信息网络安全 ›› 2025, Vol. 25 ›› Issue (10): 1523-1536.doi: 10.3969/j.issn.1671-1122.2025.10.004
TrustZone半虚拟化与容器化实现机制
- 1.武汉大学国家网络安全学院,武汉 430072
2.空天信息安全与可信计算教育部重点实验室,武汉 430072
-
收稿日期:2024-11-08出版日期:2025-10-10发布日期:2025-11-07 -
通讯作者:余发江 E-mail:fjyu@whu.edu.cn -
作者简介:余发江(1979—),男,重庆,副教授,博士,CCF会员,主要研究方向为系统安全、可信计算|王朝州(2000—),男,四川,硕士研究生,主要研究方向为系统安全 -
基金资助:国家自然科学基金(61772384)
Implementation Mechanism for TrustZone Paravirtualization and Containerization
YU Fajiang1,2( ), WANG Chaozhou1,2
), WANG Chaozhou1,2
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing, Ministry of Education, Wuhan 430072, China
-
Received:2024-11-08Online:2025-10-10Published:2025-11-07 -
Contact:YU Fajiang E-mail:fjyu@whu.edu.cn
摘要:
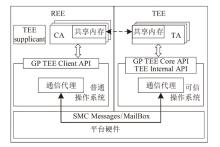
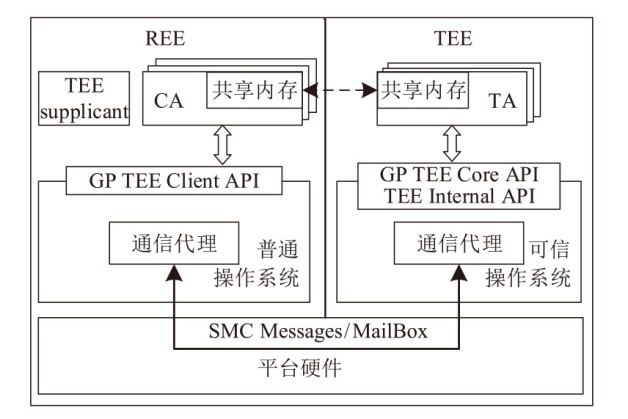
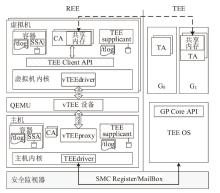
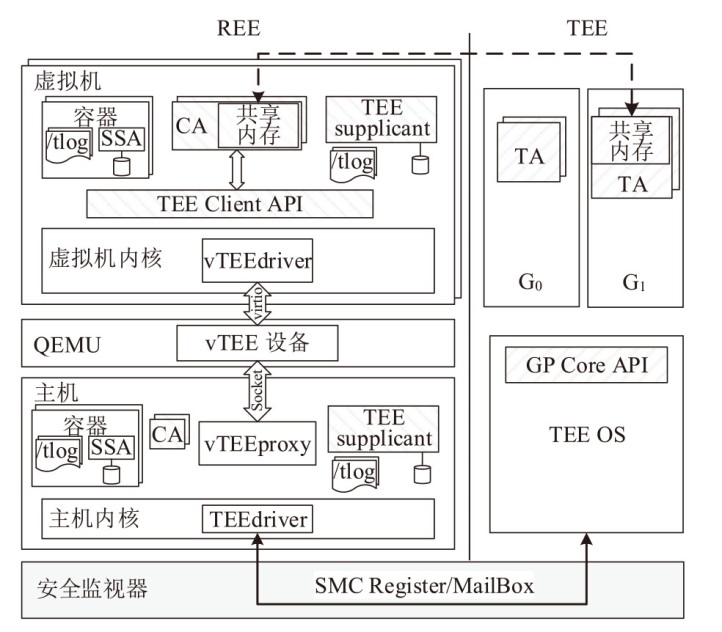
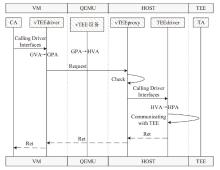
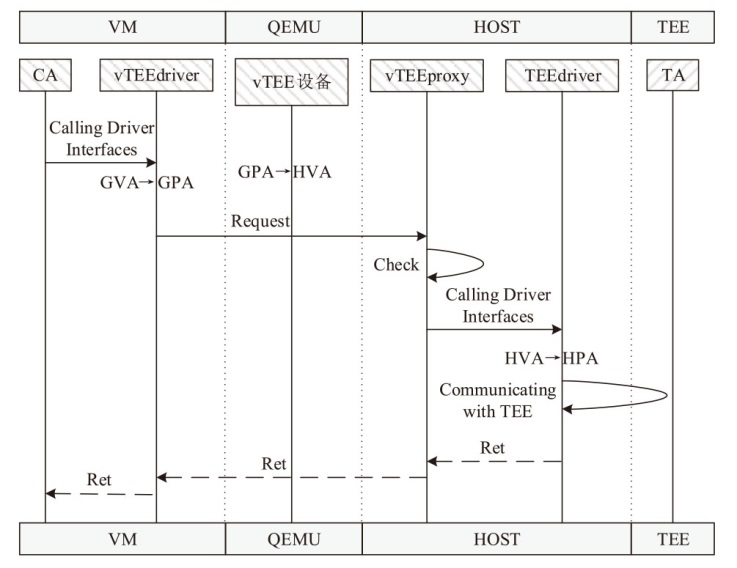
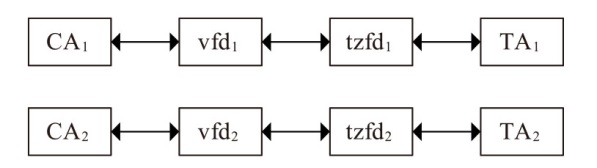
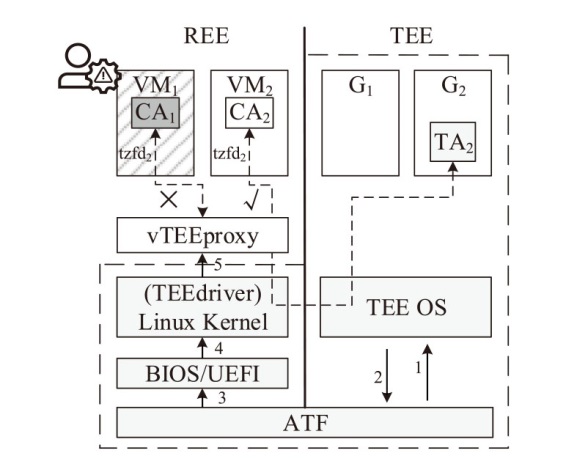
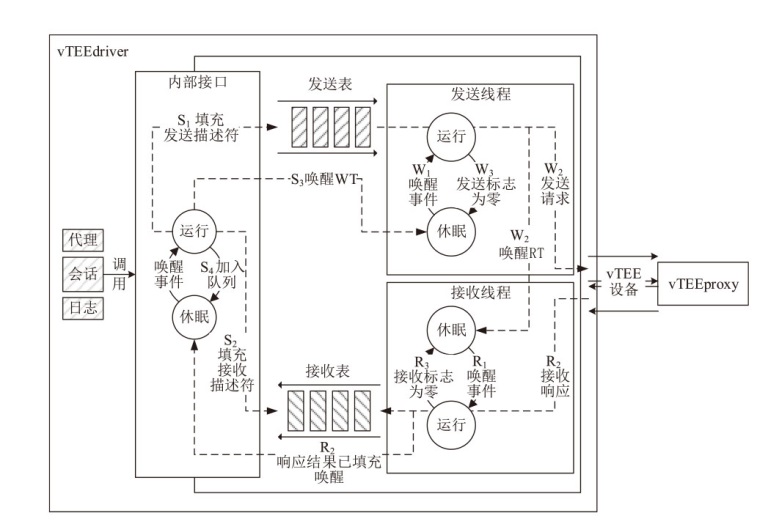
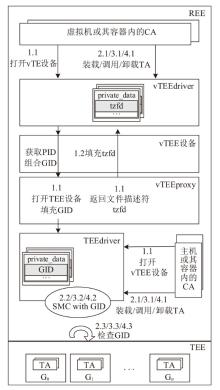
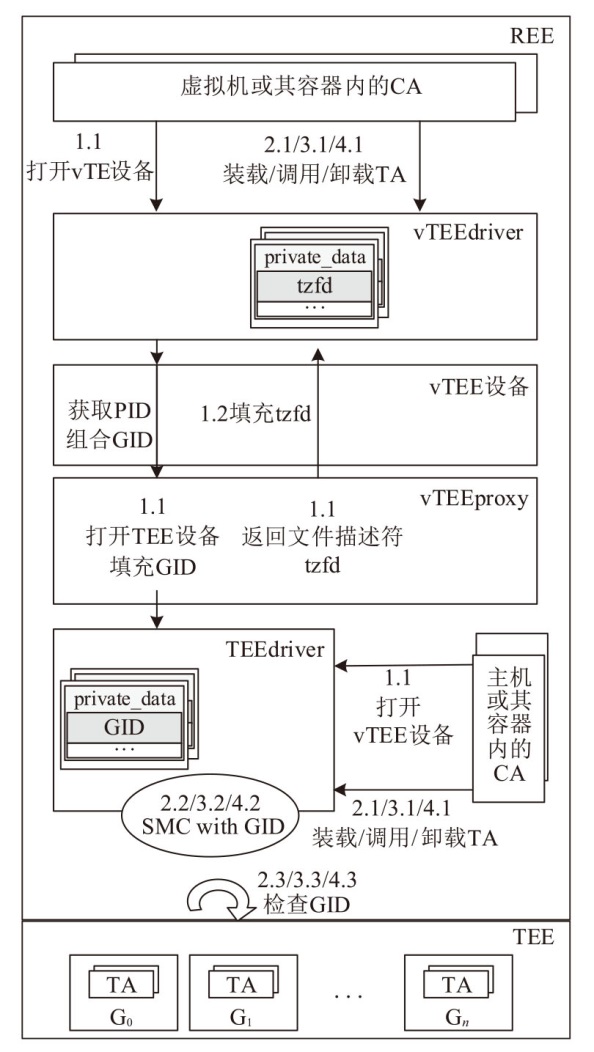
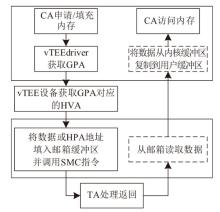
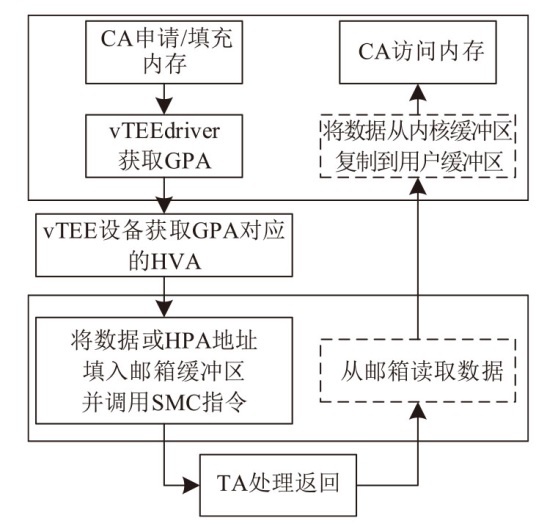
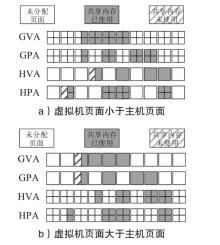
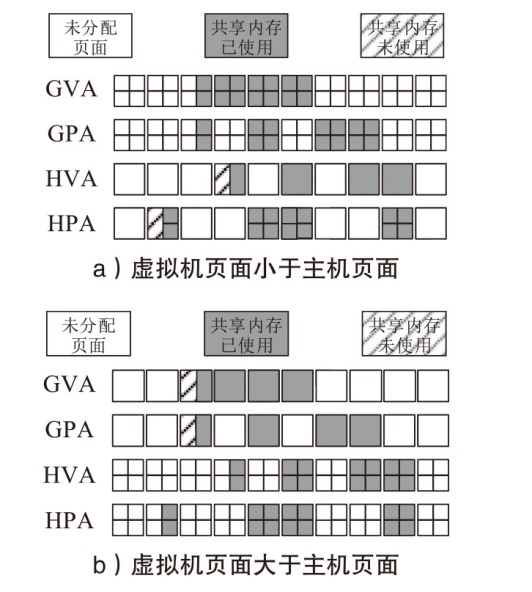
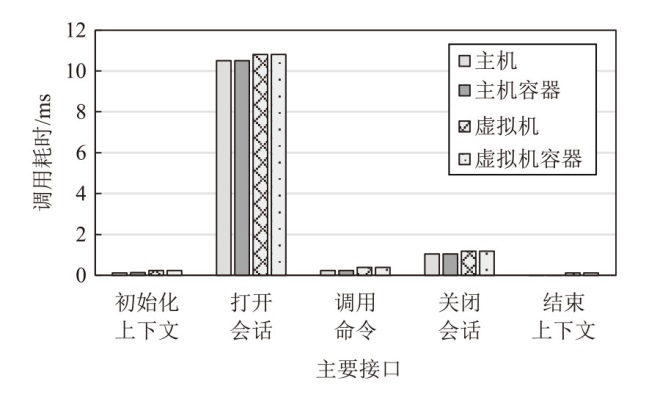
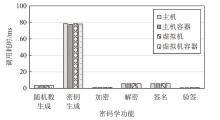
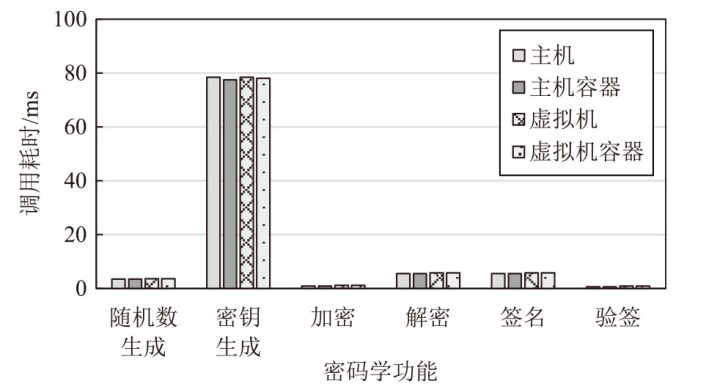
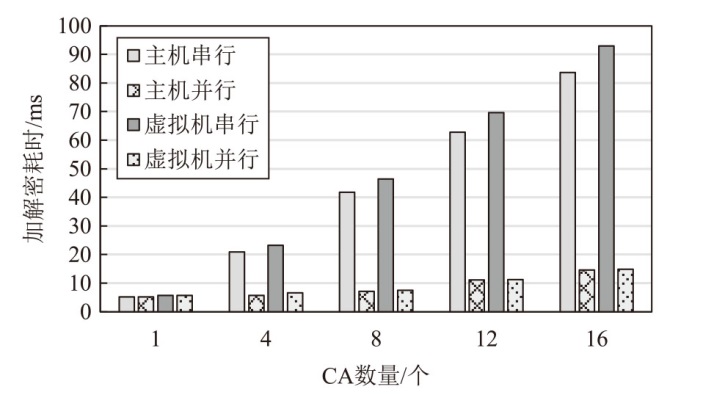
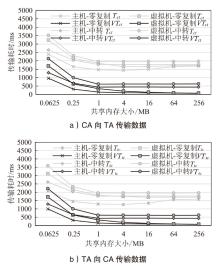
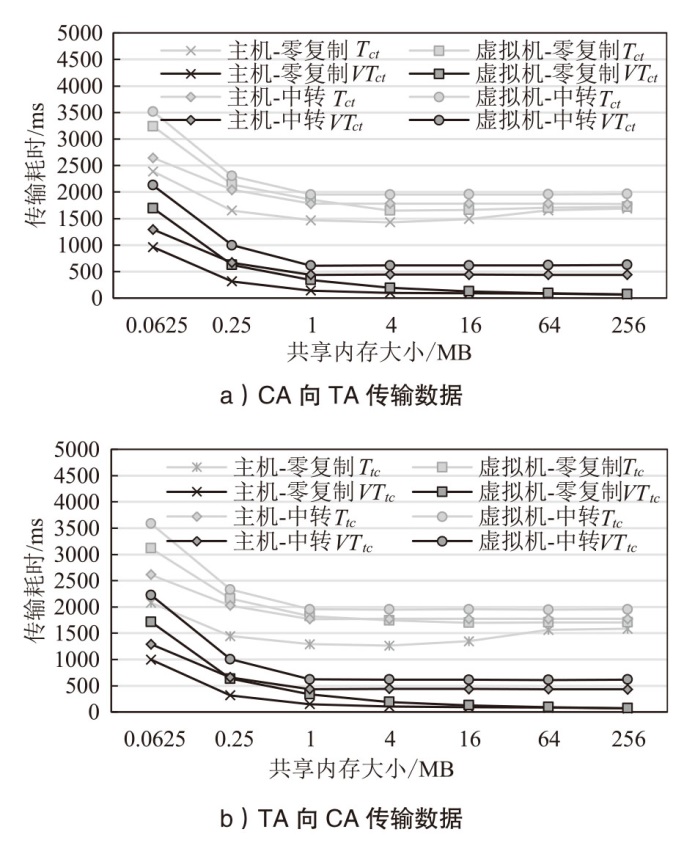
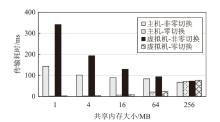
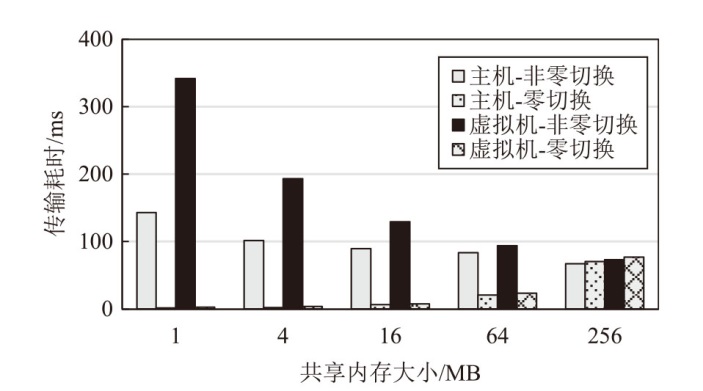
TrustZone广泛应用于移动平台,随着ARM CPU在云服务中大量部署,利用TrustZone增强虚拟机计算环境和数据的安全性需求日益凸显。但基础的TrustZone提供的硬件可信执行环境通常仅支持主机上的应用程序使用。为解决这一问题,文章提出一种TrustZone半虚拟化与容器化实现机制pvTEE,使虚拟机或容器中的客户能够高效、并行利用主机平台的可信执行环境运行可信应用。pvTEE通过前端驱动vTEEdriver、虚拟设备vTEE、主机代理程序vTEEproxy以及后端驱动TEEdriver,将虚拟机或容器内客户的调用请求转发至可信执行环境中的可信应用执行。主机、虚拟机和容器中的客户仅可调用自身场景的可信应用,无法访问其他应用。同时,主机、虚拟机及容器各自有独立的日志获取能力与安全存储服务。pvTEE基于ARMv8.2 CPU服务器、QEMU KVM虚拟机和Docker容器实现,实验结果表明,客户在虚拟机中调用可信应用完成一次RSA加解密操作,相比在主机场景中仅增加约6%的时间开销。
中图分类号:
引用本文
余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536.
YU Fajiang, WANG Chaozhou. Implementation Mechanism for TrustZone Paravirtualization and Containerization[J]. Netinfo Security, 2025, 25(10): 1523-1536.
| [1] | SABT M, ACHEMLAL M, BOUABDALLAH A. Trusted Execution Environment:What It is, and What It is Not[C]// IEEE. 2015 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2015: 57-64. |
| [2] | MCGILLION B, DETTENBORN T, NYMAN T, et al. Open-TEE: An Open Virtual Trusted Execution Environment[C]// IEEE. 2015 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2015: 400-407. |
| [3] |
MAYRHOFER R. An Architecture for Secure Mobile Devices[J]. Security and Communication Networks, 2015, 8(10): 1958-1970.
doi: 10.1002/sec.v8.10 URL |
| [4] | SANTOS N, RAJ H, SAROIU S, et al. Using ARM TrustZone to Build a Trusted Language Runtime for Mobile Applications[C]// ACM. The 19th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2014: 67-80. |
| [5] | PETTERSEN R, JOHANSEN H D, JOHANSEN D. Secure Edge Computing with ARM TrustZone[EB/OL]. (2017-01-01)[2024-08-03]. https://doi.org/10.5220/0006308601020109. |
| [6] | PIRKER M, SLAMANIG D. A Framework for Privacy-Preserving Mobile Payment on Security Enhanced ARM TrustZone Platforms[C]// IEEE. 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2012: 1155-1160. |
| [7] | COOIJMANS T, DERUITER J, POLL E. Analysis of Secure Key Storage Solutions on Android[C]// ACM. The 4th ACM Workshop on Security and Privacy in Smartphones & Mobile Devices. New York: ACM, 2014: 11-20. |
| [8] | ZHANG Yingjun, ZHAO Shijun, QIN Yu, et al. TrustTokenF: A Generic Security Framework for Mobile Two-Factor Authentication Using TrustZone[C]// IEEE. 2015 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2015: 41-48. |
| [9] |
JIAN Zhaolong, LU Ye, QIAO Youyang, et al. TSC-VEE: A TrustZone-Based Smart Contract Virtual Execution Environment[J]. IEEE Transactions on Parallel and Distributed Systems, 2023, 34(6): 1773-1788.
doi: 10.1109/TPDS.2023.3263882 URL |
| [10] |
LI Yuepeng, ZENG Deze, GU Lin, et al. PASTO: Enabling Secure and Efficient Task Offloading in TrustZone-Enabled Edge Clouds[J]. IEEE Transactions on Vehicular Technology, 2023, 72(6): 8234-8238.
doi: 10.1109/TVT.2023.3237204 URL |
| [11] | SIDDIQUI T, SIDDIQUI S A, KHAN N A. Comprehensive Analysis of Container Technology[C]// IEEE. 2019 4th International Conference on Information Systems and Computer Networks (ISCON). New York: IEEE, 2019: 218-223. |
| [12] | BRADY K, MOON S, NGUYEN T, et al. Docker Container Security in Cloud Computing[C]// IEEE. 2020 10th Annual Computing and Communication Workshop and Conference (CCWC). New York: IEEE, 2020: 975-980. |
| [13] | MATHER T, KUMARASWAMY S, LATIF S. Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance[M]. Sebastopol: O’Reilly Media, Inc., 2009. |
| [14] | RISTENPART T, TROMER E, SHACHAM H, et al. Hey, You, Get Off of My Cloud: Exploring Information Leakage in Third-Party Compute Clouds[C]// ACM. The 16th ACM Conference on Computer and Communications Security. New York: ACM, 2009: 199-212. |
| [15] | ZHAO Shixuan, LI Mengyuan, ZHANG Y Q, et al. vSGX: Virtualizing SGX Enclaves on AMD SEV[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 321-336. |
| [16] | NGABONZIZA B, MARTIN D, BAILEY A, et al. TrustZone Explained: Architectural Features and Use Cases[C]// IEEE. 2016 IEEE 2nd International Conference on Collaboration and Internet Computing (CIC). New York: IEEE, 2016: 445-451. |
| [17] | DEMIGHA O, LARGUET R. Hardware-Based Solutions for Trusted Cloud Computing[EB/OL]. (2021-04-01)[2024-08-03]. https://www.sciencedirect.com/science/article/pii/S0167404820303904. |
| [18] | GUAN Le, LIU Peng, XING Xinyu, et al. TrustShadow: Secure Execution of Unmodified Applications with ARM TrustZone[C]// ACM. The 15th Annual International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2017: 488-501. |
| [19] | BRITO T, DUARTE N O, SANTOS N. ARM TrustZone for Secure Image Processing on the Cloud[C]// IEEE. 2016 IEEE 35th Symposium on Reliable Distributed Systems Workshops (SRDSW). New York: IEEE, 2016: 37-42. |
| [20] | HUA Zhichao, GU Jinyu, XIA Yubin, et al. vTZ: Virtualizing ARM TrustZone[C]// USENIX. The 26th USENIX Security Symposium (USENIX Security 17). Berkeley: USENIX, 2017: 541-556. |
| [21] | HUA Zhichao, YU Yang, GU Jinyu, et al. TZ-Container: Protecting Container from Untrusted OS with ARM TrustZone[EB/OL]. (2021-08-19)[2024-08-03]. https://link.springer.com/article/10.1007/s11432-019-2707-6. |
| [22] | LI Dingji, MI Zeyu, XIA Yubin, et al. TwinVisor: Hardware-Isolated Confidential Virtual Machines for ARM[C]// ACM. The ACM SIGOPS 28th Symposium on Operating Systems Principles. New York: ACM, 2021: 638-654. |
| [23] | SUN He, SUN Kun, WANG Yuewu, et al. TrustICE: Hardware-Assisted Isolated Computing Environments on Mobile Devices[C]// IEEE. 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2015: 367-378. |
| [24] | LI Wenhao, XIA Yubin, LU Long, et al. TEEv: Virtualizing Trusted Execution Environments on Mobile Platforms[C]// ACM. The 15th ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments. New York: ACM, 2019: 2-16. |
| [25] |
KWON D, SEO J, CHO Y, et al. PrOS: Light-Weight Privatized Secure OSes in ARM TrustZone[J]. IEEE Transactions on Mobile Computing, 2020, 19(6): 1434-1447.
doi: 10.1109/TMC.7755 URL |
| [26] | ALVES T. TrustZone: Integrated Hardware and Software Security[J]. Information Quarterly, 2004(3): 18-24. |
| [27] | ZHU Qinyu, CHEN Quan, LIU Yichen, et al. Investigating TrustZone: A Comprehensive Analysis[EB/OL]. (2023-04-14)[2024-08-03]. https://onlinelibrary.wiley.com/doi/10.1155/2023/7369634. |
| [28] | BELLARD F. QEMU, a Fast and Portable Dynamic Translator[C]// USENIX. The Annual Conference on USENIX Annual Technical Conference (ATEC’05). Berkeley: USENIX, 2005: 41-46. |
| [29] | RUSSELL R. Virtio: Towards a De-Facto Standard for Virtual I/O Devices[J]. ACM SIGOPS Operating Systems Review, 2008, 42(5): 95-103. |
| [30] | GOLDENBERG D, KAGAN M, RAVID R, et al. Zero Copy Sockets Direct Protocol Over Infiniband-Preliminary Implementation and Performance Analysis[C]// IEEE. The 13th Symposium on High Performance Interconnects (HOTI’05). New York: IEEE, 2005: 128-137. |
| [31] | ZHANG Ning, SUN Kun, SHANDS D, et al. TruSense: Information Leakage from TrustZone[C]// IEEE. IEEE INFOCOM 2018-IEEE Conference on Computer Communications. New York: IEEE, 2018: 1097-1105. |
| [32] | KOU Zili, SINHA S, HE Wenjian, et al. Cache Side-Channel Attacks and Defenses of the Sliding Window Algorithm in TEEs[C]// IEEE. 2023 Design, Automation & Test in Europe Conference & Exhibition (DATE). New York: IEEE, 2023: 1-6. |
| [33] | LI Xupeng, LI Xuheng, DALL C, et al. Design and Verification of the ARM Confidential Compute Architecture[C]// USENIX. The 16th USENIX Symposium on Operating Systems Design and Implementation (OSDI’22). Berkeley: USENIX, 2022: 465-484. |
| [34] | FOX A C J, STOCKWELL G, XIONG Shale, et al. A Verification Methodology for the ARM® Confidential Computing Architecture: from a Secure Specification to Safe Implementations[J]. The ACM on Programming Languages, 2023, 7: 376-405. |
| [1] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [2] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [3] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [4] | 邢凌凯, 张健. 基于HPC的虚拟化平台异常检测技术研究与实现[J]. 信息网络安全, 2023, 23(10): 64-69. |
| [5] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [6] | 林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67. |
| [7] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [8] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [9] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [10] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [11] | 亢保元, 颉明明, 司林. 基于生物识别技术的多云服务器认证方案研究[J]. 信息网络安全, 2019, 19(6): 45-52. |
| [12] | 时向泉, 陶静, 赵宝康. 面向虚拟化环境的网络访问控制系统[J]. 信息网络安全, 2019, 19(10): 1-9. |
| [13] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [14] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [15] | 朱维军, 樊永文, 班绍桓. 动态虚拟MSISDN的拟态自动机模型与安全性验证方法[J]. 信息网络安全, 2018, 18(4): 15-22. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||