,2017,17(9):21-25. |
| 徐威扬,李尧,唐勇,等.一种跨指令架构二进制漏洞搜索技术研究[J].信息网络安全,2017,17(9):21-25. | |
| [14] | WANG Minghao.The Security Analysis and Attacks Detection of OSPF Routing Protocol[C]//IEEE.International Conference on Intelligent Computation Technology and Automation,October 25-26, 2014,Changsha, China.New York:IEEE, 2015:836-839. |
| [15] | VENTRE G.Experimental Analysis of Attacks Against Intradomain Routing Protocols[M]. Nieuwe Hemweg:IOS Press, 2005. |
| [16] | SMITH B R, GARCIA-LUNA-ACEVES J J. Securing the Border Gateway Routing Protocol[C]//IEEE.Global Telecommunications Conference,November 18-28,London, UK.New York:IEEE, 1996:81-85. |
| [17] | KENT S, LYNN C, SEO K.Secure Border Gateway Protocol (S-BGP)[J].IEEE Journal on Selected Areas in Communications, 2000, 18(4) :582-592. |
| [18] | COSTIN A,ZARRAS A.Automated Dynamic Firmware Analysis at Scale: A Case Study on Embedded Web Interfaces[C]// ACM.ACM on Asia Conference on Computer and Communications Security,May 30-June 3, 2016,Xi'an,China.New York:ACM, 2016:437-448. |
| [19] | CUI A,COSTELLO M,STOLFO S J. When Firmware Modifications Attack: A Case Study of Embedded Exploitation[EB/OL].,2017-7-15. |
| [20] | ZADDACH J,BRUNO L,BALZAROTTI D, et al. Avatar: A Framework to Support Dynamic Security Analysis of Embedded Systems’ Firmwares[EB/OL].. |
| [21] | COSTIN A, ZADDACH J,FRANCILLON A, et al.A Large-scale Analysis of the Security of Embedded Firmwares[C]//USENIX. 23rd USENIX conference on Security Symposium ,August 20 - 22, 2014,San Diego,USA.Berkeley: USENIX,2014:95-110. |
| [22] | YAN S,WANG R,HAUSER C, et al. Firmalice-Automatic Detection of Authentication Bypass Vulnerabilities in Binary Firmware[EB/OL].,2017-7-15. |
| [23] | HU Chaojian, XUE Yibo, ZHAO Liang, et al.Backdoor Detection in Embedded System Firmware without File System[J].Journal on Communications, 2013(8):140-145. |
| 忽朝俭, 薛一波, 赵粮,等. 无文件系统嵌入式固件后门检测[J]. 通信学报, 2013(8):140-145. | |
| [24] | WANG Xiajing,HU Changzhen,MA Rui, et al.A Survey of the Key Technology of Binary Program Vulnerability Discovery[J].Netinfo Security, 2017,17(8):1-13. |
| 王夏菁, 胡昌振, 马锐,等. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017,17(8):1-13. | |
| [25] | LI Deng,YIN Qing,LIN Jian,et al.Firmware Vulnerability Detection in Embedded Device Based on Homology Analysis[J].Computer Engineering,2017, 43(1):72-78. |
| 李登, 尹青, 林键,等. 基于同源性分析的嵌入式设备固件漏洞检测[J]. 计算机工程, 2017, 43(1):72-78. | |
| [26] | SHI Ji, ZENG Zhaolong, YANG Congbao,et al.The Summary of Fuzzing Testing Technology[J].Netinfo Security,2014, 14(3):87-91. |
| 史记, 曾昭龙, 杨从保,等. Fuzzing测试技术综述[J]. 信息网络安全, 2014,14(3):87-91. | |
| [27] | ZHOU Yan.Extensible Framework for Static Vulnerability Detection Based on Taint Analysis[D].Nanjing:Nanjing University,2017. |
| 周严. 基于污点分析的静态漏洞检测可扩展框架[D].南京:南京大学, 2017 | |
| [28] | CUI Hualiang,LAN Yun,CUI Baojiang.Application of Dynamic Taints Analysis Technology in Vulnerability Detection of ActiveX Controls[J].Netinfo Security,2013, 13(12):16-19. |
| 崔化良, 兰芸, 崔宝江.动态污点分析技术在ActiveX控件漏洞挖掘上的应用[J]. 信息网络安全, 2013,13(12):16-19. |
| [1] | 文伟平, 李经纬, 焦英楠, 李海林. 一种基于随机探测算法和信息聚合的漏洞检测方法[J]. 信息网络安全, 2019, 19(1): 1-7. |
| [2] | 龚婉婉, 刘士兴, 冯婷婷. 基于无线传感器网络的智能家居监控平台设计[J]. 信息网络安全, 2015, 15(3): 79-83. |
| [3] | 文伟平, 郭荣华, 孟正, 柏皛. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全, 2015, 15(2): 7-8. |
| [4] | . 典型文档类CVE漏洞检测工具的研究与实现[J]. , 2014, 14(6): 18-. |
| [5] | . 基于代理模式的 SQL 注入漏洞检测技术研究[J]. , 2014, 14(11): 66-. |
| [6] | 潘峰;李涛;张电. 主动式漏洞检测与修复系统的设计与实现[J]. , 2013, 13(5): 0-0. |
| [7] | 宋超臣;黄俊强;王大萌;段志鸣. 计算机漏洞安全检测技术综述[J]. , 2012, 12(1): 0-0. |
| [8] | 宋海龄;文伟平. 一个典型的Web安全评测工具的分析与改进[J]. , 2011, 11(8): 0-0. |
| [9] | 方舟;黄俊强. 数据库安全测评通用模型的设计与实现[J]. , 2011, 11(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||