信息网络安全 ›› 2016, Vol. 16 ›› Issue (12): 28-33.doi: 10.3969/j.issn.1671-1122.2016.12.005
基于特征的网络漏洞态势感知方法研究
高川1, 严寒冰2, 贾子骁2
- 1.北京航空航天大学计算机学院,北京 100191
2.国家计算机网络应急技术处理协调中心,北京 100020
Research on the Method for Network Vulnerabilities Situational Awareness Based on the Features
Chuan GAO1, Hanbing YAN2, Zixiao JIA2
- 1. College of Computer, Beihang University, Beijing 100191, China
2. National Computer Network Emergency Response Technical Team/Coordination Center of China, Beijing 100020, China
摘要:
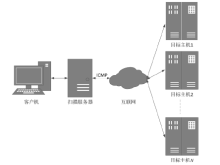
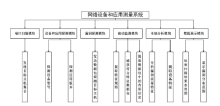
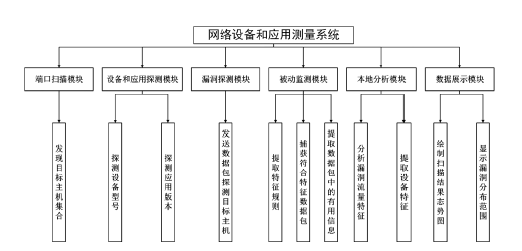
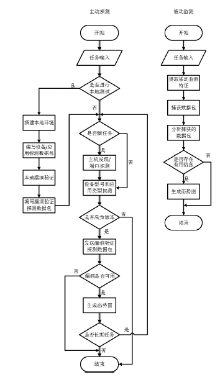
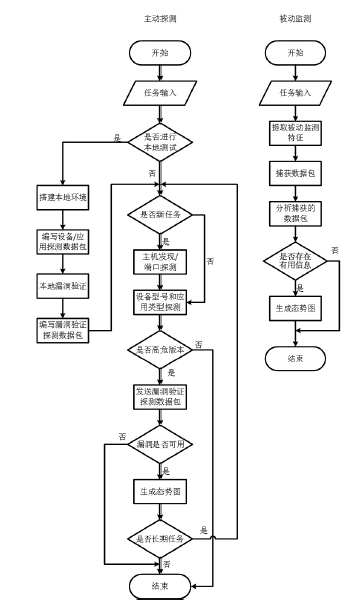
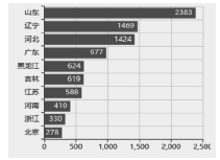
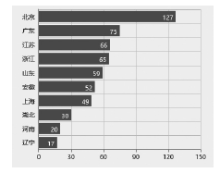
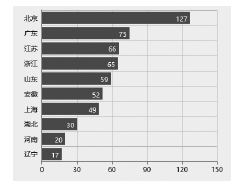
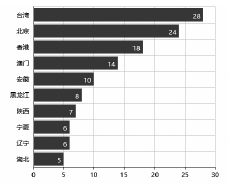
随着互联网规模的持续扩大,互联网安全问题日益严峻,互联网设备和应用的安全态势成为所有网络用户重视的内容。文章提出一种基于特征的互联网设备和应用的测量方法。首先,对设备和应用进行特征提取,采用主动探测和被动监测相结合的方法,得到设备和应用的信息。然后,对得到的信息进行分析,描绘互联网设备和应用的漏洞分布态势。文章对3种设备和应用进行测量,验证了该方法,探测了它们的漏洞分布情况。漏洞分布态势图可以帮助网络管理员有效理解互联网设备和应用的状态,及时发现漏洞并进行修补。
中图分类号: